Setting Metadata on Machine Identities
- Manually Configure Metadata
Accessing Attributes From Machine Identity Login
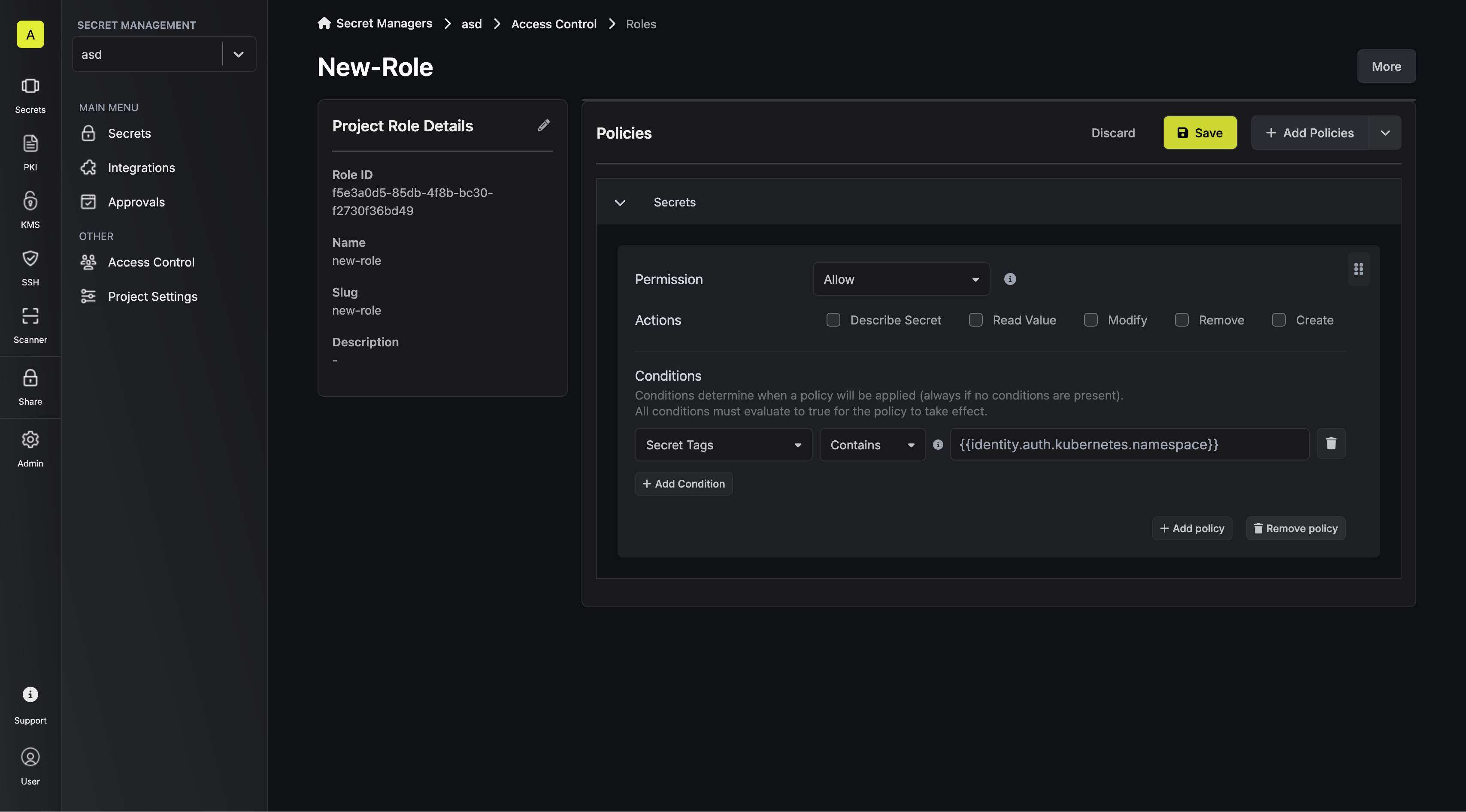
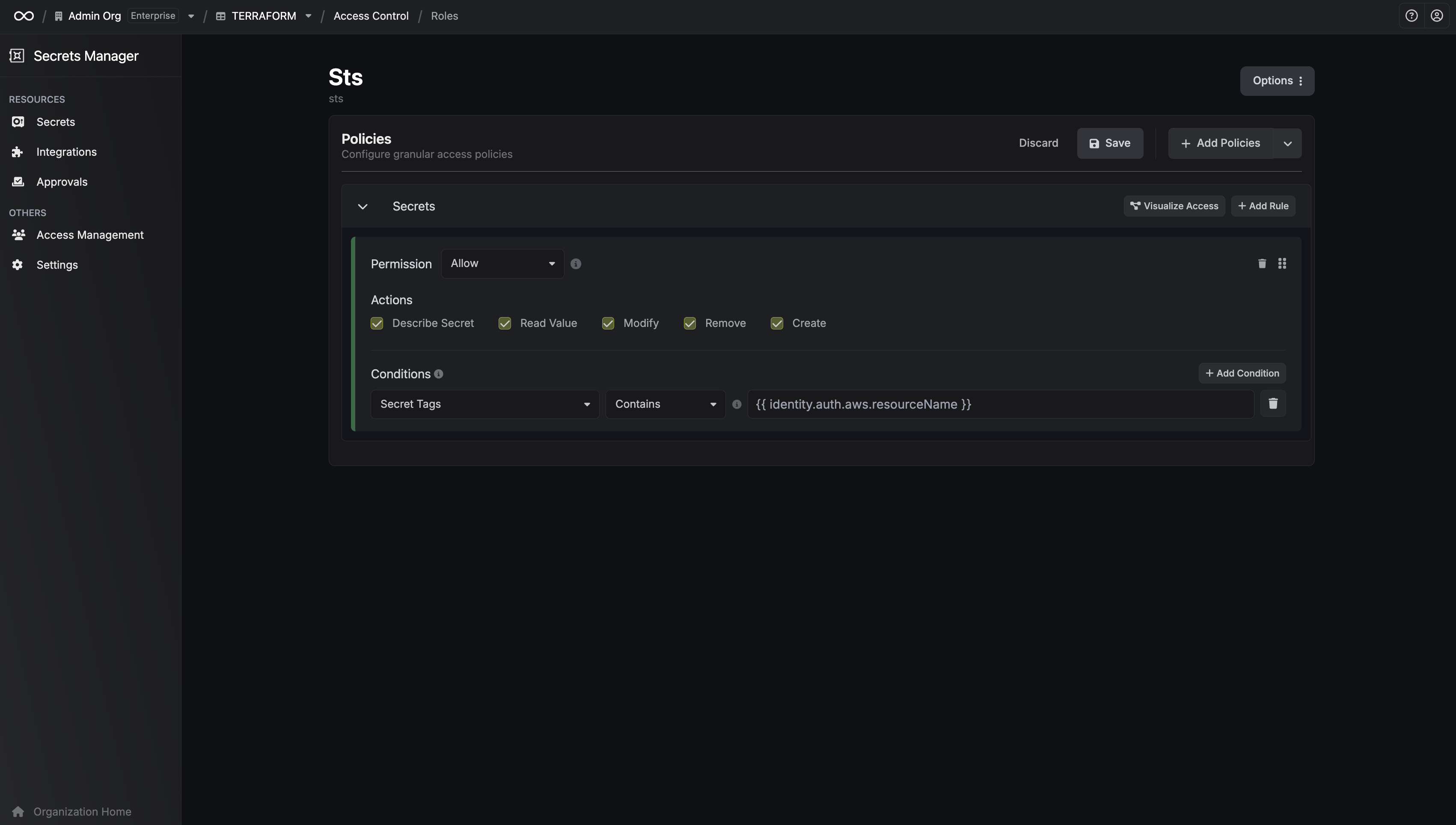
When machine identities authenticate, they may receive additional payloads/attributes from the service provider. For methods like OIDC, these come as claims in the token and can be made available in your policies.- OIDC Login Attributes
- Kubernetes Login Attributes
- AWS Attributes
- Other Authentication Method Attributes
- Navigate to the Identity Authentication settings and select the OIDC Auth Method.
- In the Advanced section, locate the Claim Mapping configuration.
- Map the OIDC claims to permission attributes by specifying:
- Attribute Name: The identifier to be used in your policies (e.g., department).
- Claim Path: The dot notation path to the claim in the OIDC token (e.g., user.department).
- department: to
user.department - role: to
user.role