Templates
You can create reusable LDAP authentication templates to standardize configurations across multiple machine identities. Templates help ensure consistency, reduce configuration errors, and simplify identity management at scale. To create and manage LDAP auth templates, see our Machine Identity Auth Templates documentation. Once you’ve created a template, you can apply it when configuring LDAP auth for your identities in the guide below.Guide
Creating an identity
To create an identity, head to your Organization Settings > Access Control > Identities and press Create identity.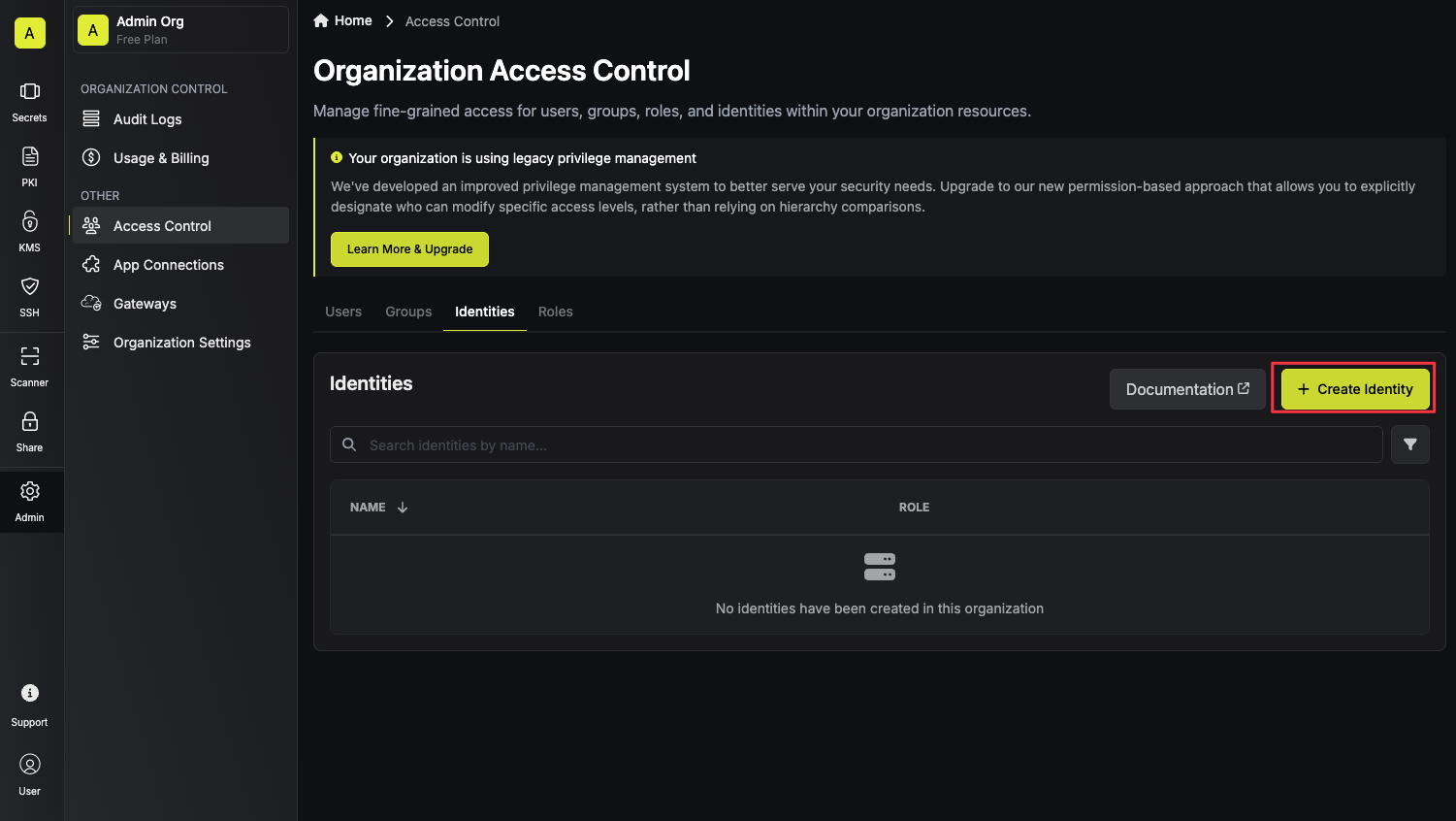 When creating an identity, you specify an organization level role for it to assume; you can configure roles in Organization Settings > Access Control > Organization Roles.
