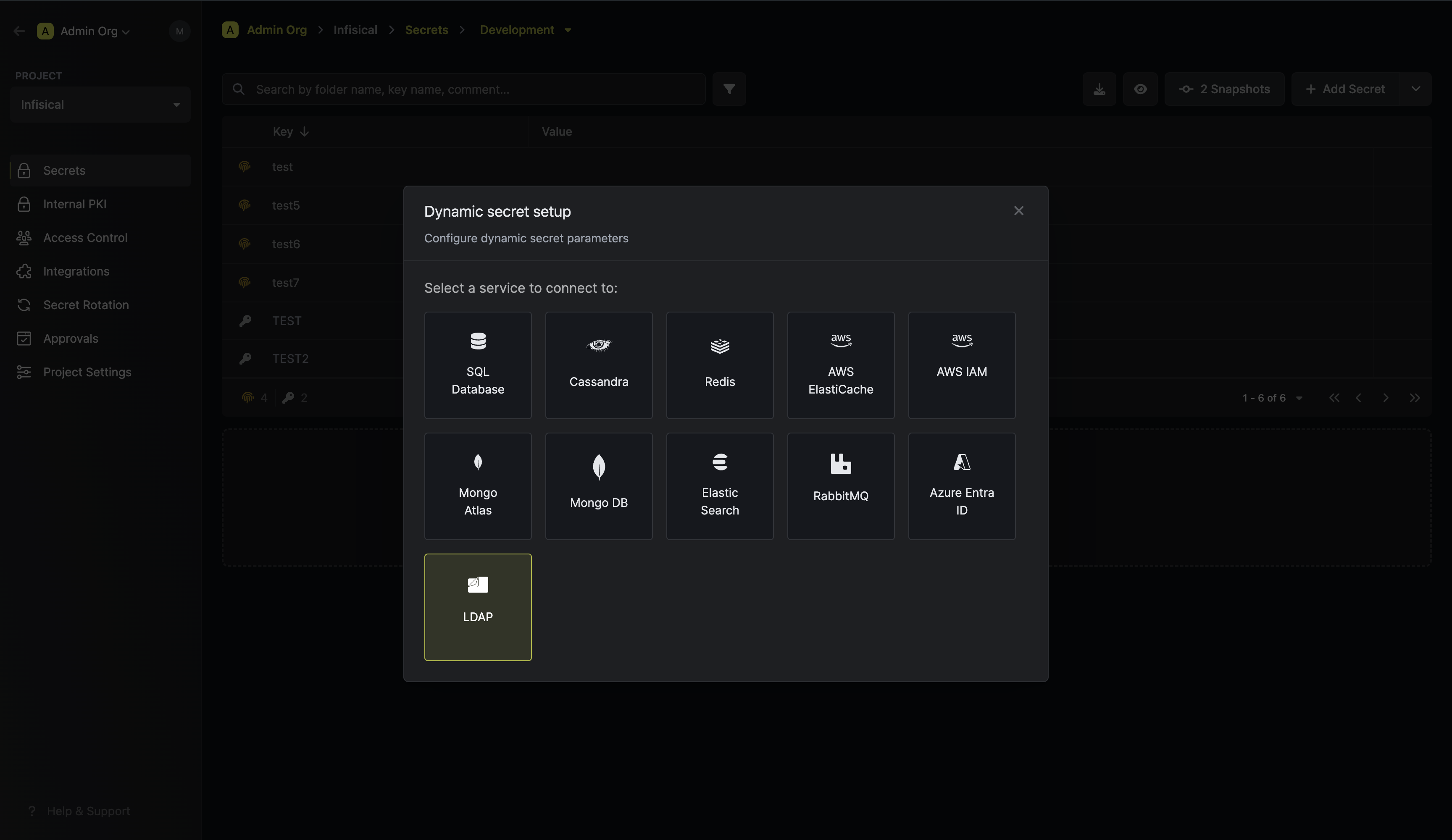
Prerequisites
- Create a user with the necessary permissions to create users in your LDAP server.
- Ensure your LDAP server is reachable via Infisical instance.
