Diagram
The following sequence diagram illustrates the Kubernetes Auth workflow for authenticating applications running in pods with Infisical.Concept
At a high-level, Infisical authenticates an application in Kubernetes by verifying its identity and checking that it meets specific requirements (e.g. it is bound to an allowed service account) at the/api/v1/auth/kubernetes-auth/login endpoint. If successful,
then Infisical returns a short-lived access token that can be used to make authenticated requests to the Infisical API.
To be more specific:
- The application deployed on Kubernetes retrieves its service account credential that is a JWT token at the
/var/run/secrets/kubernetes.io/serviceaccount/tokenpod path. - The application sends the JWT token to Infisical at the
/api/v1/auth/kubernetes-auth/loginendpoint after which Infisical forwards the JWT token to the Kubernetes API Server at the TokenReview API for verification and to obtain the service account information associated with the JWT token. Infisical is able to authenticate and interact with the TokenReview API by using either the long lived JWT token set while configuring this authentication method or by using the incoming token itself. The JWT token mentioned in this context is referred as the token reviewer JWT token. - Infisical checks the service account properties against set criteria such Allowed Service Account Names and Allowed Namespaces.
- If all is well, Infisical returns a short-lived access token that the application can use to make authenticated requests to the Infisical API.
We recommend using one of Infisical’s clients like SDKs or the Infisical Agent
to authenticate with Infisical using Kubernetes Auth as they handle the
authentication process including service account credential retrieval for you.
Guide
In the following steps, we explore how to create and use identities for your applications in Kubernetes to access the Infisical API using the Kubernetes Auth authentication method.Obtaining the token reviewer JWT for Infisical
Option 1: Reviewer JWT Token
Option 1: Reviewer JWT Token
When to use this option: Choose this approach when you want centralized authentication management. Only one service account needs special permissions, and your application service accounts remain unchanged.
infisical-service-account.yaml
system:auth-delegator cluster role. As described here, this role allows delegated authentication and authorization checks, specifically for Infisical to access the TokenReview API. You can apply the following configuration file:cluster-role-binding.yaml
Secret resource:service-account-token.yaml
Option 2: Client JWT as Reviewer JWT Token
Option 2: Client JWT as Reviewer JWT Token
When to use this option: Choose this approach to eliminate long-lived tokens. This option simplifies Infisical configuration but requires each application service account to have elevated permissions.
system:auth-delegator role:client-role-binding.yaml
Option 3: Use Gateway as Reviewer
Option 3: Use Gateway as Reviewer
When to use this option: Choose this approach when you have a gateway deployed in your Kubernetes Cluster and wish to eliminate long-lived tokens. This approach simplifies Infisical Kubernetes Auth configuration, and only one service account will need to have the elevated
system:auth-delegator ClusterRole binding.Note: Gateway is a paid feature. - Infisical Cloud users: Gateway is
available under the Enterprise Tier. - Self-Hosted Infisical: Please
contact sales@infisical.com to purchase an
enterprise license.
Deploying a gateway
To deploy a gateway in your Kubernetes cluster, follow our Gateway deployment guide using helm.
Grant the gateway the system:auth-delegator ClusterRole binding
To grant the gateway the
system:auth-delegator ClusterRole binding, you can use the following command:gateway-role-binding.yaml
Creating an identity
To create an identity, head to your Organization Settings > Access Control > Identities and press Create identity. When creating an identity, you specify an organization level role for it to assume; you can configure roles in Organization Settings > Access Control > Organization Roles.