When creating an identity, you specify an organization level role for it to assume; you can configure roles in Organization Settings > Access Control > Organization Roles.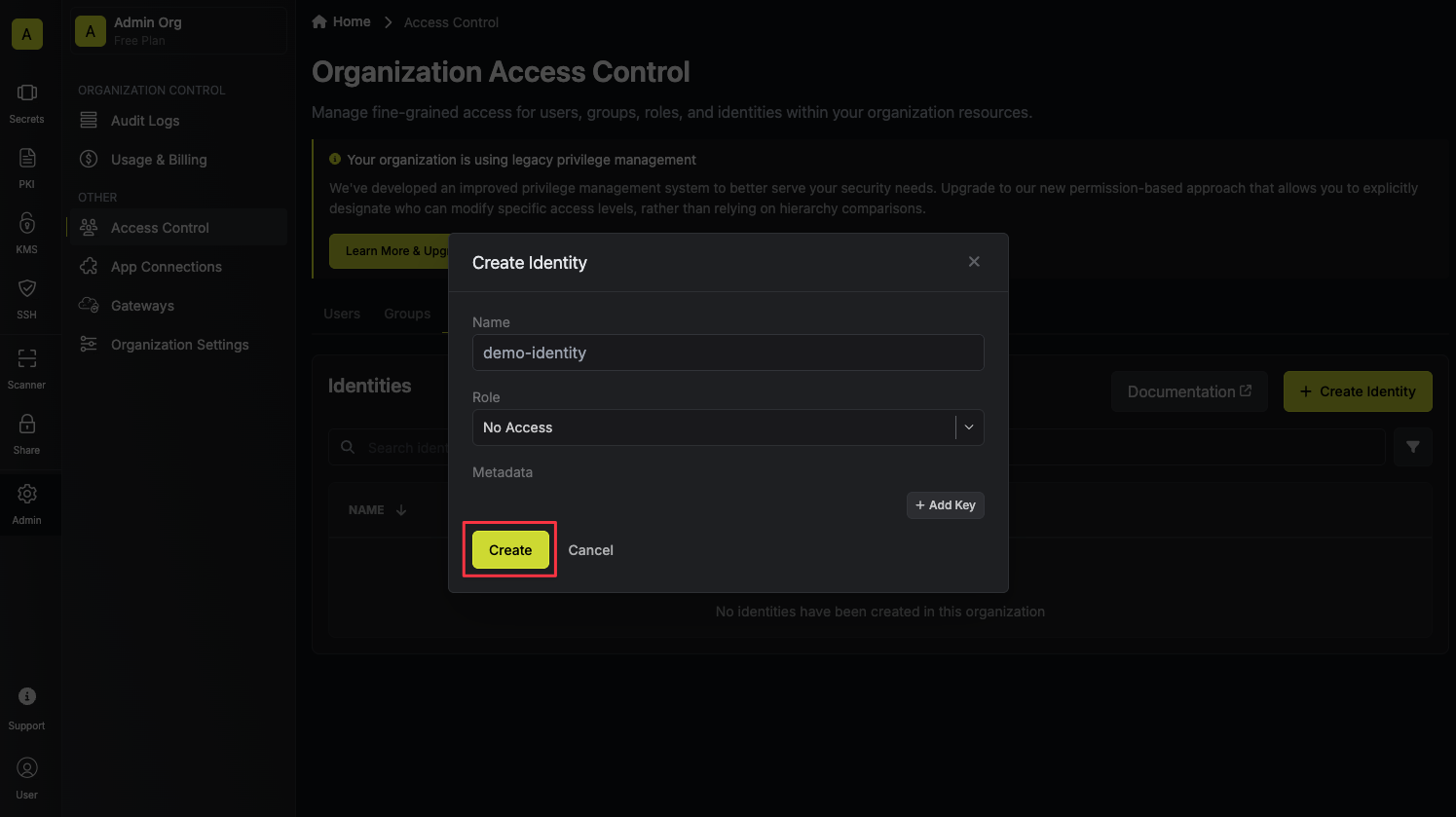 Now input a few details for your new identity. Here’s some guidance for each field:
Now input a few details for your new identity. Here’s some guidance for each field:
 When creating an identity, you specify an organization level role for it to assume; you can configure roles in Organization Settings > Access Control > Organization Roles.
