Prepare AWS CloudHSM Cluster
Before you get started, you’ll need to configure a AWS CloudHSM cluster which meets the following criteria:- The cluster must be active.
- The cluster must not be associated with any other AWS KMS custom key store.
- The cluster must be configured with private subnets in at least two Availability Zones in the Region.
- The security group for the cluster must include inbound and outbound rules that allow TCP traffic on ports 2223-2225.
- The cluster must contain at least two active HSMs in different Availability Zones.
Set Up AWS KMS Custom Key Store
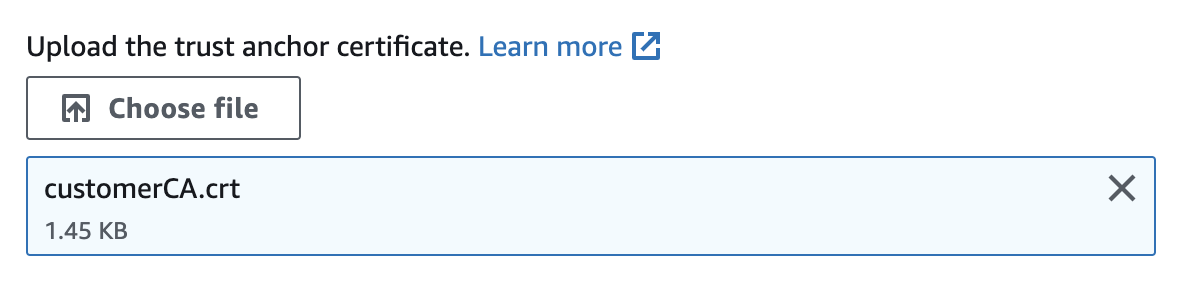
To set up an AWS KMS custom key store with AWS CloudHSM, you will need the following:- The trust anchor certificate of your AWS CloudHSM cluster.
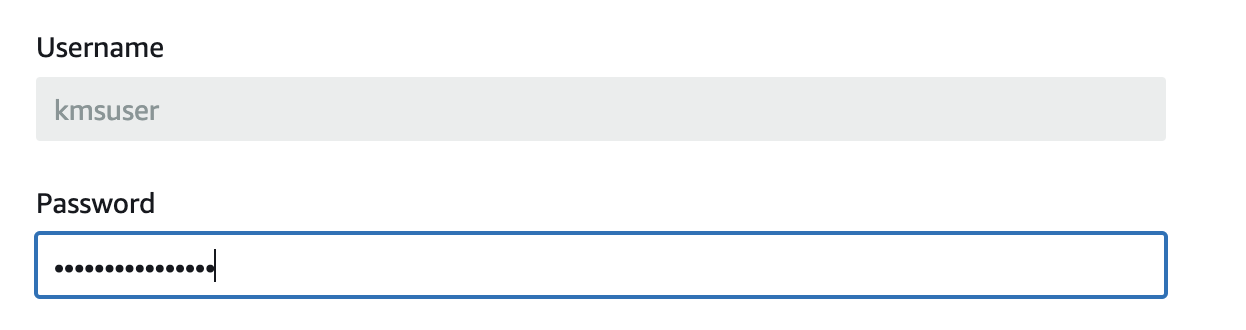
- A
kmsuseruser in the AWS CloudHSM cluster with the crypto-user role.
