Client Secret Authentication
Client Secret Authentication
To use client secret authentication, ensure your Azure Service Principal has the required permissions to manage DNS records in your Azure DNS Zone.Prerequisites:
- Set up Azure and have an existing DNS Zone.
- An Azure Service Principal (App Registration) with a Client Secret.
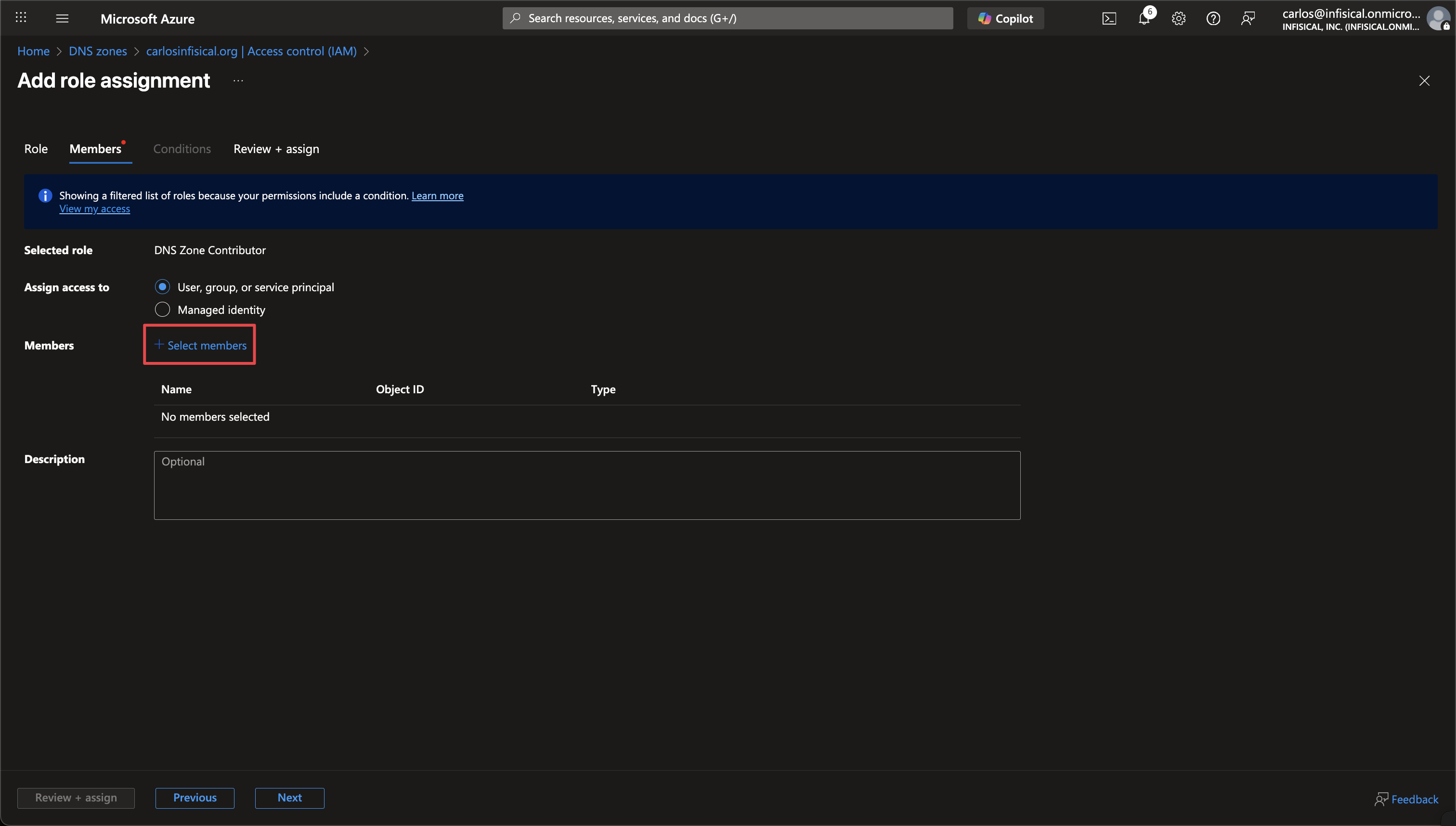