When creating an identity, you specify an organization level role for it to assume; you can configure roles in Organization Settings > Access Control > Organization Roles. Now input a few details for your new identity. Here’s some guidance for each field:
Now input a few details for your new identity. Here’s some guidance for each field:- Name (required): A friendly name for the identity.
- Role (required): A role from the Organization Roles tab for the identity to assume. The organization role assigned will determine what organization level resources this identity can have access to.
Configuring LDAP auth for your identity
To configure LDAP auth for your identity, press the Add Auth Method button on the identity’s page.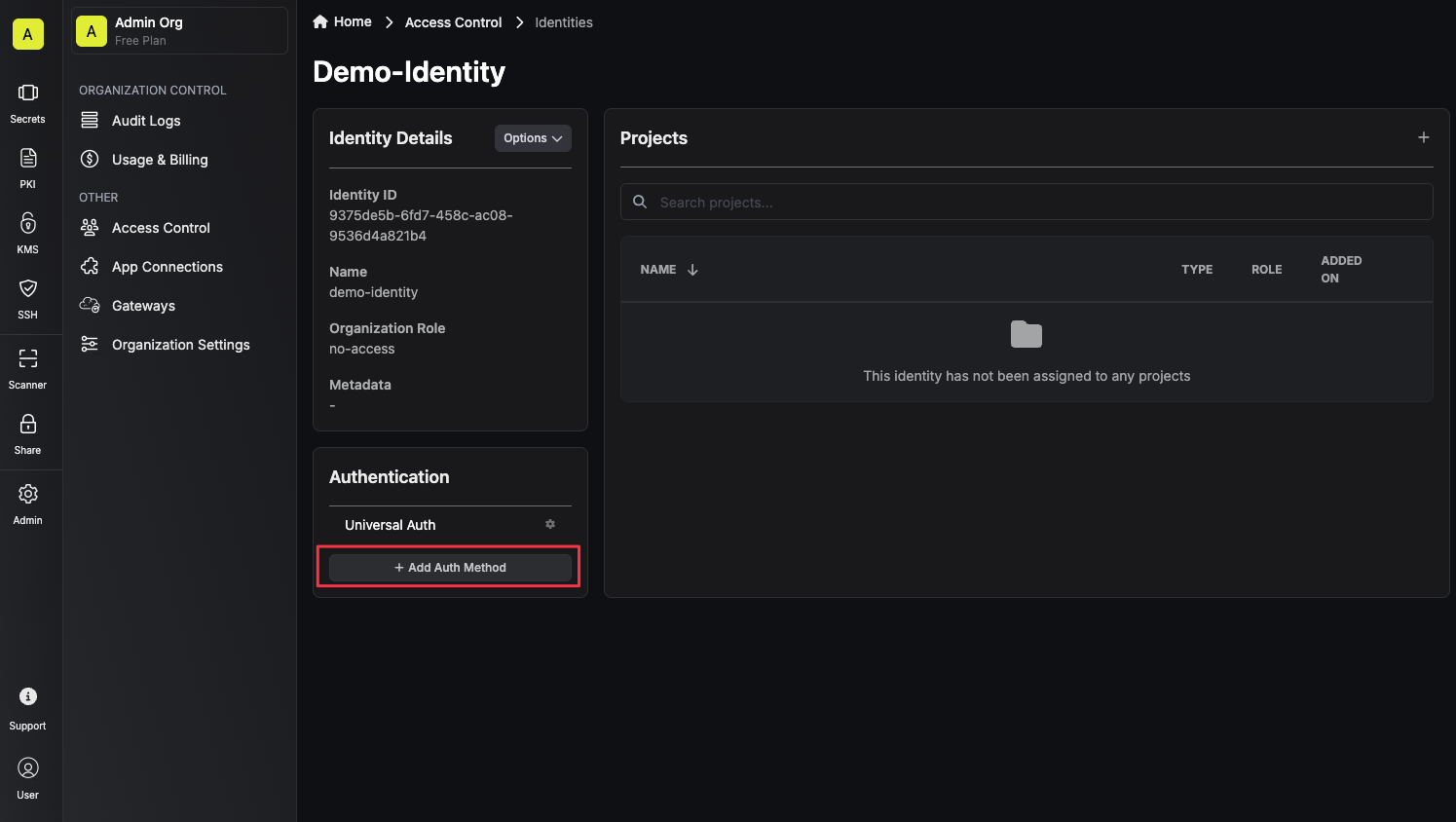 Now select LDAP Auth from the list of available auth methods for the identity.
Now select LDAP Auth from the list of available auth methods for the identity. After selecting LDAP Auth, you’ll see the form you need to fill out to configure LDAP auth for your identity. The following fields are available:Configuration Tab
