Email 2FA
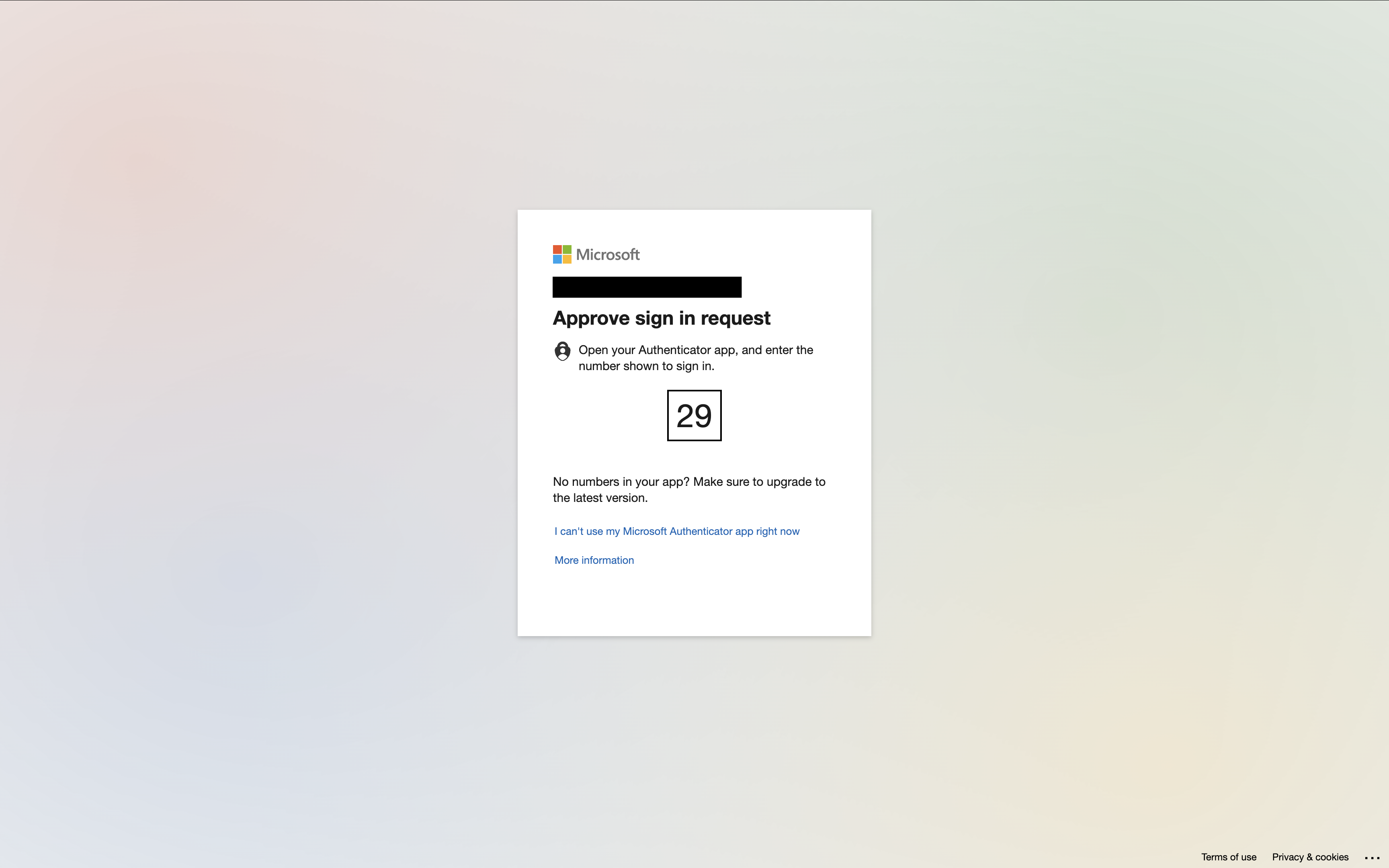
If 2-factor authentication is enabled in the Personal settings page, email will be used for MFA by default.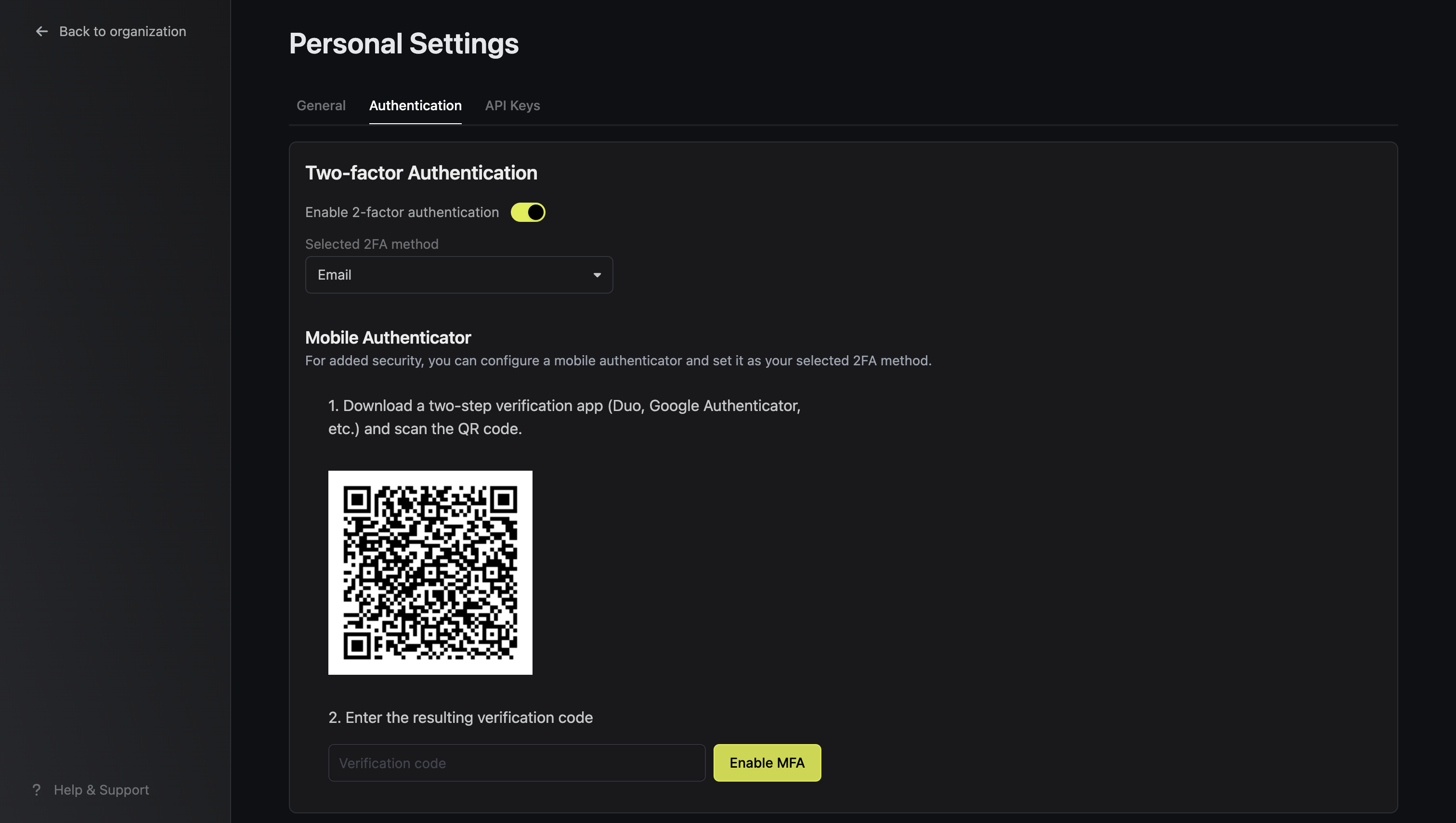