Navigate to your DNS Zone
In the Azure Portal, navigate to your DNS Zone that you want to use for ACME DNS validation. Click on Access control (IAM) in the left sidebar, then click Add > Add role assignment.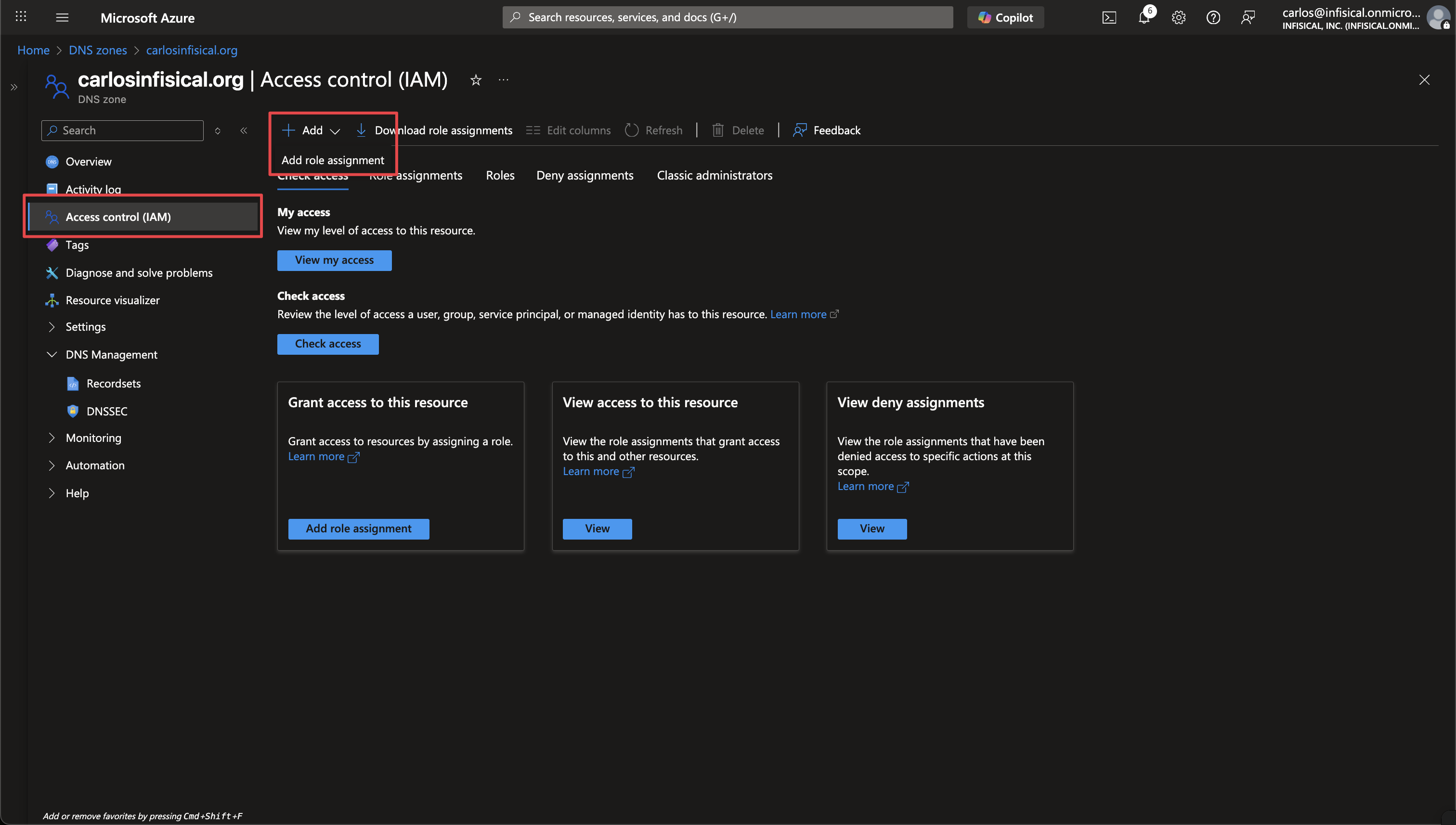

Assign DNS Zone Contributor Role
Search for and select the DNS Zone Contributor role, then click Next.