Self-Hosted Instance
Self-Hosted Instance
Using the Azure Key Vault connection on a self-hosted instance of Infisical requires configuring an application in Azure
and registering your instance with it.Prerequisites:
- Set up Azure and have an existing Key Vault instance.
Create an application in Azure
Navigate to Azure Active Directory > App registrations to create a new application.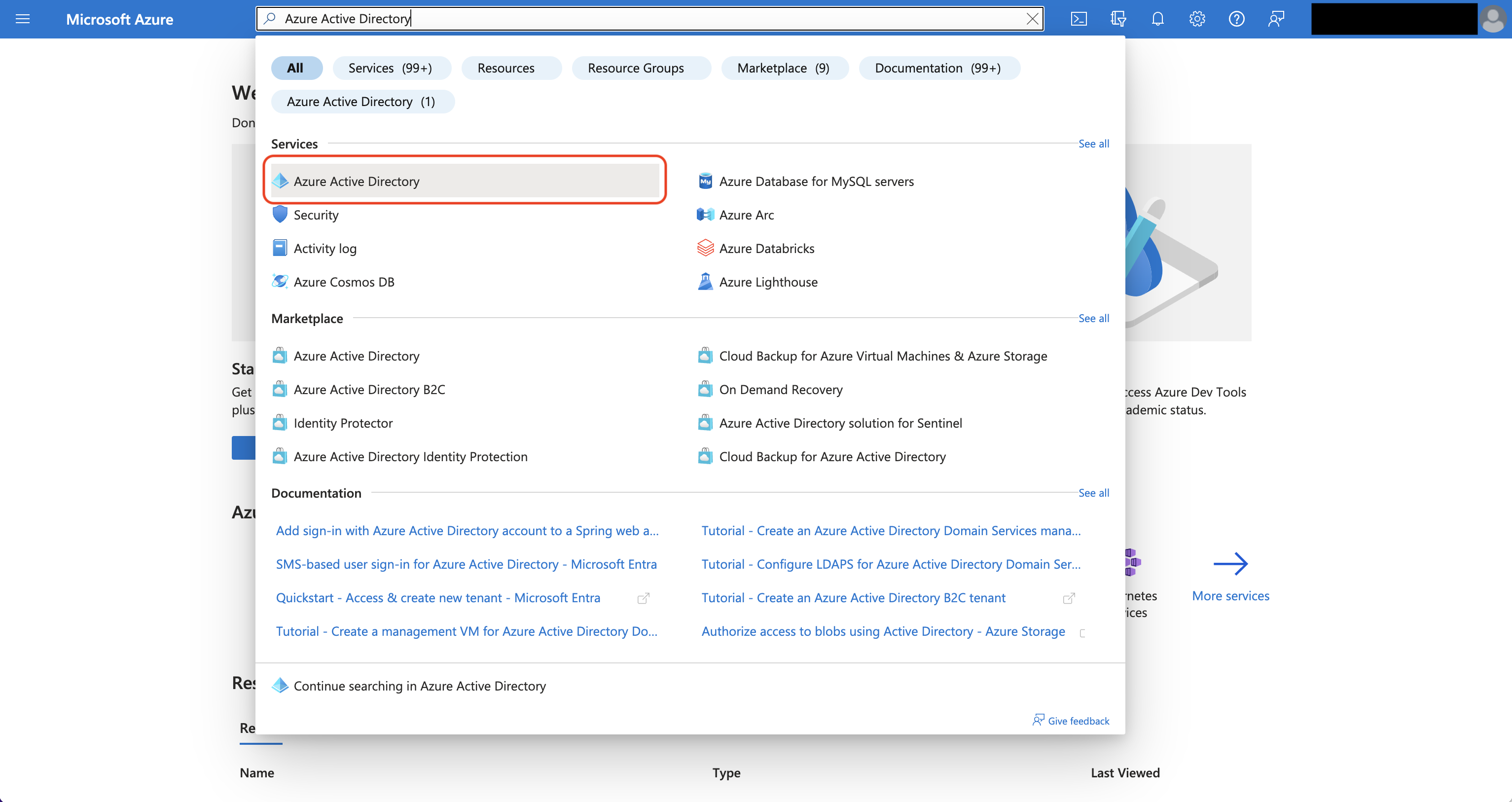
 Create the application. As part of the form, set the Redirect URI to
Create the application. As part of the form, set the Redirect URI to 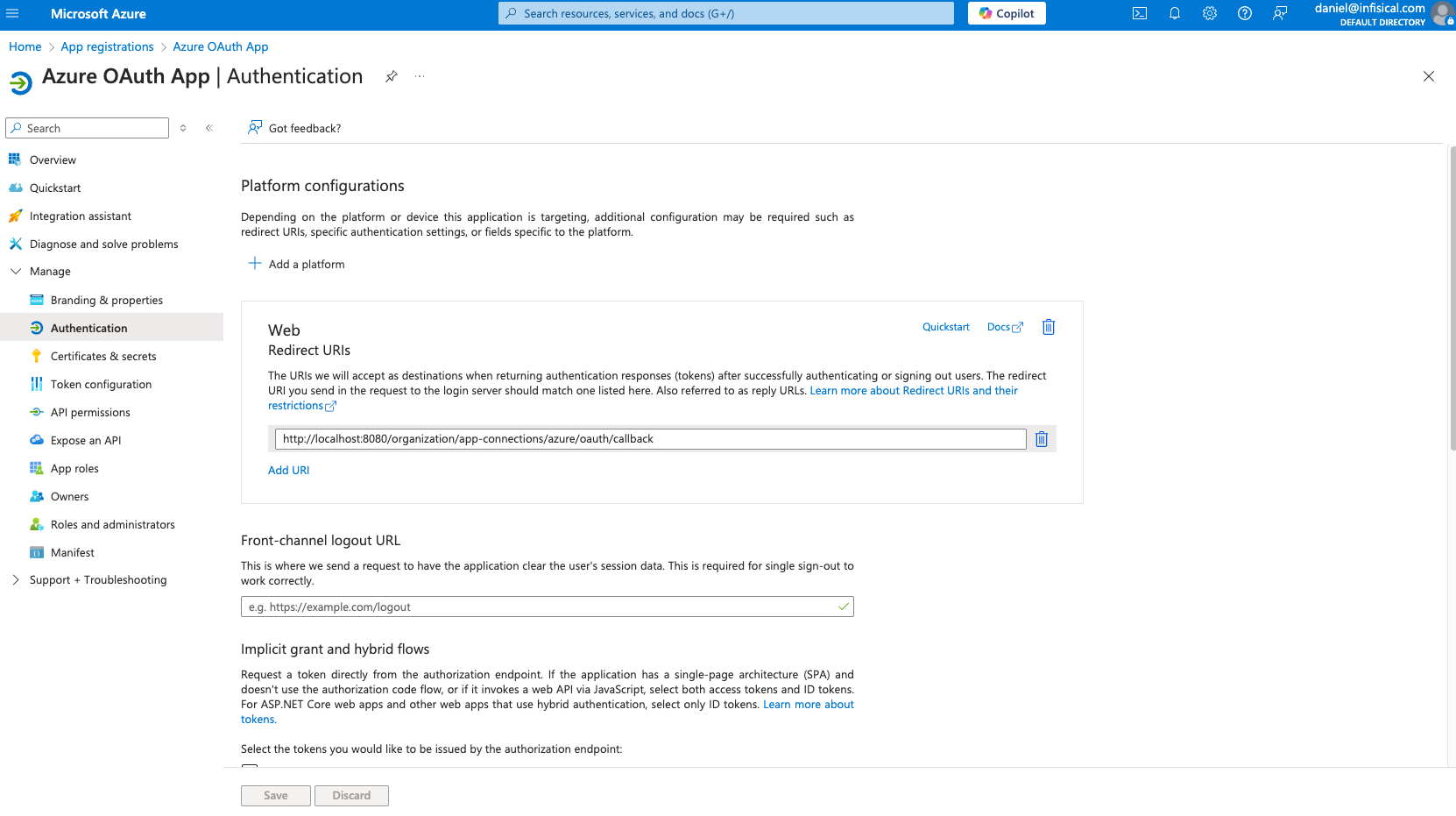