Mobile Authenticator 2FA
You can use any mobile authenticator app (Authy, Google Authenticator, Duo, etc.) to secure your account. After registration with an authenticator, select Mobile Authenticator as your 2FA method.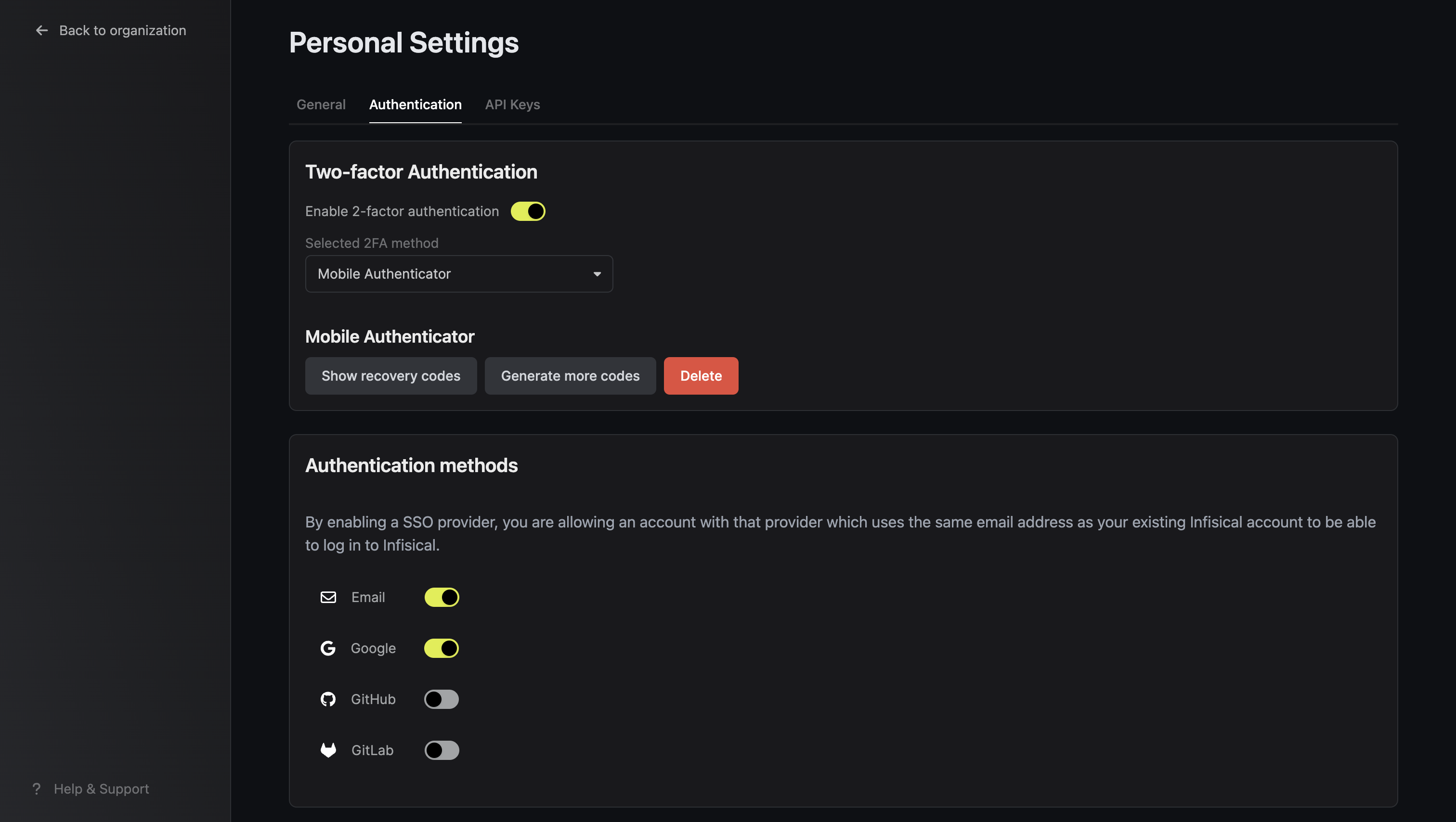
Entra ID / Azure AD MFA
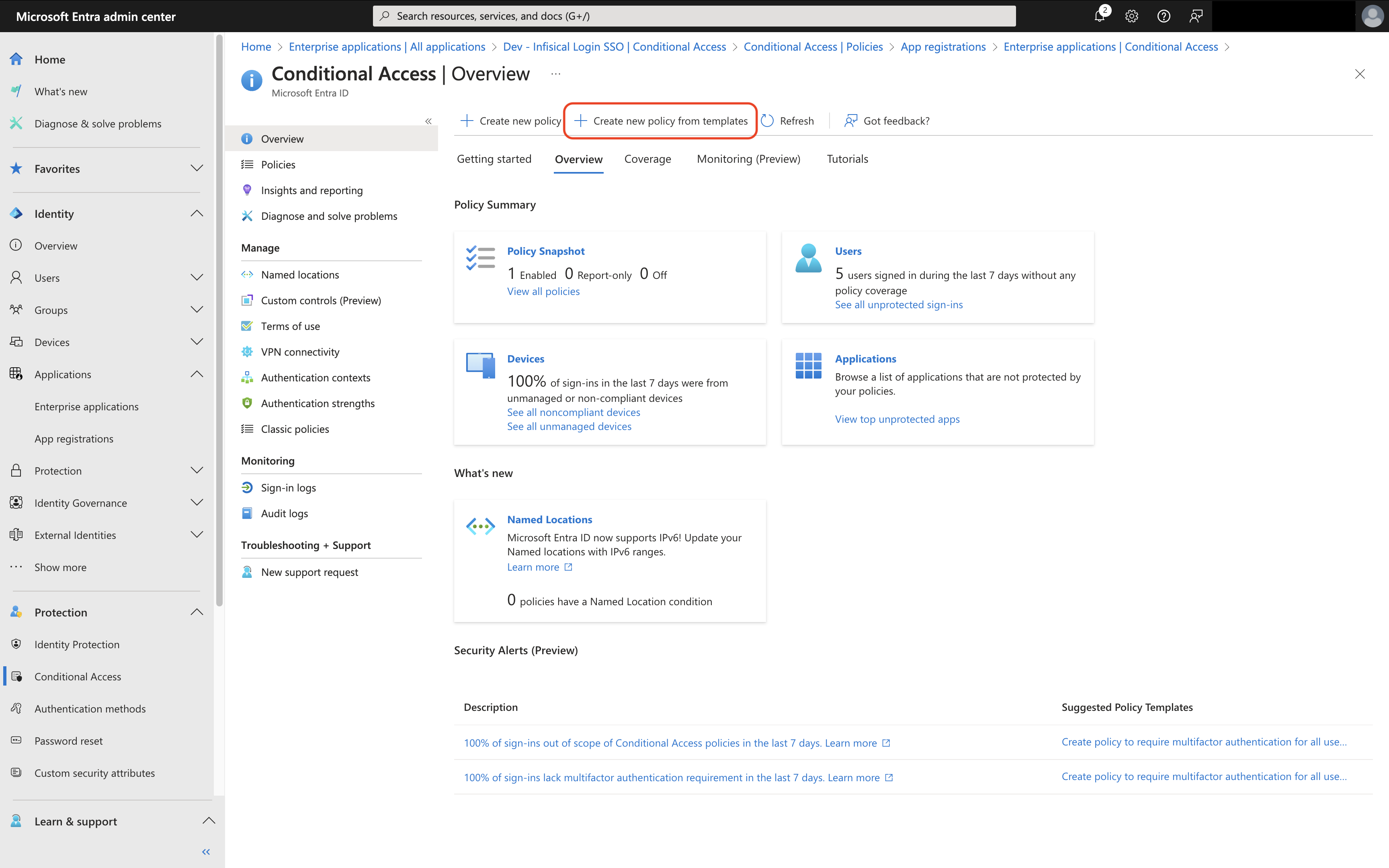
Before proceeding make sure you’ve enabled SAML SSO for Entra ID / Azure AD.We also encourage you to have your team download and setup the
Microsoft Authenticator App prior to enabling MFA.