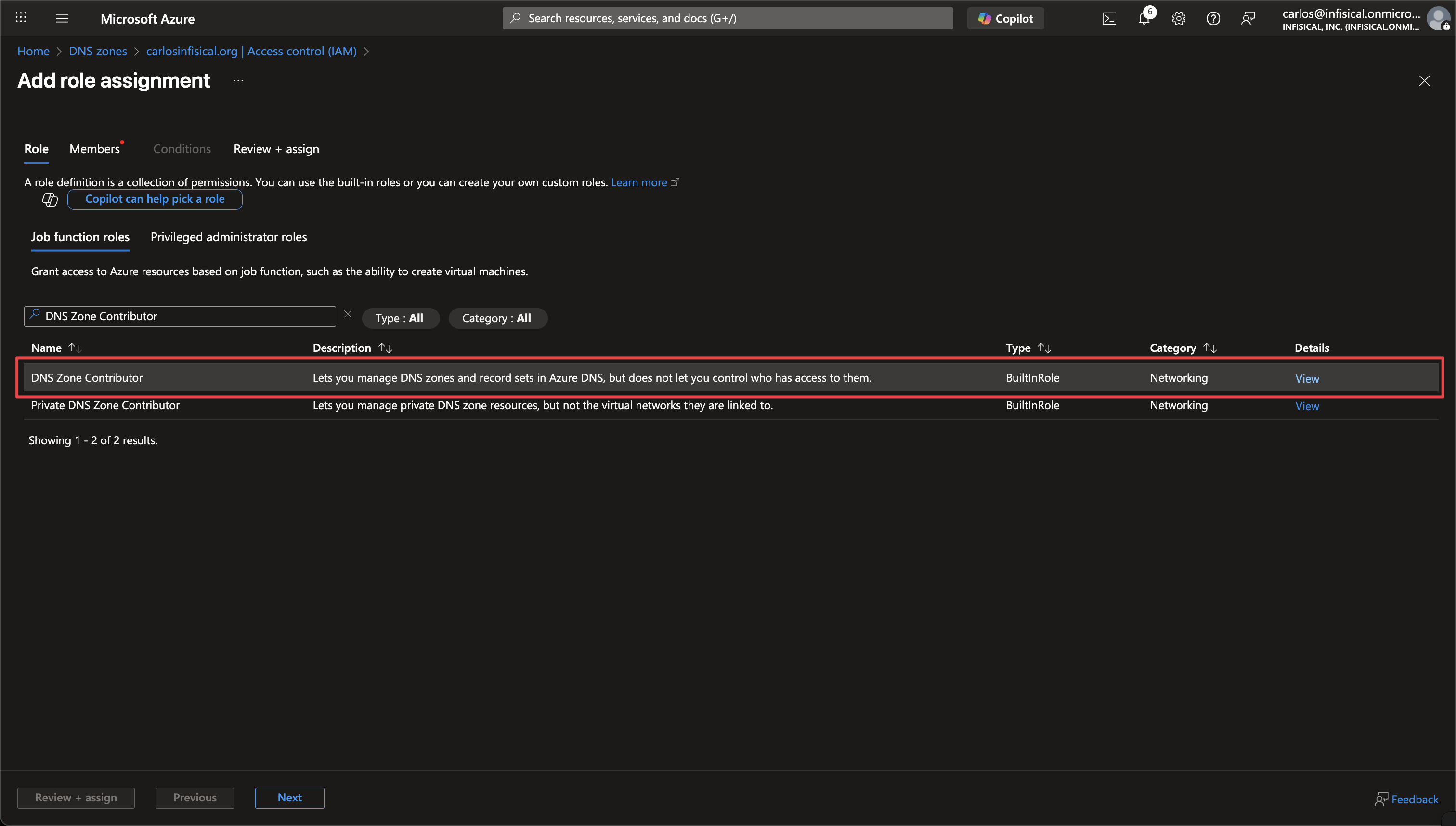

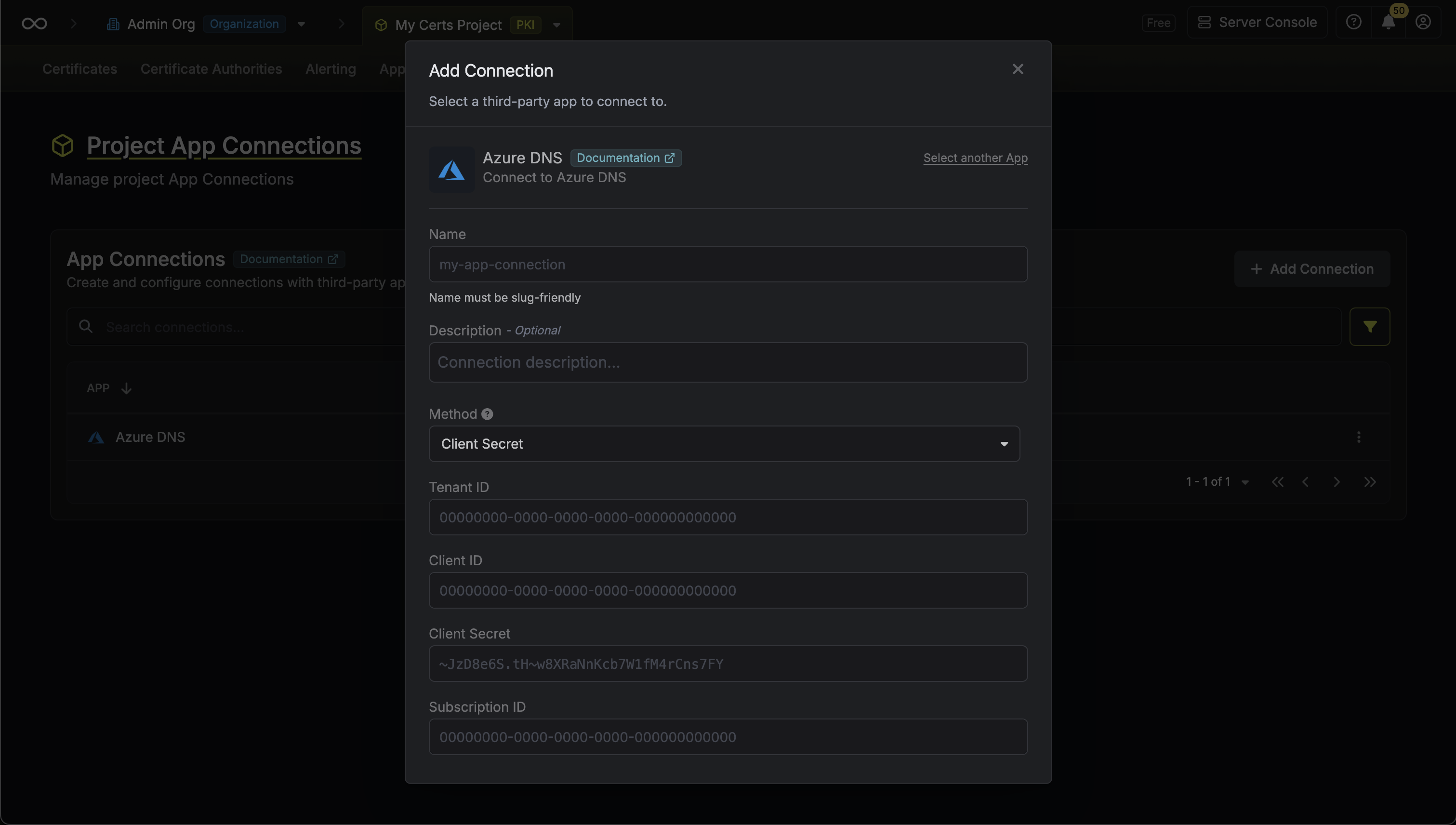
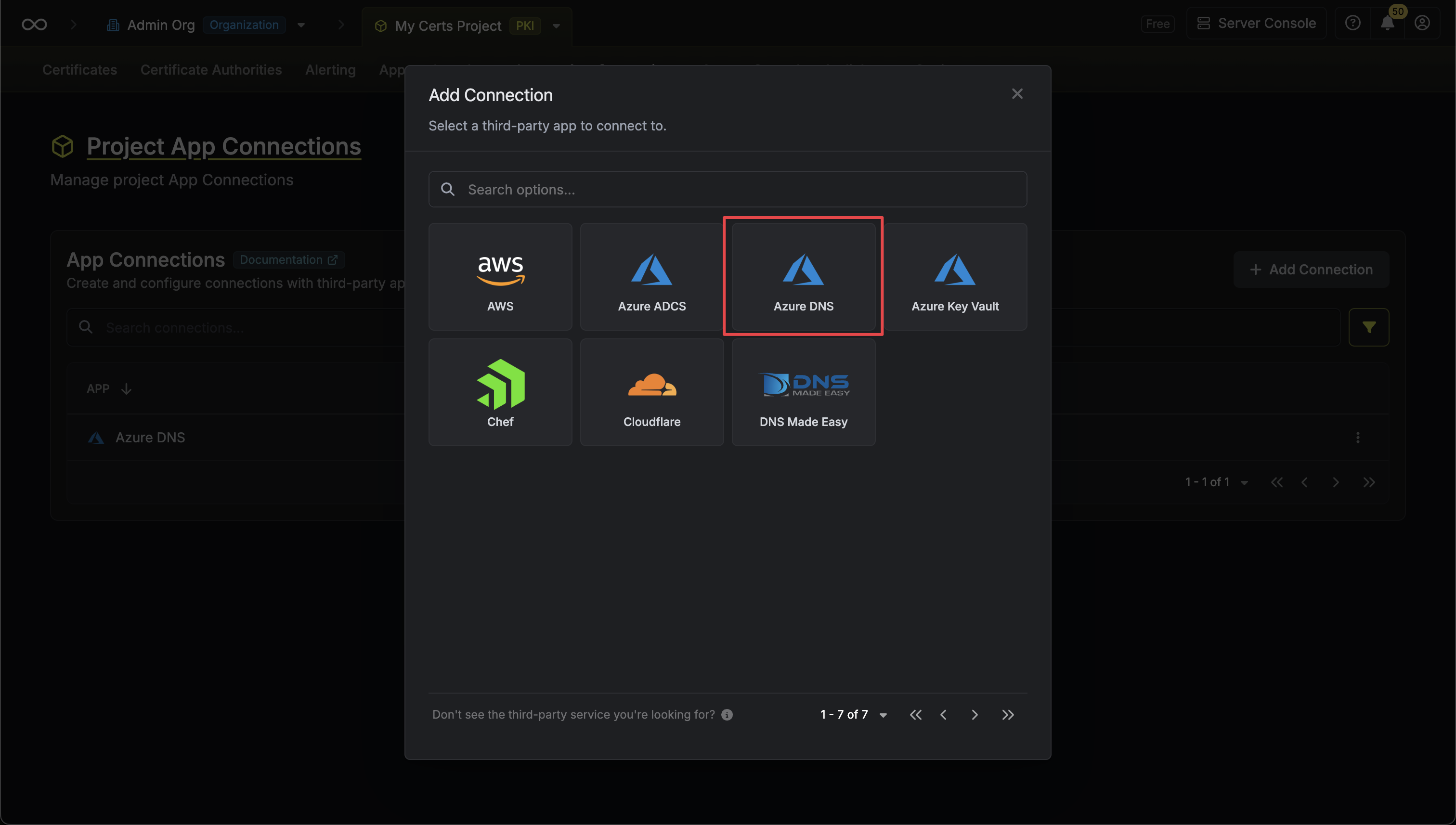
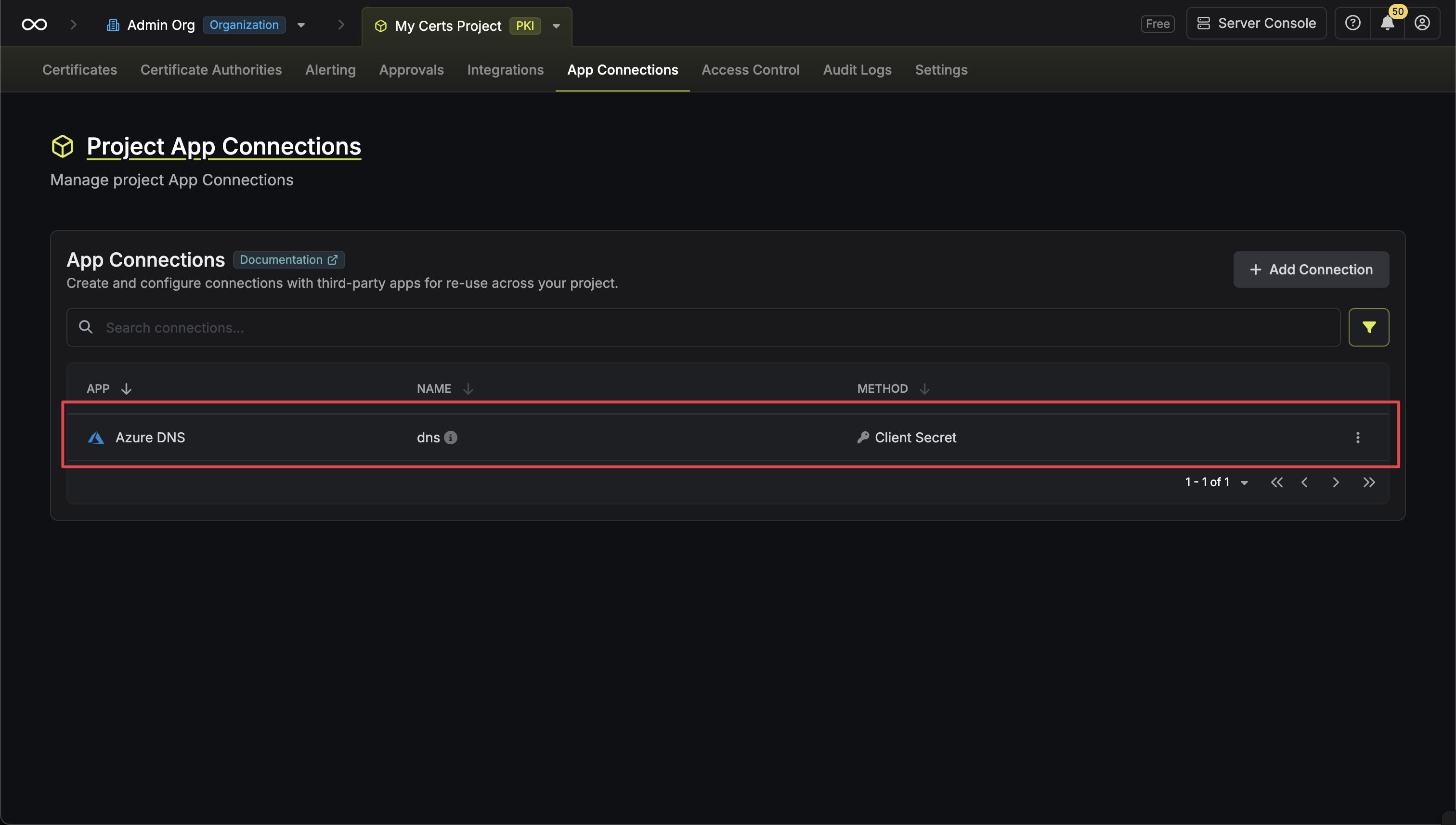
Setup Azure DNS Connection in Infisical
Create Connection
Fill in the Tenant ID, Client ID, Client Secret, and Subscription ID fields with the credentials from your Azure Service Principal.