Azure Active Directory is now Microsoft Entra ID.

 Create the application. As part of the form, set the Redirect URI to
Create the application. As part of the form, set the Redirect URI to https://your-domain.com/organization/app-connections/azure/oauth/callback.
Assign API permissions to the application
For the Azure Connection to work with Key Vault, you need to assign multiple permissions to the application.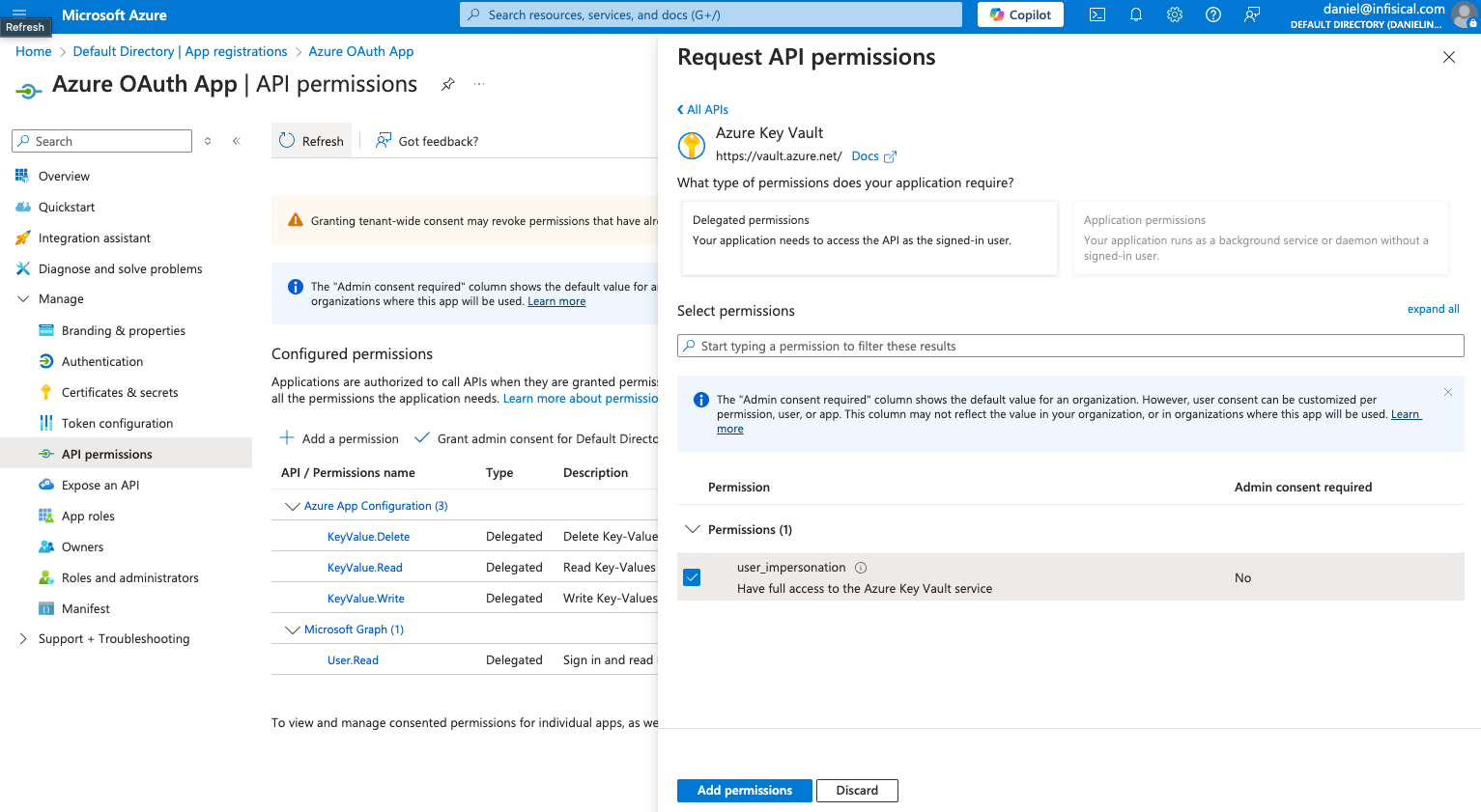
Azure Key Vault permissions
Set the API permissions of the Azure application to includeuser.impersonation for the Key Vault API.