When creating an identity, you specify an organization level role for it to assume; you can configure roles in Organization Settings > Access Control > Organization Roles. Now input a few details for your new identity. Here’s some guidance for each field:
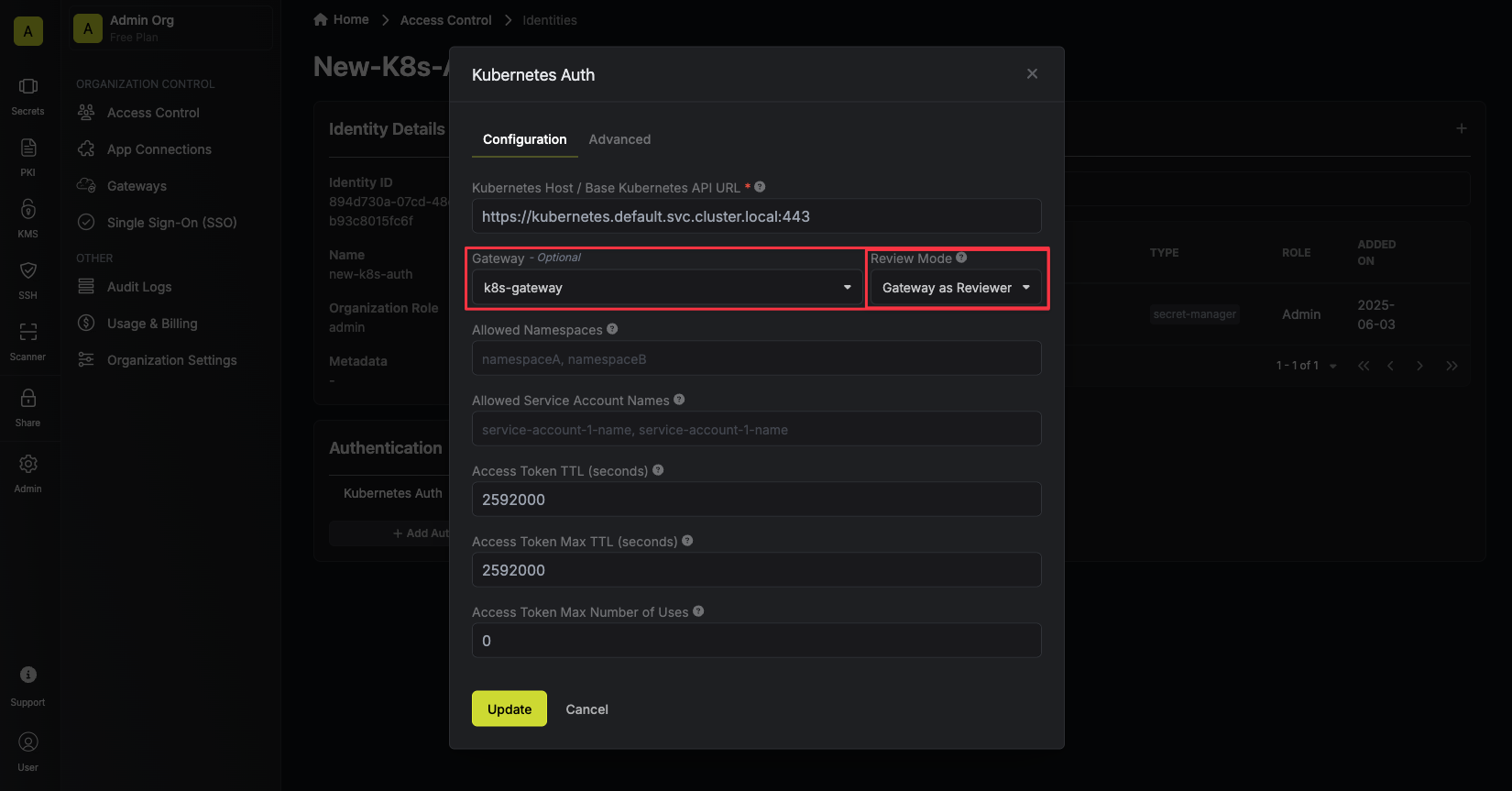
Now input a few details for your new identity. Here’s some guidance for each field: Since the identity has been configured with Universal Auth by default, you should re-configure it to use Kubernetes Auth instead. To do this, press to edit the Authentication section,
remove the existing Universal Auth configuration, and add a new Kubernetes Auth configuration onto the identity.
Since the identity has been configured with Universal Auth by default, you should re-configure it to use Kubernetes Auth instead. To do this, press to edit the Authentication section,
remove the existing Universal Auth configuration, and add a new Kubernetes Auth configuration onto the identity.
 Here’s some more guidance on each field:
Here’s some more guidance on each field:
 When creating an identity, you specify an organization level role for it to assume; you can configure roles in Organization Settings > Access Control > Organization Roles.
When creating an identity, you specify an organization level role for it to assume; you can configure roles in Organization Settings > Access Control > Organization Roles. Now input a few details for your new identity. Here’s some guidance for each field:
Now input a few details for your new identity. Here’s some guidance for each field:- Name (required): A friendly name for the identity.
- Role (required): A role from the Organization Roles tab for the identity to assume. The organization role assigned will determine what organization level resources this identity can have access to.
 Since the identity has been configured with Universal Auth by default, you should re-configure it to use Kubernetes Auth instead. To do this, press to edit the Authentication section,
remove the existing Universal Auth configuration, and add a new Kubernetes Auth configuration onto the identity.