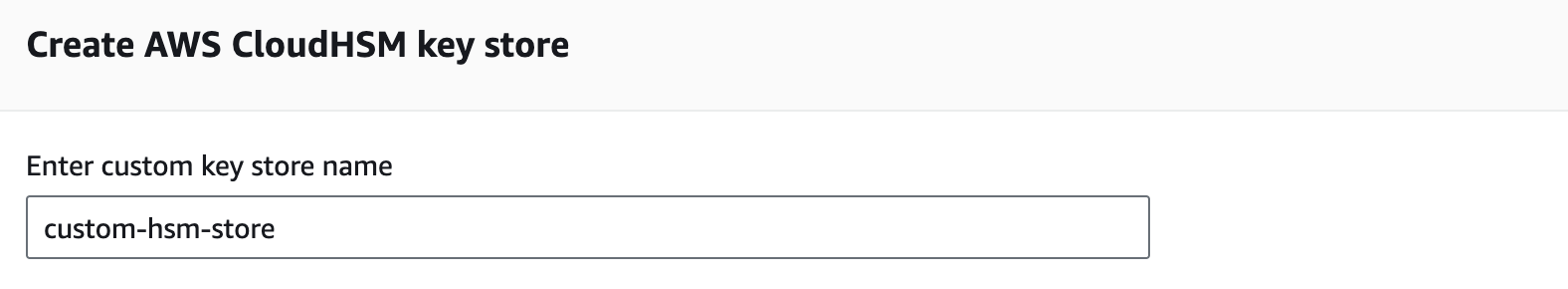
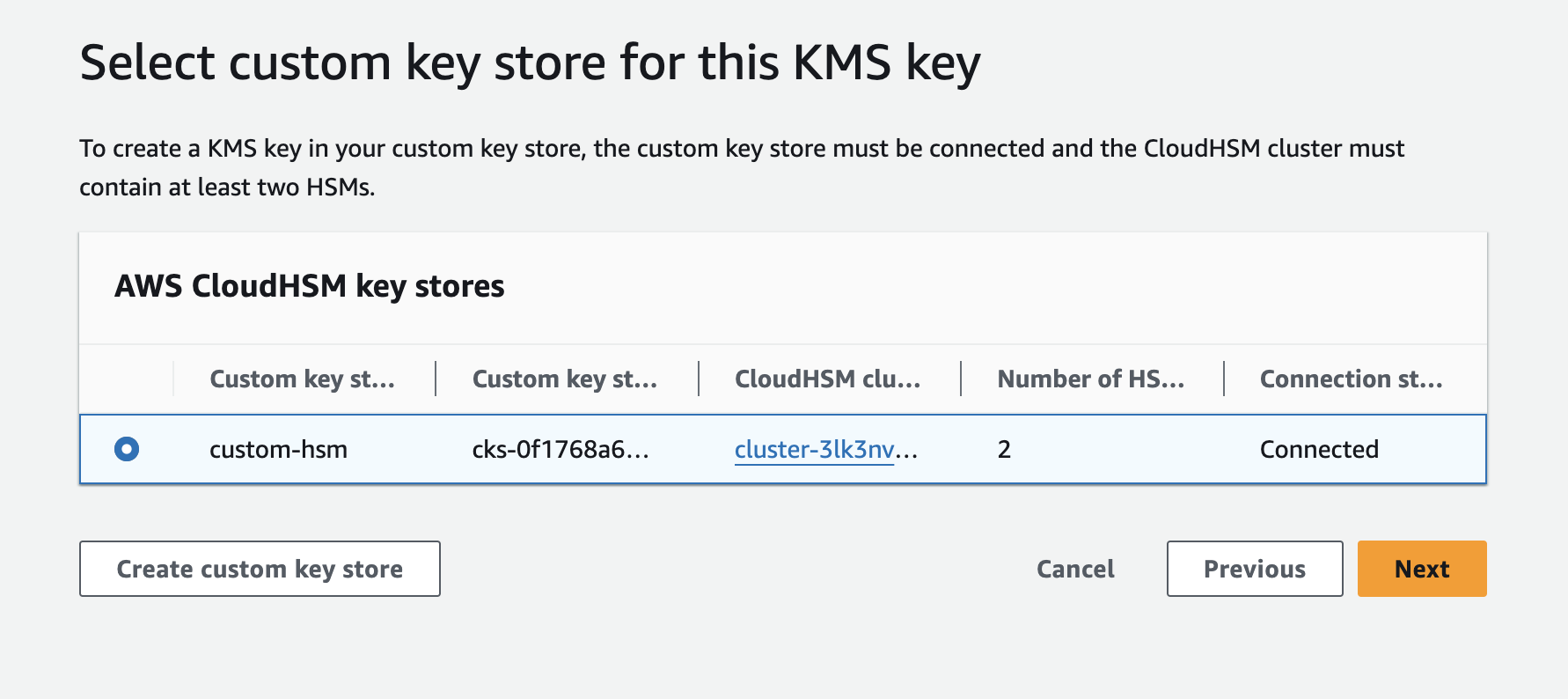
Navigate to Key store creation page
In the AWS console, head over to
AWS KMS > AWS CloudHSM key stores and click Create key store.Select HSM cluster
Select the AWS CloudHSM cluster. You should be able to select the cluster if it meets the required criteria mentioned above.