After selecting LDAP Auth, you’ll see the form you need to fill out to configure LDAP auth for your identity. The following fields are available:Configuration Tab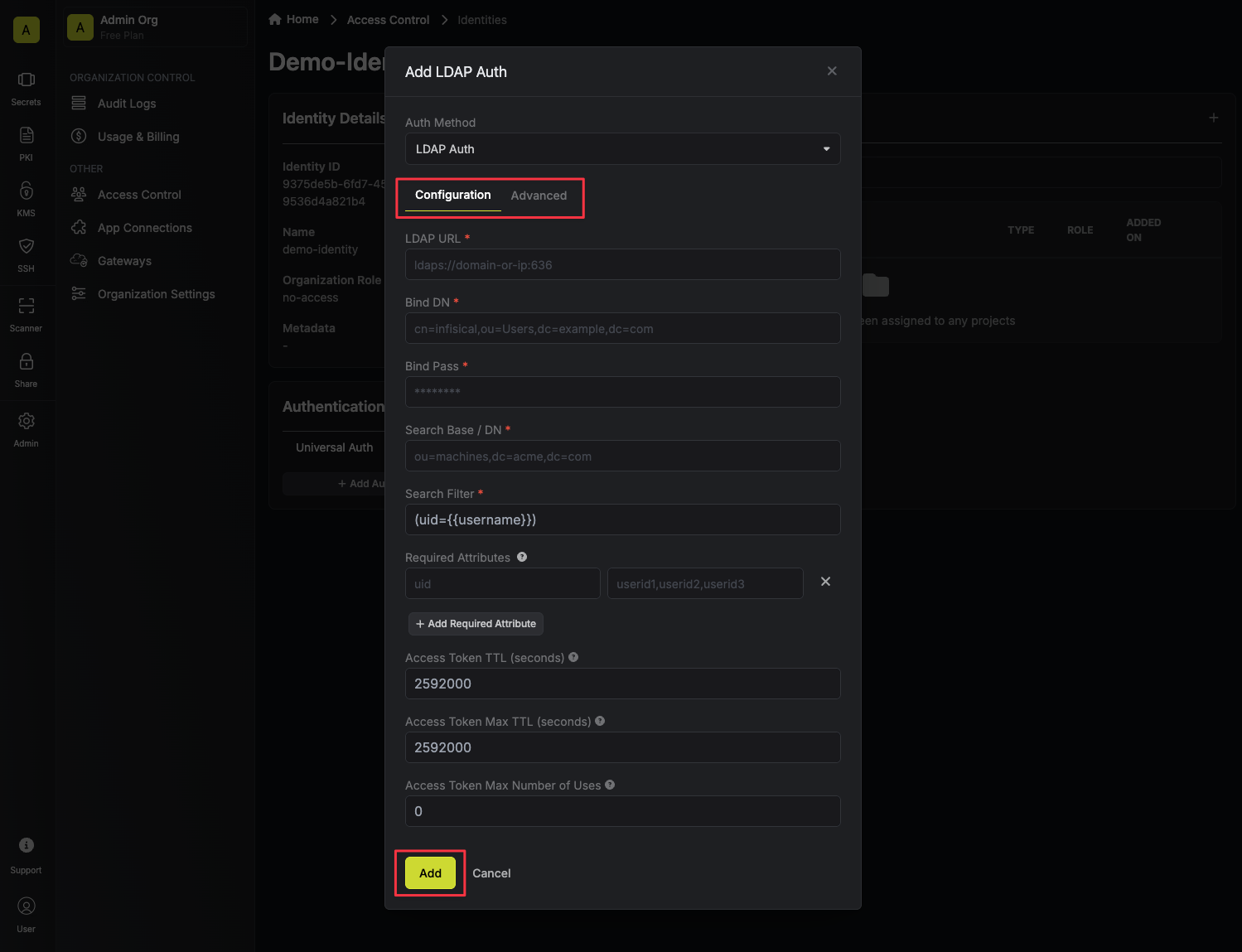
 Now select LDAP Auth from the list of available auth methods for the identity.
Now select LDAP Auth from the list of available auth methods for the identity. After selecting LDAP Auth, you’ll see the form you need to fill out to configure LDAP auth for your identity. The following fields are available:Configuration Tab
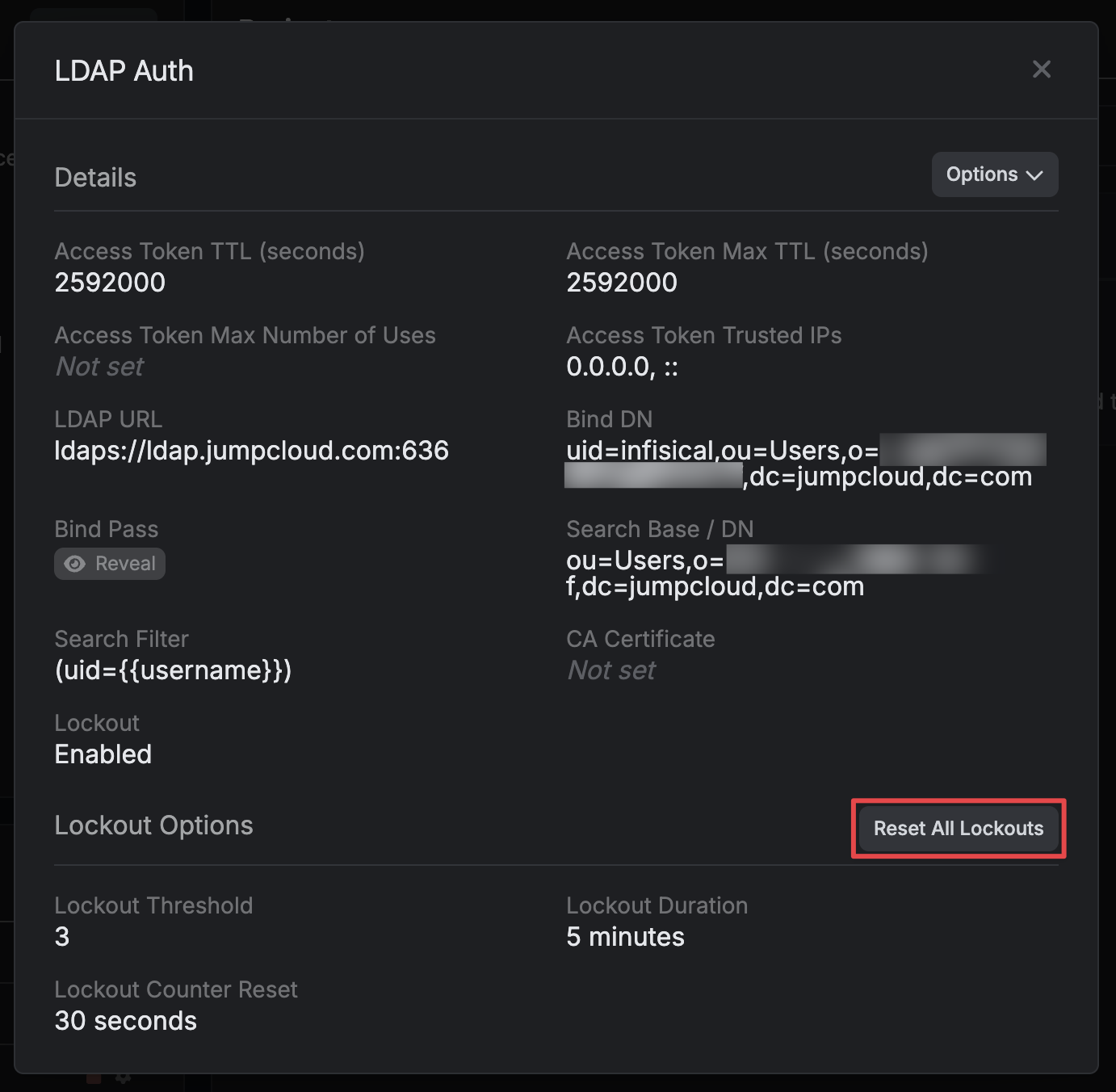
After selecting LDAP Auth, you’ll see the form you need to fill out to configure LDAP auth for your identity. The following fields are available:Configuration TabURL: The LDAP server to connect to such asldap://ldap.your-org.com,ldaps://ldap.myorg.com:636(for connection over SSL/TLS), etc.Bind DN: The DN to bind to the LDAP server with.Bind Pass: The password to bind to the LDAP server with.Search Base / DN: Base DN under which to perform user search such asou=Users,dc=acme,dc=com.User Search Filter: Template used to construct the LDAP user search filter such as(uid={{username}}); use literal{{username}}to have the given username