Since the identity has been configured with Universal Auth by default, you should re-configure it to use Kubernetes Auth instead. To do this, press to edit the Authentication section,
remove the existing Universal Auth configuration, and add a new Kubernetes Auth configuration onto the identity.
 Here’s some more guidance on each field:
Here’s some more guidance on each field:- Kubernetes Host / Base Kubernetes API URL: The host string, host:port pair, or URL to the base of the Kubernetes API server. This can usually be obtained by running
kubectl cluster-info. - Token Reviewer JWT: A long-lived service account JWT token for Infisical to access the TokenReview API to validate other service account JWT tokens submitted by applications/pods. This is the JWT token obtained from step 1.5(Reviewer Tab). If omitted, the client’s own JWT will be used instead, which requires the client to have the
system:auth-delegatorClusterRole binding. This is shown in step 1, option 2. - Allowed Service Account Names: A comma-separated list of trusted service account names that are allowed to authenticate with Infisical.
- Allowed Namespaces: A comma-separated list of trusted namespaces that service accounts must belong to authenticate with Infisical.
- Allowed Audience: An optional audience claim that the service account JWT token must have to authenticate with Infisical.
- CA Certificate: The PEM-encoded CA cert for the Kubernetes API server. This is used by the TLS client for secure communication with the Kubernetes API server.
- Access Token TTL (default is
2592000equivalent to 30 days): The lifetime for an acccess token in seconds. This value will be referenced at renewal time. - Access Token Max TTL (default is
2592000equivalent to 30 days): The maximum lifetime for an acccess token in seconds. This value will be referenced at renewal time. - Access Token Max Number of Uses (default is
0): The maximum number of times that an access token can be used; a value of0implies infinite number of uses. - Access Token Trusted IPs: The IPs or CIDR ranges that access tokens can be used from. By default, each token is given the
0.0.0.0/0, allowing usage from any network address.
Adding an identity to a project
To enable the identity to access project-level resources such as secrets within a specific project, you should add it to that project.To do this, head over to the project you want to add the identity to and go to Project Settings > Access Control > Machine Identities and press Add identity.Next, select the identity you want to add to the project and the project level role you want to allow it to assume. The project role assigned will determine what project level resources this identity can have access to.



Accessing the Infisical API with the identity
To access the Infisical API as the identity, you should first make sure that the pod running your application is bound to a service account specified in the Allowed Service Account Names field of the identity’s Kubernetes Auth authentication method configuration in step 2.Once bound, the pod will receive automatically mounted service account credentials that is a JWT token at the
/var/run/secrets/kubernetes.io/serviceaccount/token path. This token should be used to authenticate with Infisical at the /api/v1/auth/kubernetes-auth/login endpoint.For information on how to configure sevice accounts for pods, refer to the guide here.We provide a code example below of how you might retrieve the JWT token and use it to authenticate with Infisical to gain access to the Infisical API.Sample code for inside an application
Sample code for inside an application
The shown example uses Node.js but you can use any other language to retrieve the service account JWT token and use it to authenticate with Infisical.
Each identity access token has a time-to-live (TTL) which you can infer from the response of the login operation;
the default TTL is
7200 seconds which can be adjusted.If an identity access token exceeds its max ttl, it can no longer authenticate with the Infisical API. In this case,
a new access token should be obtained by performing another login operation.Why is the Infisical API rejecting my service account JWT token?
Why is the Infisical API rejecting my service account JWT token?
There are a few reasons for why this might happen:
- The Kubernetes Auth authentication method configuration is invalid.
- The service account JWT token has expired is malformed or invalid.
- The service account associated with the JWT token does not meet the criteria set forth in the Kubernetes Auth authentication method configuration such as Allowed Service Account Names and Allowed Namespaces.
Why is the Infisical API rejecting my access token?
Why is the Infisical API rejecting my access token?
There are a few reasons for why this might happen:
- The access token has expired.
- The identity is insufficiently permissioned to interact with the resources you wish to access.
- The client access token is being used from an untrusted IP.
What is access token renewal and TTL/Max TTL?
What is access token renewal and TTL/Max TTL?
A identity access token can have a time-to-live (TTL) or incremental lifetime after which it expires.In certain cases, you may want to extend the lifespan of an access token; to do so, you must set a max TTL parameter.A token can be renewed any number of times where each call to renew it can extend the token’s lifetime by increments of the access token’s TTL.
Regardless of how frequently an access token is renewed, its lifespan remains bound to the maximum TTL determined at its creation.