Create AWS KMS Key
Next, you’ll need to create a AWS KMS key where you will set the key store you created previously.Navigate to AWS KMS key creation page
In your AWS console, proceed to
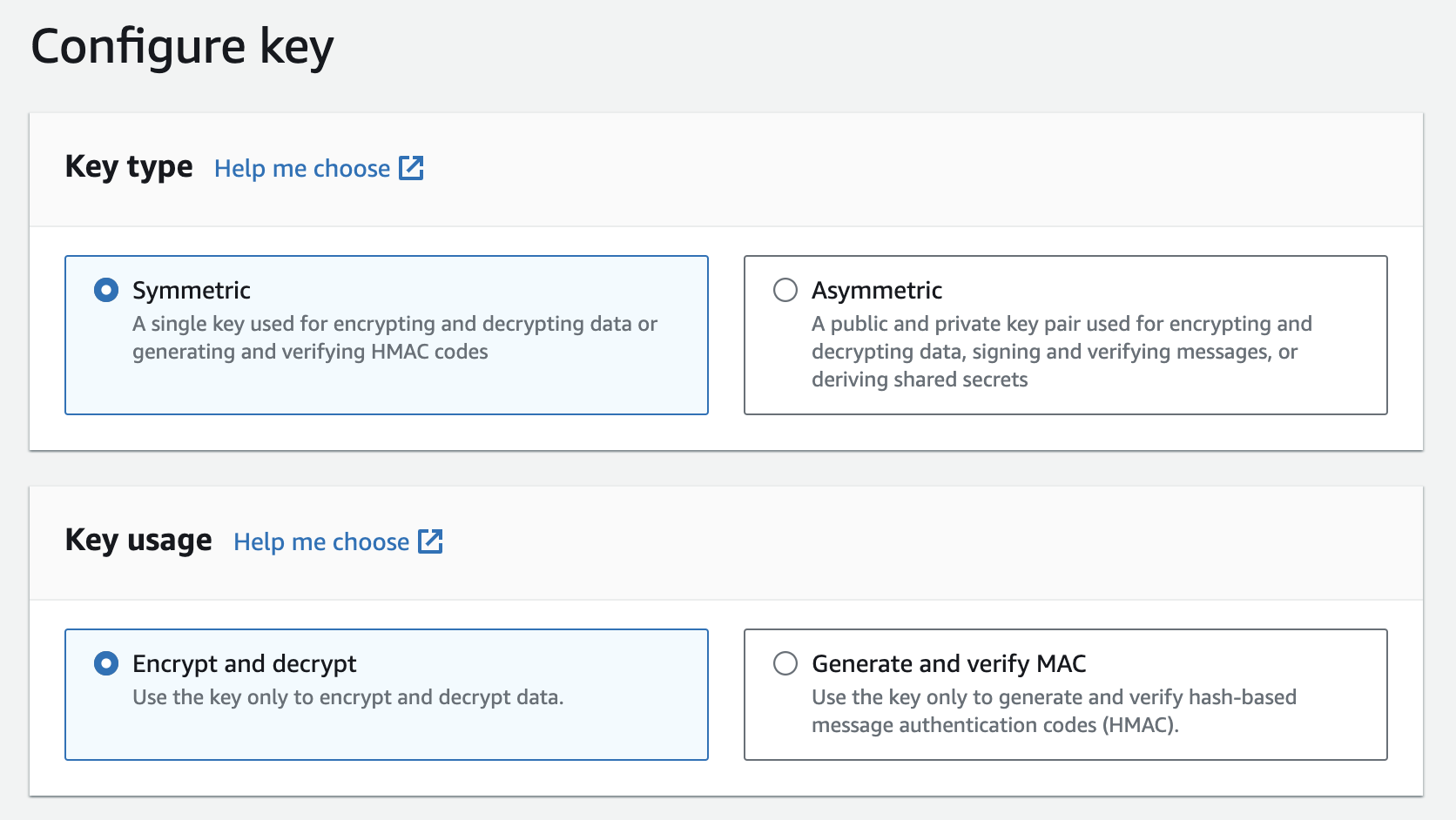