Add your application credentials to Infisical
Obtain the Application (Client) ID in Overview and generate a Client Secret in Certificate & secrets for your Azure application.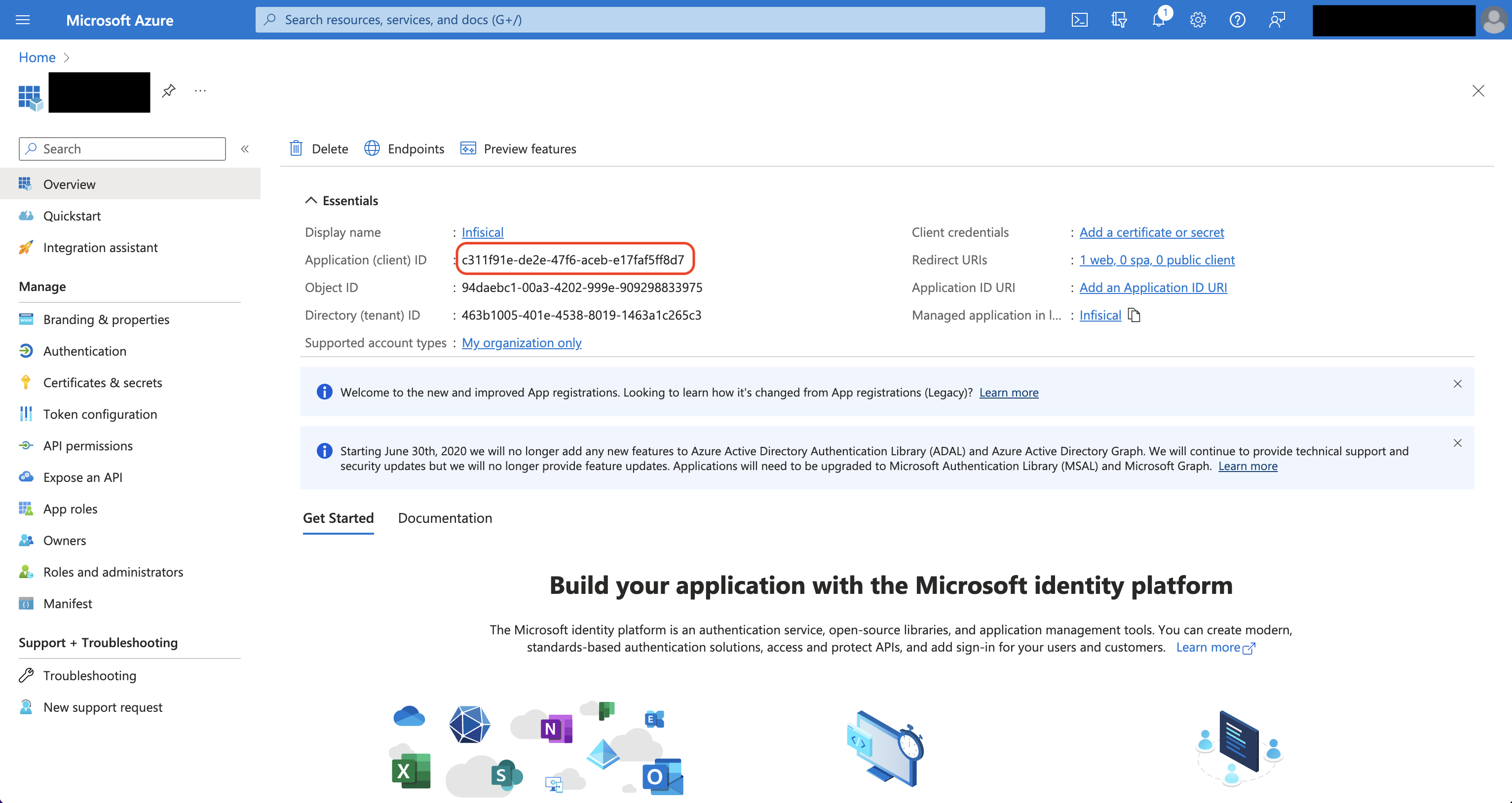
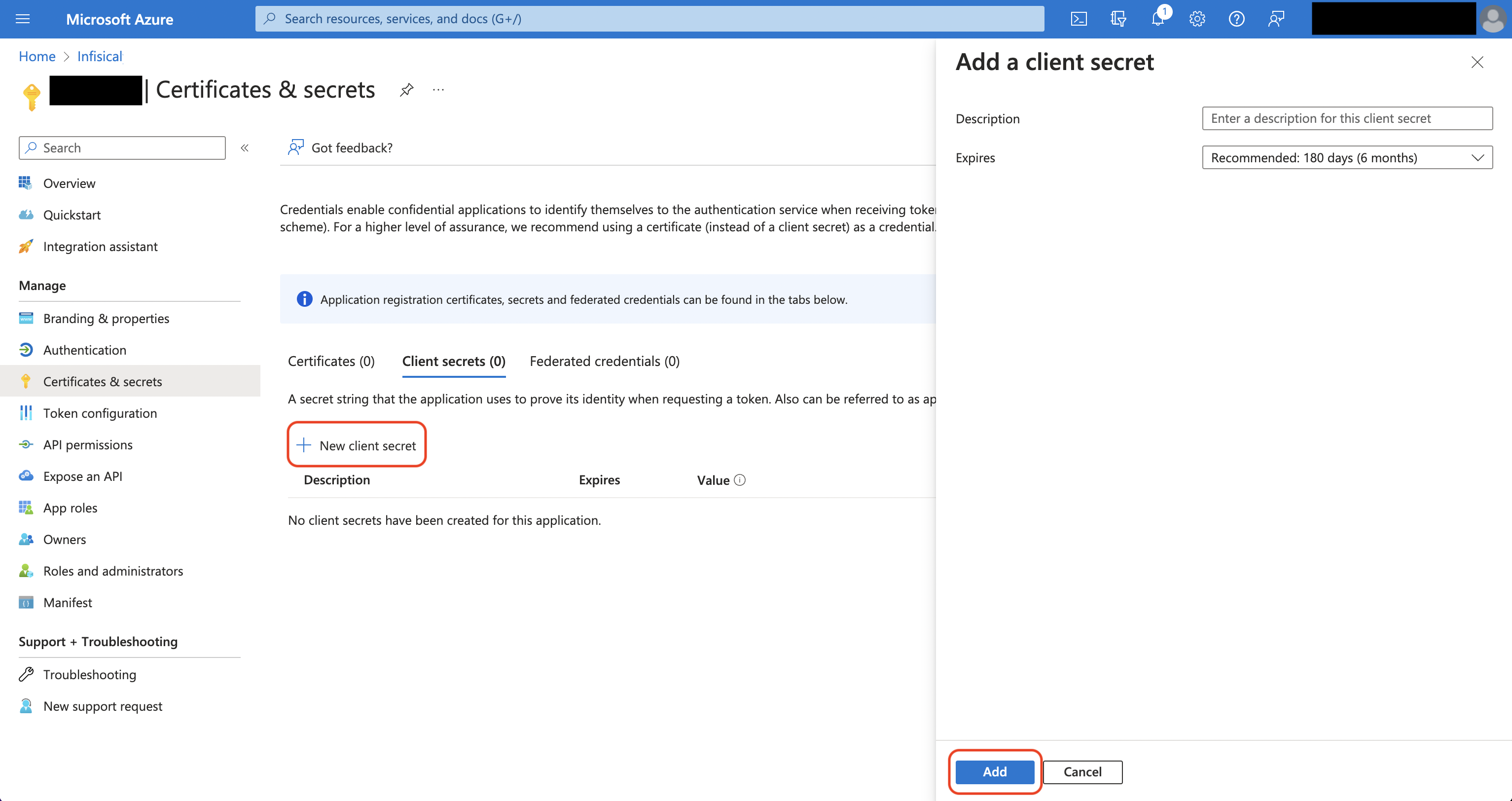
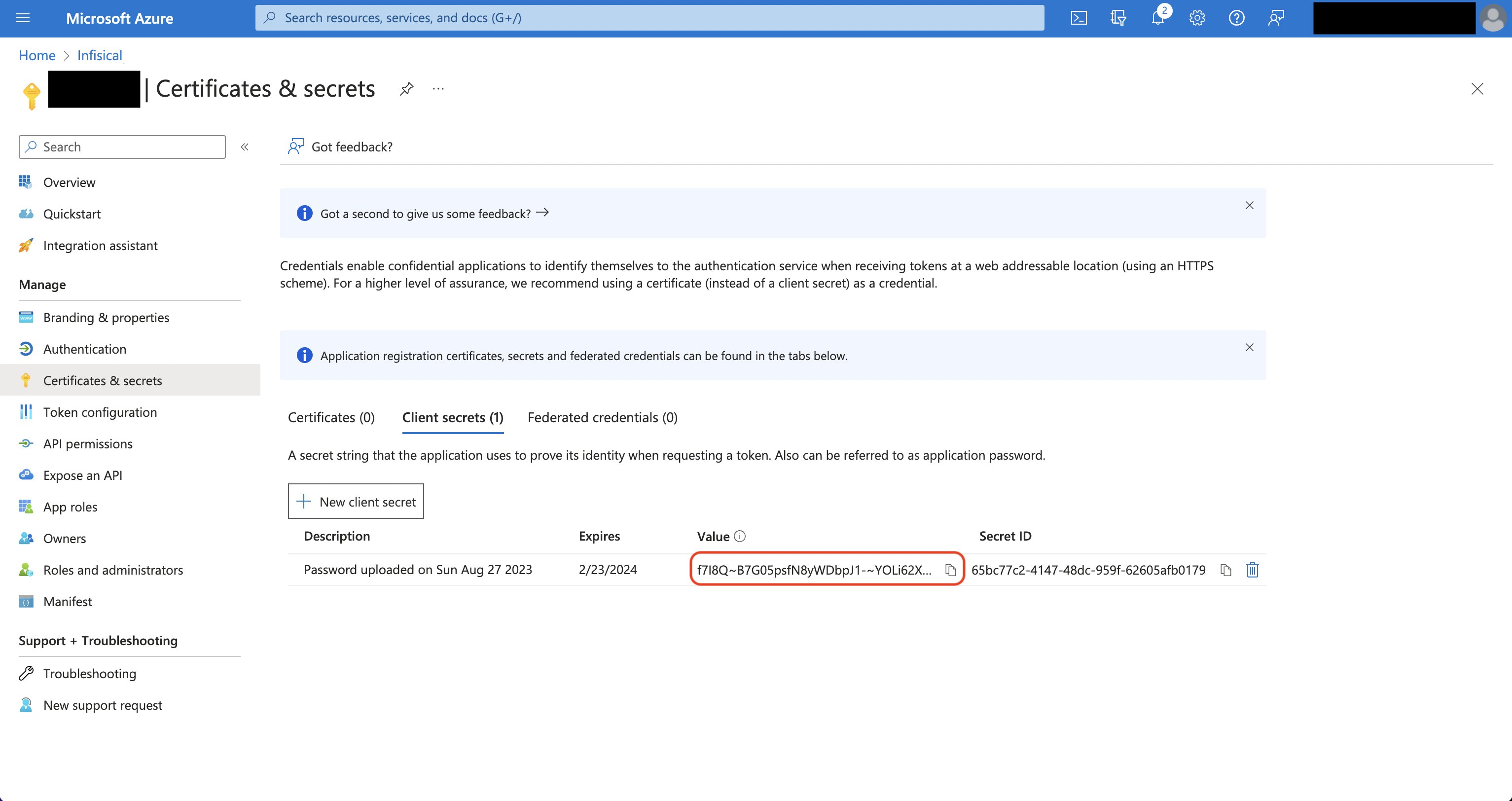 Back in your Infisical instance, add two new environment variables for the credentials of your Azure application.