Create LDAP Credentials
- Dynamic
- Static
Open Secret Overview Dashboard
Open the Secret Overview dashboard and select the environment in which you would like to add a dynamic secret.
Provide the inputs for dynamic secret parameters
Name by which you want the secret to be referenced
Default time-to-live for a generated secret (it is possible to modify this value after a secret is generated)
Maximum time-to-live for a generated secret.
LDAP url to connect to. (Example: ldap://your-ldap-ip:389 or ldaps://domain:636)
DN to bind to. This should have permissions to create a new users.
Password for the given DN.
CA certificate to use for TLS in case of a secure connection.
The type of LDAP credential - select Dynamic.
LDIF to run while creating a user in LDAP. This can include extra steps to assign the user to groups or set permissions.
Here Active Directory Example:
{{Username}}, {{Password}} and {{EncodedPassword}} are templatized variables for the username and password generated by the dynamic secret.{{EncodedPassword}} is the encoded password required for the unicodePwd field in Active Directory as described here.OpenLDAP Example:LDIF to run while revoking a user in LDAP. This can include extra steps to remove the user from groups or set permissions.
Here
{{Username}} is a templatized variable for the username generated by the dynamic secret.OpenLDAP / Active Directory Example:LDIF to run incase Creation LDIF fails midway.For the creation example shown above, if the user is created successfully but not added to a group, this LDIF can be used to remove the user.
Here
{{Username}}, {{Password}} and {{EncodedPassword}} are templatized variables for the username generated by the dynamic secret.OpenLDAP / Active Directory Example:Specifies a template for generating usernames. This field allows customization of how usernames are automatically created.Allowed template variables are:
{{randomUsername}}: Random username string.{{unixTimestamp}}: Current Unix timestamp at the time of lease creation.{{identity.name}}: Name of the identity that is generating the lease.{{dynamicSecret.name}}: Name of the associated dynamic secret.{{dynamicSecret.type}}: Type of the associated dynamic secret.{{random N}}: Random string of N characters.
truncate: Truncates a string to a specified length.replace: Replaces a substring with another value.uppercase: Converts a string to uppercase.lowercase: Converts a string to lowercase.
Generate dynamic secrets
Once you’ve successfully configured the dynamic secret, you’re ready to generate on-demand credentials.