AWS KMS > Customer managed keys and click Create.Select key material origin
In the advanced options, for the Key material origin field, select 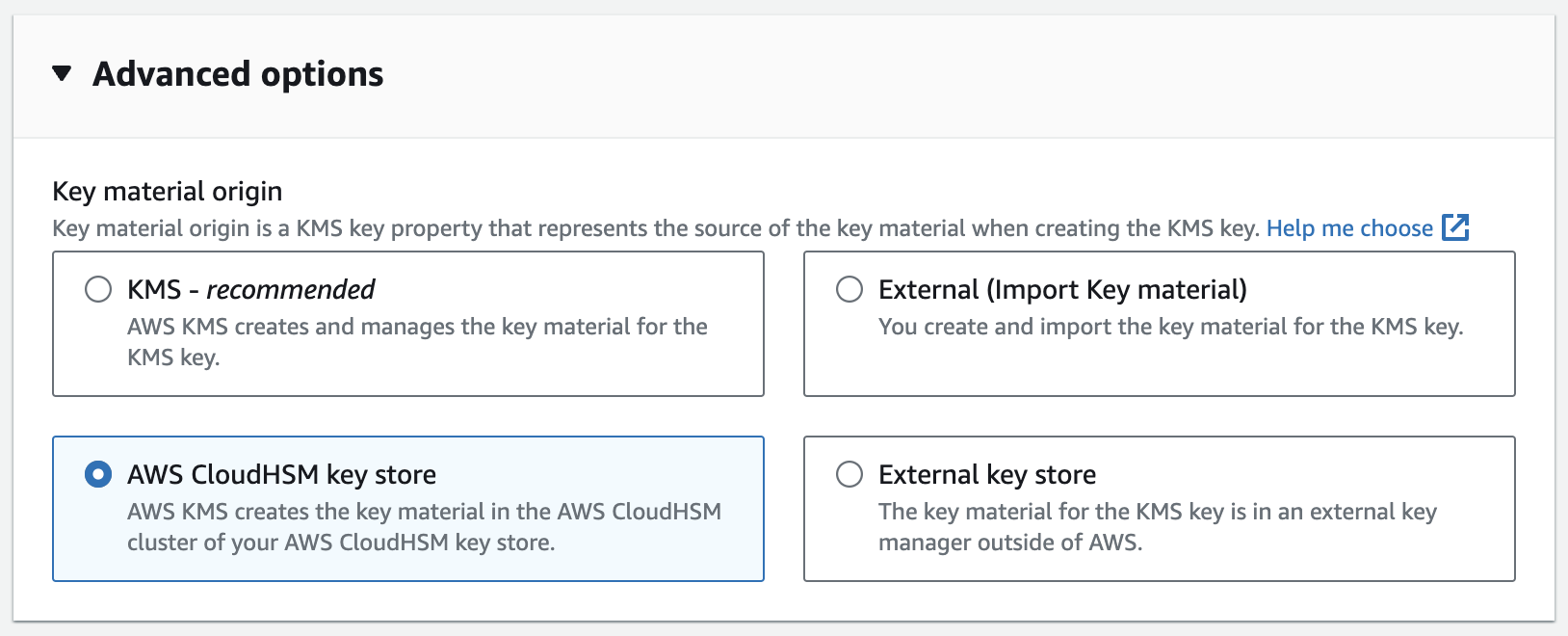
AWS CloudHSM key store. Then, click next.