Back in your Infisical instance, add two new environment variables for the credentials of your Azure application.


 Back in your Infisical instance, add two new environment variables for the credentials of your Azure application.
Back in your Infisical instance, add two new environment variables for the credentials of your Azure application.INF_APP_CONNECTION_AZURE_KEY_VAULT_CLIENT_ID: The Application (Client) ID of your Azure application.INF_APP_CONNECTION_AZURE_KEY_VAULT_CLIENT_SECRET: The Client Secret of your Azure application.
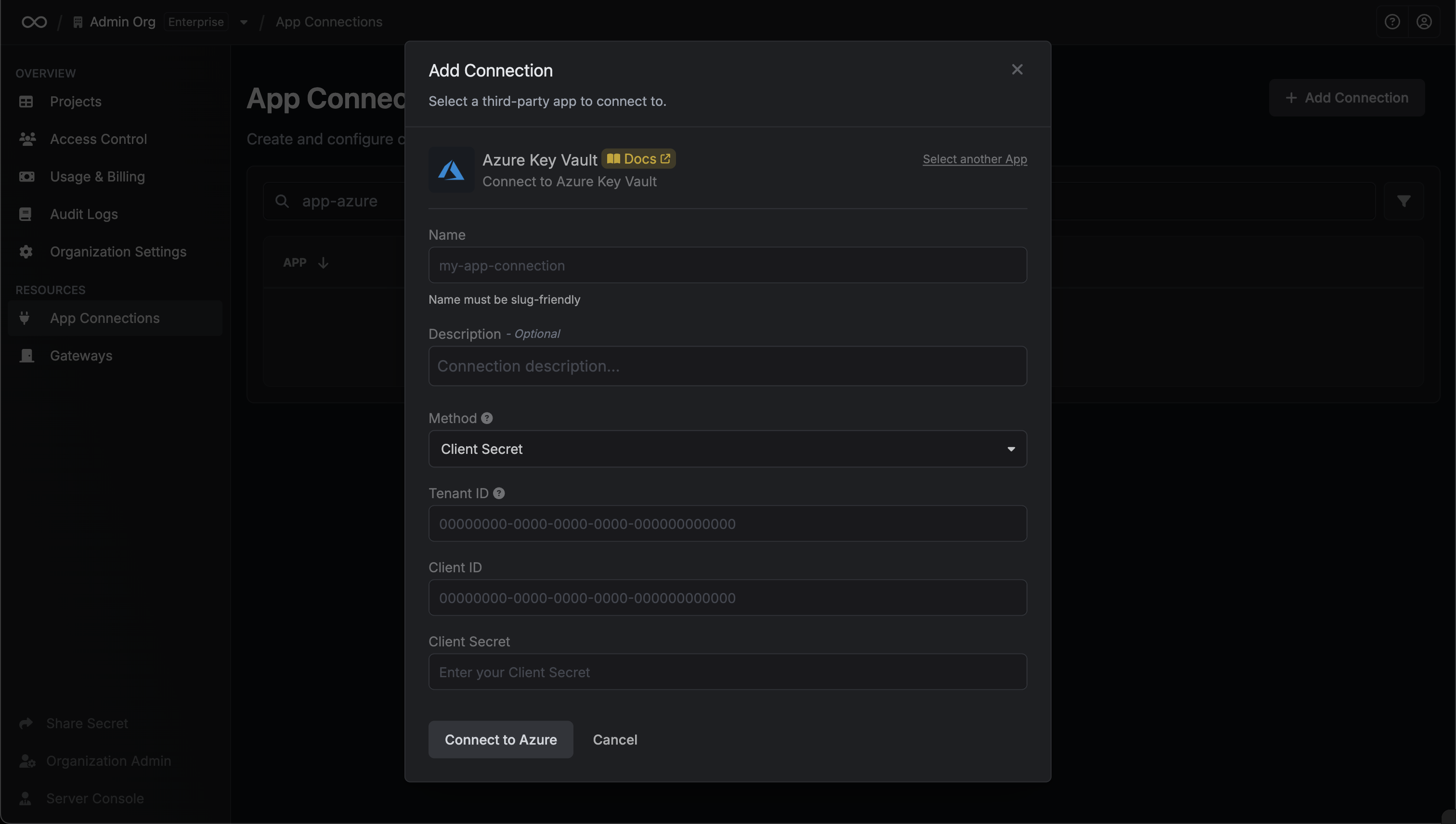
Client Secret Authentication
Client Secret Authentication
To use client secret authentication, ensure your Azure Service Principal has the required permissions and is connected to the Azure Key Vault instances you want to use.Prerequisites:
- Set up Azure and have an existing Key Vault instance.