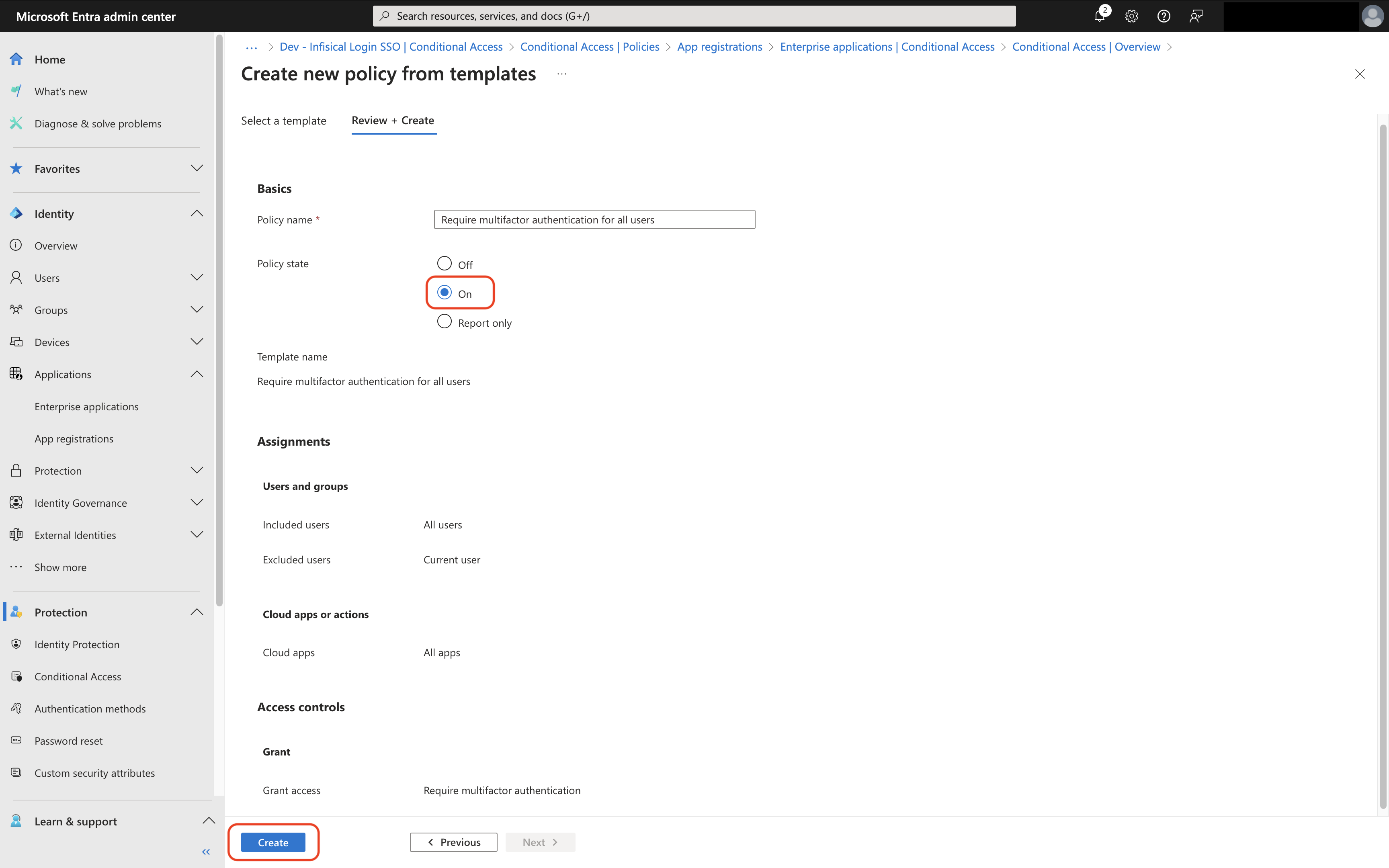
Select Require MFA for All Users and Tap on Review + Create
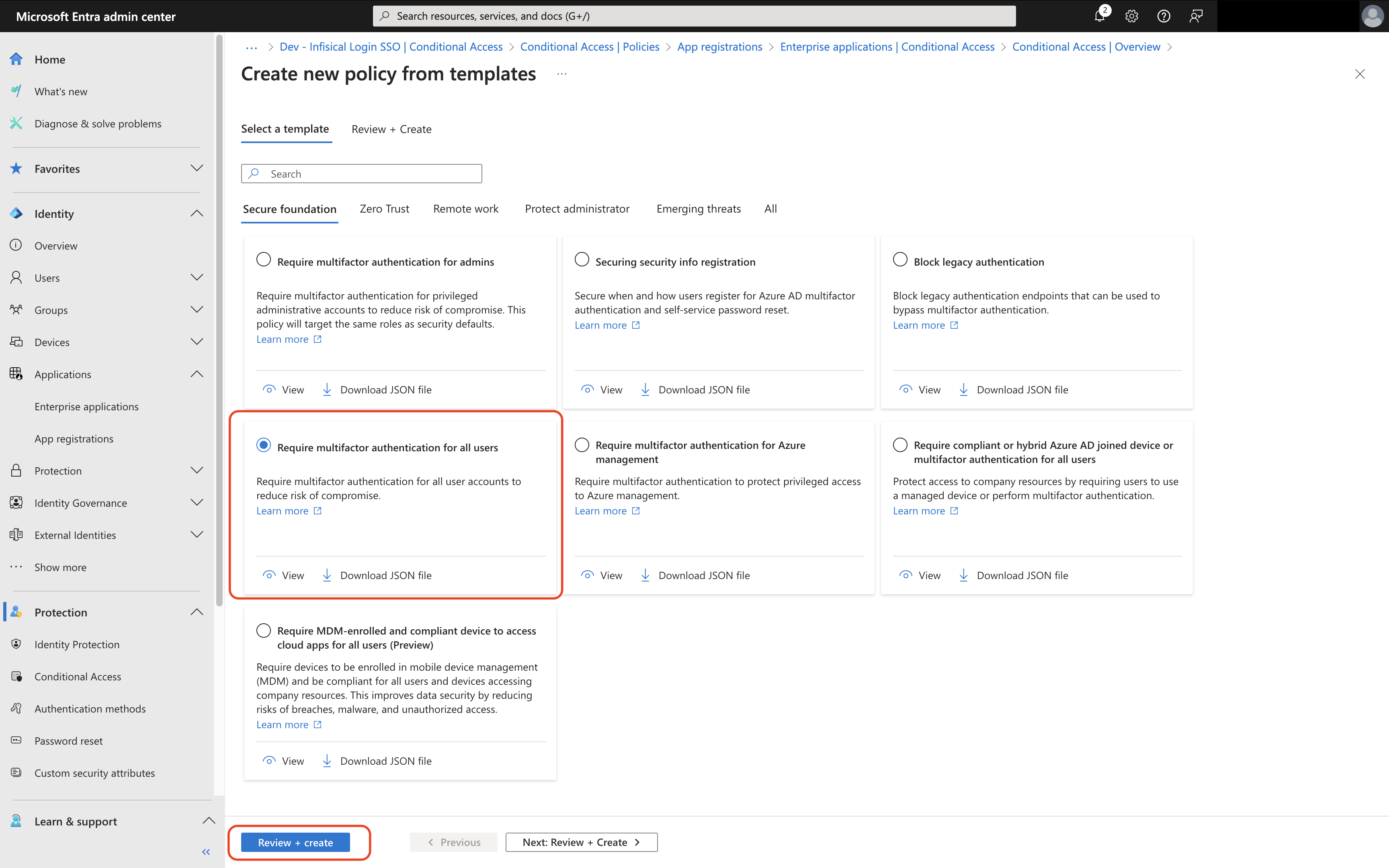
By default all users except the configuring admin will be setup to require
MFA. Microsoft encourages keeping at least one admin excluded from MFA to
prevent accidental lockout.