used in the search. The default is(uid={{username}})which is compatible with several common directory schemas.Required Attributes: A key/value pair of attributes that must be present in the LDAP user entry for them to be authenticated. As an example, if you set keyuidto valueuser1,user2,user3, then only users withuidofuser1,user2, oruser3will be able to login with this identity. Each value is a comma separated list of attributes.Access Token TTL(default is 2592000 equivalent to 30 days): The lifetime for an access token in seconds. This value will be referenced at renewal time.Access Token Max TTL(default is 2592000 equivalent to 30 days): The maximum lifetime for an access token in seconds. This value will be referenced at renewal time.Access Token Max Number of Uses(default is 0): The maximum number of times that an access token can be used; a value of 0 implies infinite number of uses.
Lockout(enabled by default): The lockout feature will temporarily block login attempts after X consecutive login failures.Lockout Threshold(default is 3): The amount of times login must fail before locking the identity auth method.Lockout Duration(default is 5 minutes): How long an identity auth method lockout lasts.Lockout Counter Reset(default is 30 seconds): How long to wait from the most recent failed login until resetting the lockout counter.
CA Certificate: The CA certificate to use when verifying the LDAP server certificate. This field is optional but recommended.Access Token Trusted IPs: The IPs or CIDR ranges that access tokens can be used from. By default, each token is given the 0.0.0.0/0, allowing usage from any network address.

Authenticating with the identity
After configuring LDAP auth for your identity, you can authenticate with the identity and obtain an access token using your LDAP credentials.If successful, you’ll receive an access token in the response body.You can read more about the login API endpoint here.
For EU Cloud and Self-Hosted users, make sure to replace
https://app.infisical.com with https://eu.infisical.com or your self-hosted instance’s URL in the request URL.How do I reset a lockout?
How do I reset a lockout?
You can reset (remove) all lockouts for an identity auth method by clicking into the auth method and pressing Reset All Lockouts.