- The service principal must be connected to your target Azure Key Vault instance(s)
Assign API permissions to the service principal
Configure the required API permissions for your App Registration to interact with Azure Key Vault:
Azure Key Vault permissions
Set the API permissions of your Azure service principal to includeuser_impersonation for the Key Vault API.
Setup Azure Connection in Infisical
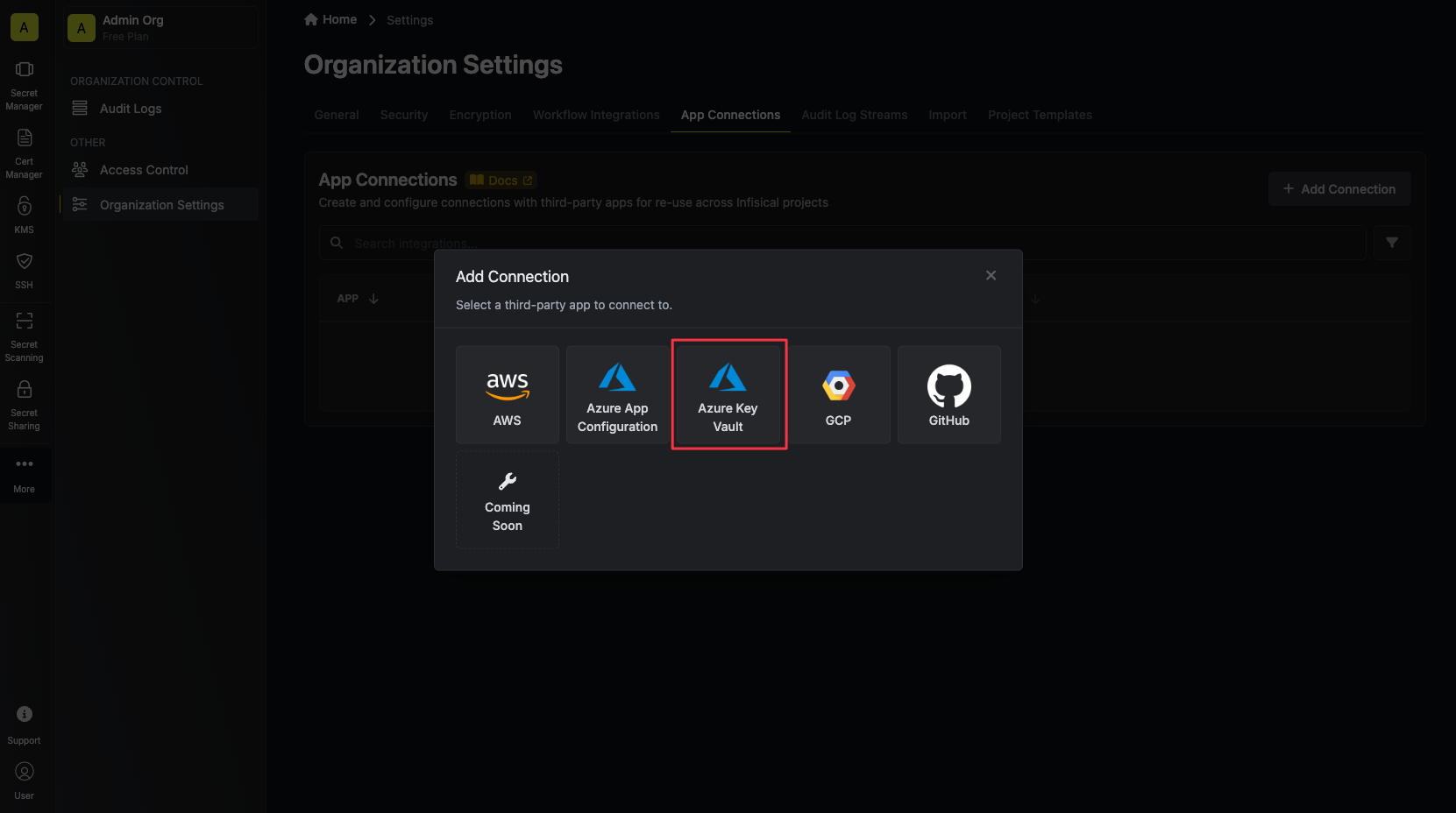
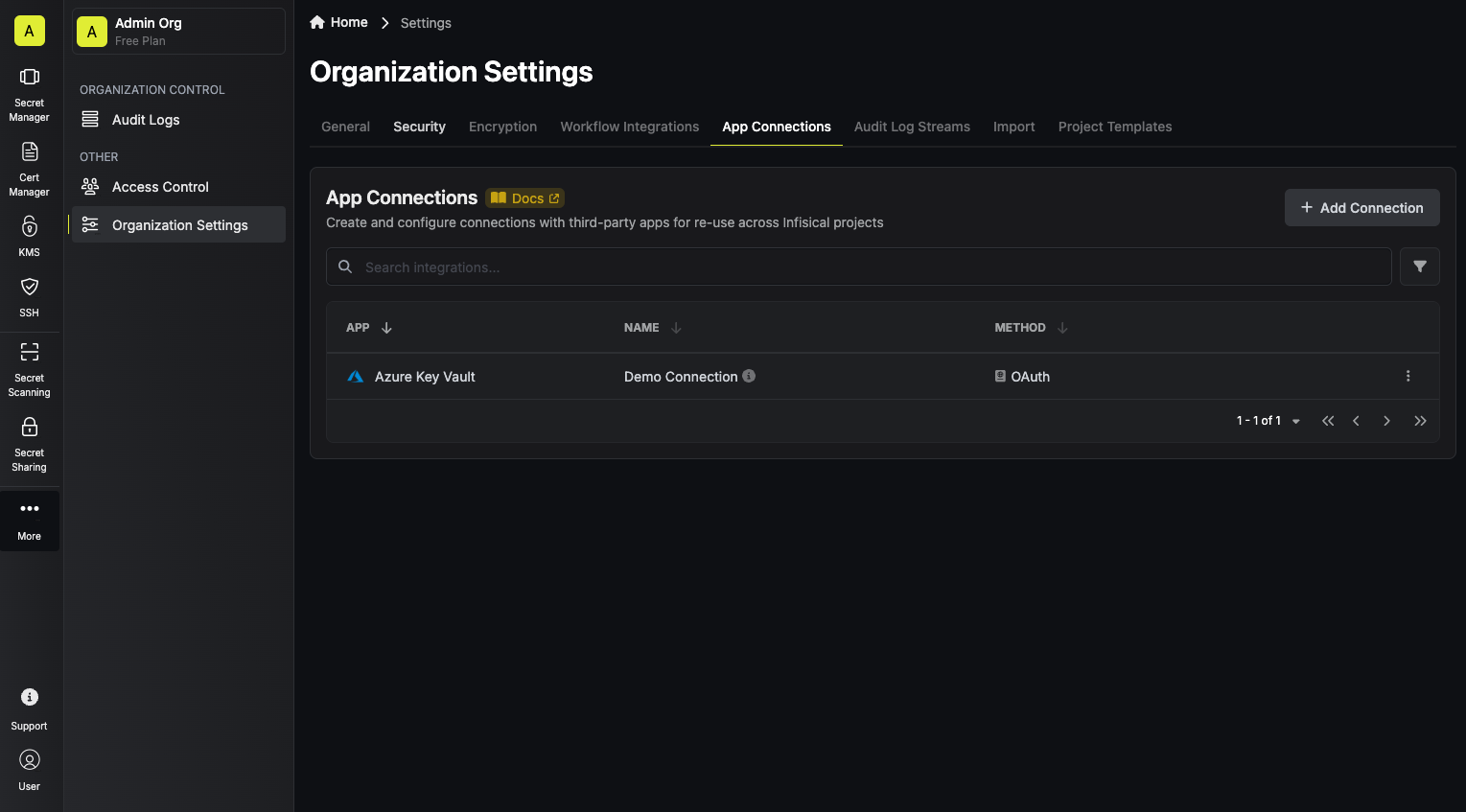
Navigate to App Connections
Navigate to the Integrations tab in the desired project, then select App Connections. 