To do this, simply click on the ‘Generate’ button which appears when hovering over the dynamic secret item.
Alternatively, you can initiate the creation of a new lease by selecting ‘New Lease’ from the dynamic secret lease list section.
 When generating these secrets, it’s important to specify a Time-to-Live (TTL) duration. This will dictate how long the credentials are valid for.
When generating these secrets, it’s important to specify a Time-to-Live (TTL) duration. This will dictate how long the credentials are valid for. Once you click the
Once you click the 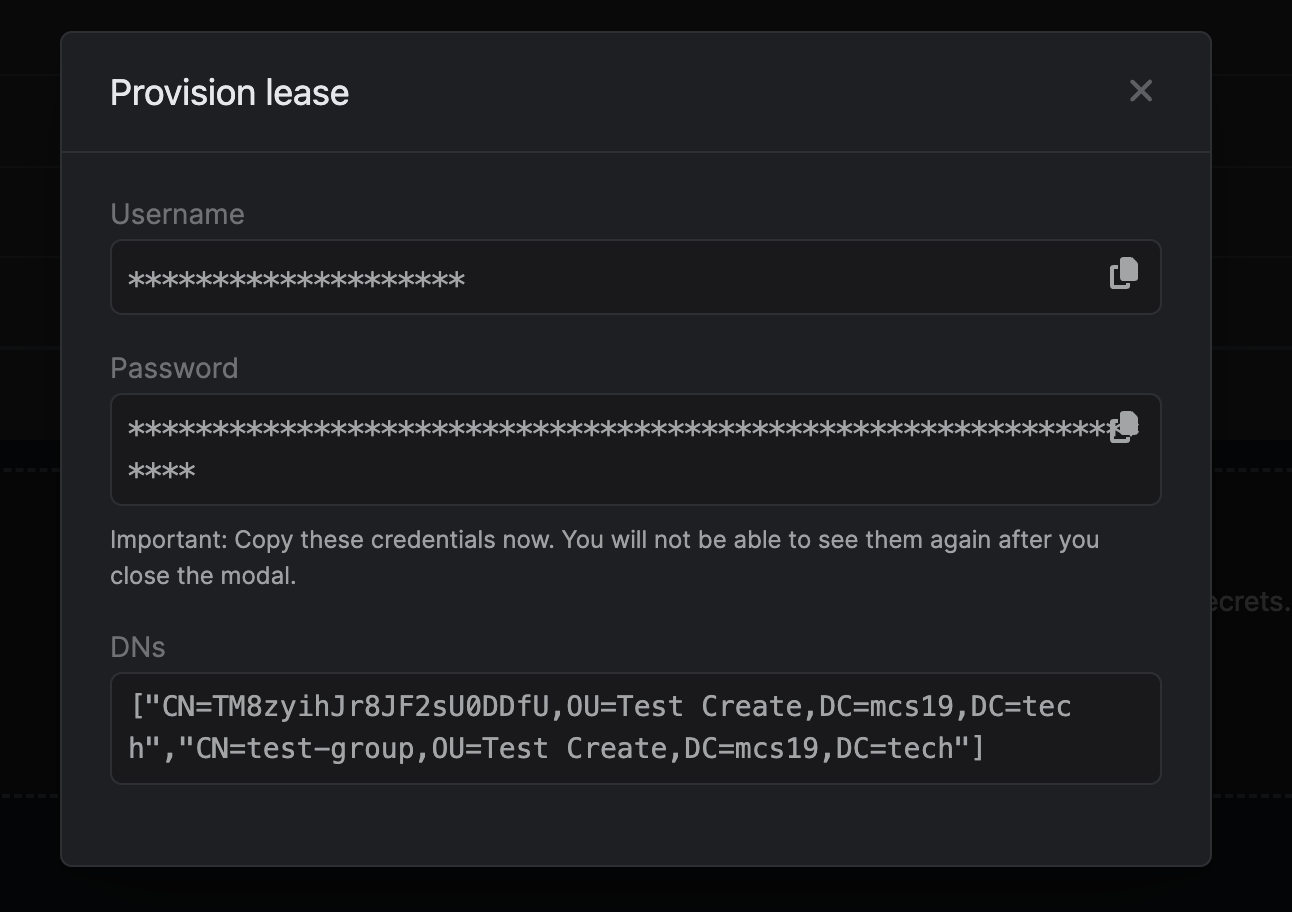

 When generating these secrets, it’s important to specify a Time-to-Live (TTL) duration. This will dictate how long the credentials are valid for.
When generating these secrets, it’s important to specify a Time-to-Live (TTL) duration. This will dictate how long the credentials are valid for. Once you click the
Once you click the Submit button, a new secret lease will be generated and the credentials from it will be shown to you with an array of DN’s altered depending on the Creation LDIF.
Active Directory Integration
- Passwords in Active Directory are set using the
unicodePwdfield. This must be proceeded by two colons::as shown in the example. Source - Active directory uses the
userAccountControlfield to enable account. Read MoreuserAccountControlset to512enables a user.- To disable AD’s password expiration for this dynamic user account. The
userAccountControlvalue for this is:65536. - Since
userAccountControlflag is cumulative set it to512 + 65536=66048to do both.
- Active Directory does not permit direct modification of a user’s
memberOfattribute. The member attribute of a group and thememberOfattribute of a user are linked attributes, where the member attribute represents the forward link, which can be modified. In the context of AD group membership, the group’smemberattribute serves as the forward link. Therefore, to add a newly created dynamic user to a group, a modification request must be issued to the desired group, updating its membership to include the new user.
LDIF Entries
User account management is handled through LDIF entries.Things to Remember
- No trailing spaces: Ensure there are no trailing spaces on any line, including blank lines.
- Empty lines before modify blocks: Every modify block must be preceded by an empty line.
- Multiple modifications: You can define multiple modifications for a DN within a single modify block. Each modification should end with a single dash (
-).