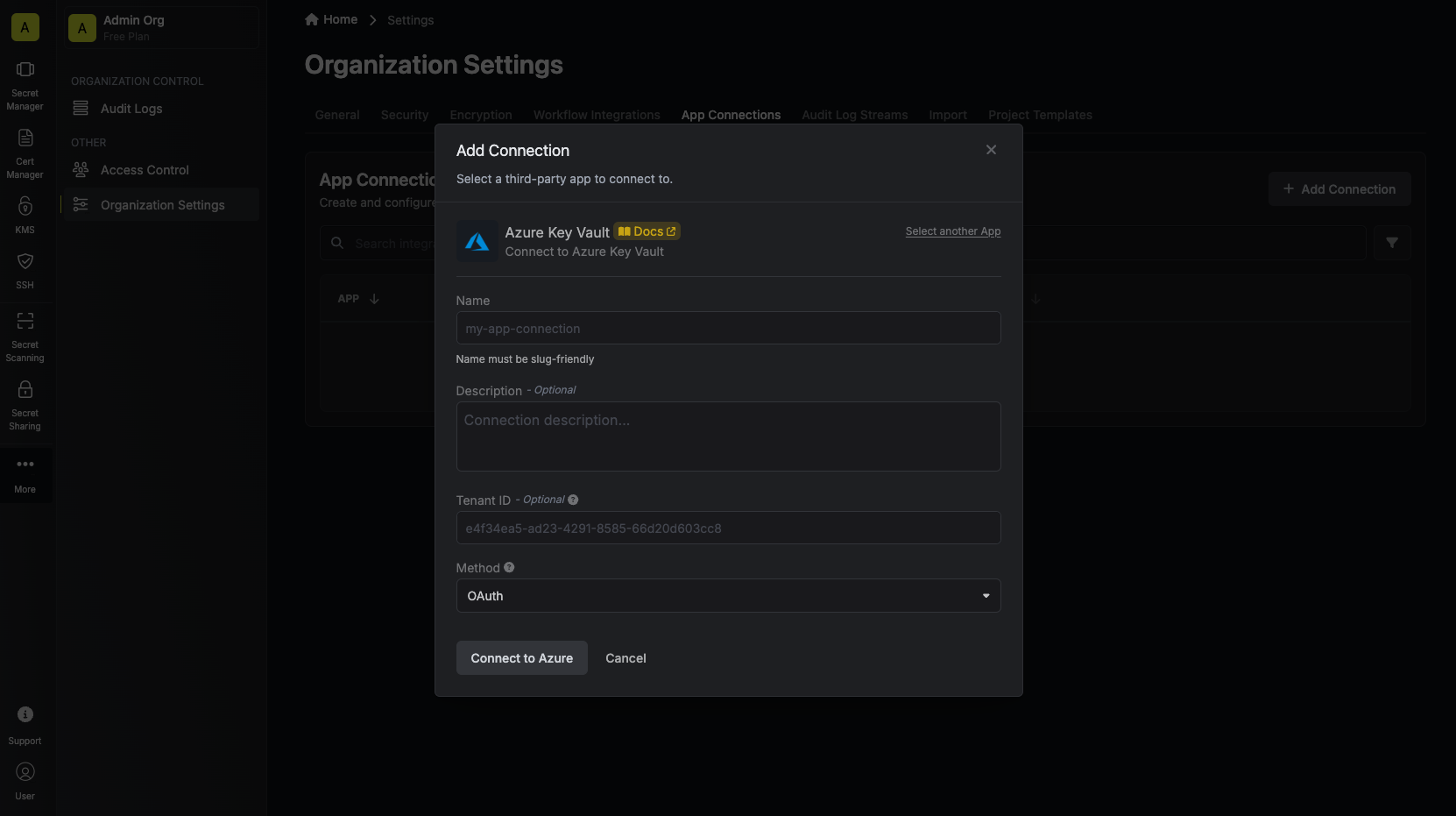
Create Connection
- OAuth
- Client Secret
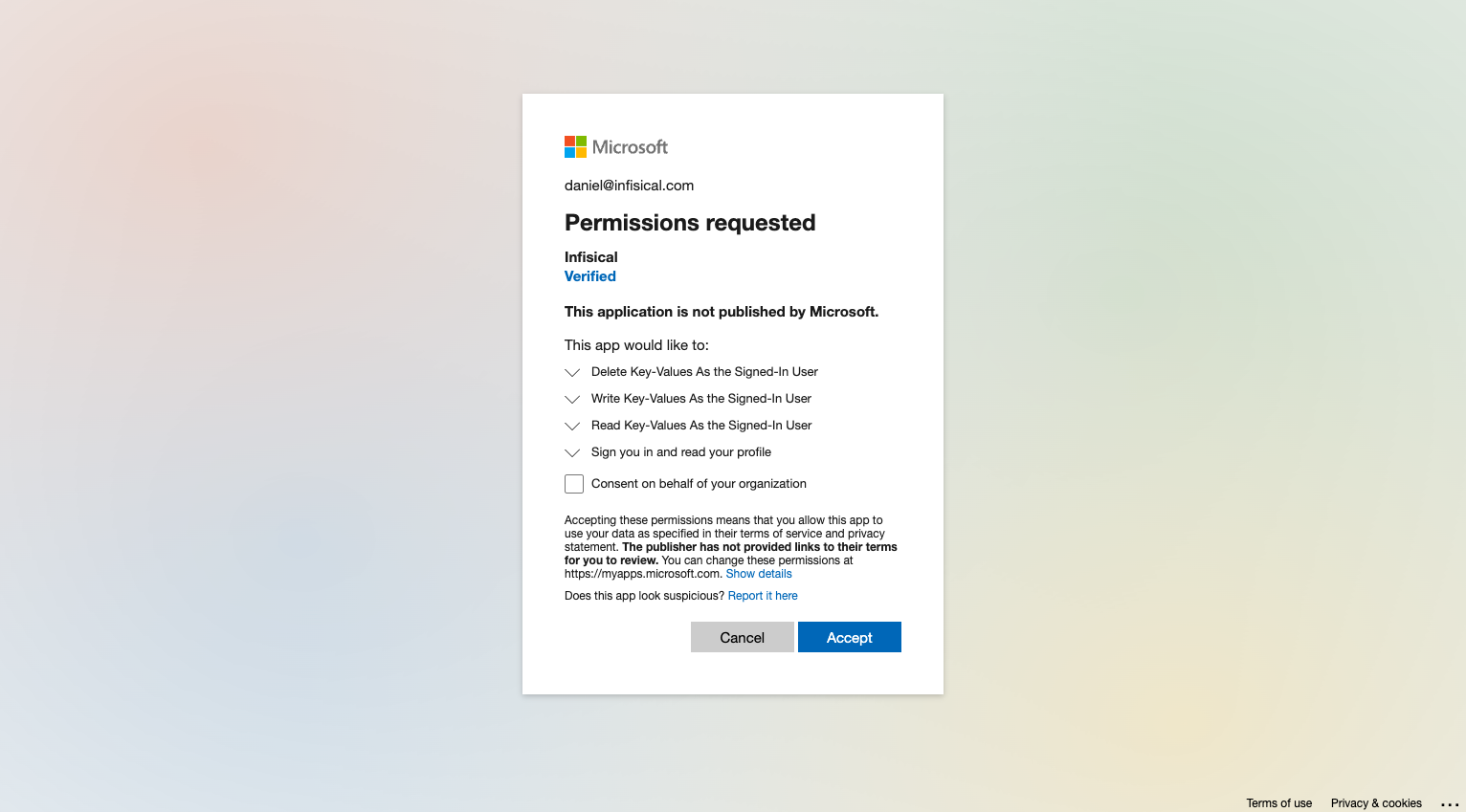
Authorize Connection
You can optionally authenticate against a specific tenant by providing the Azure Tenant or Directory ID.Now select the OAuth method and click Connect to Azure.