Rotation Type: Dual-PhaseThis rotation maintains two active credential sets with overlapping validity, ensuring zero-downtime during rotation cycles.
Prerequisites
- Create an AWS Connection with the required Secret Rotation permissions
-
Make sure to add the following permissions to your IAM Role/IAM User Permission policy set used by your AWS Connection:
Workflow
The typical workflow for using the AWS IAM User rotation strategy consists of four steps:- Creating the target IAM user whose credentials you wish to rotate.
- Configuring the rotation strategy in Infisical with the credentials of the managing IAM user.
- Pressing the Rotate button in the Infisical dashboard to trigger the rotation of the target IAM user’s credentials. The strategy can also be configured to rotate the credentials automatically at a specified interval.
Create the target IAM user
To begin, create an IAM user whose credentials you wish to rotate. If you already have an IAM user,
then you can skip this step.
Configure the AWS IAM User secret rotation strategy in Infisical
- Infisical UI
- API
-
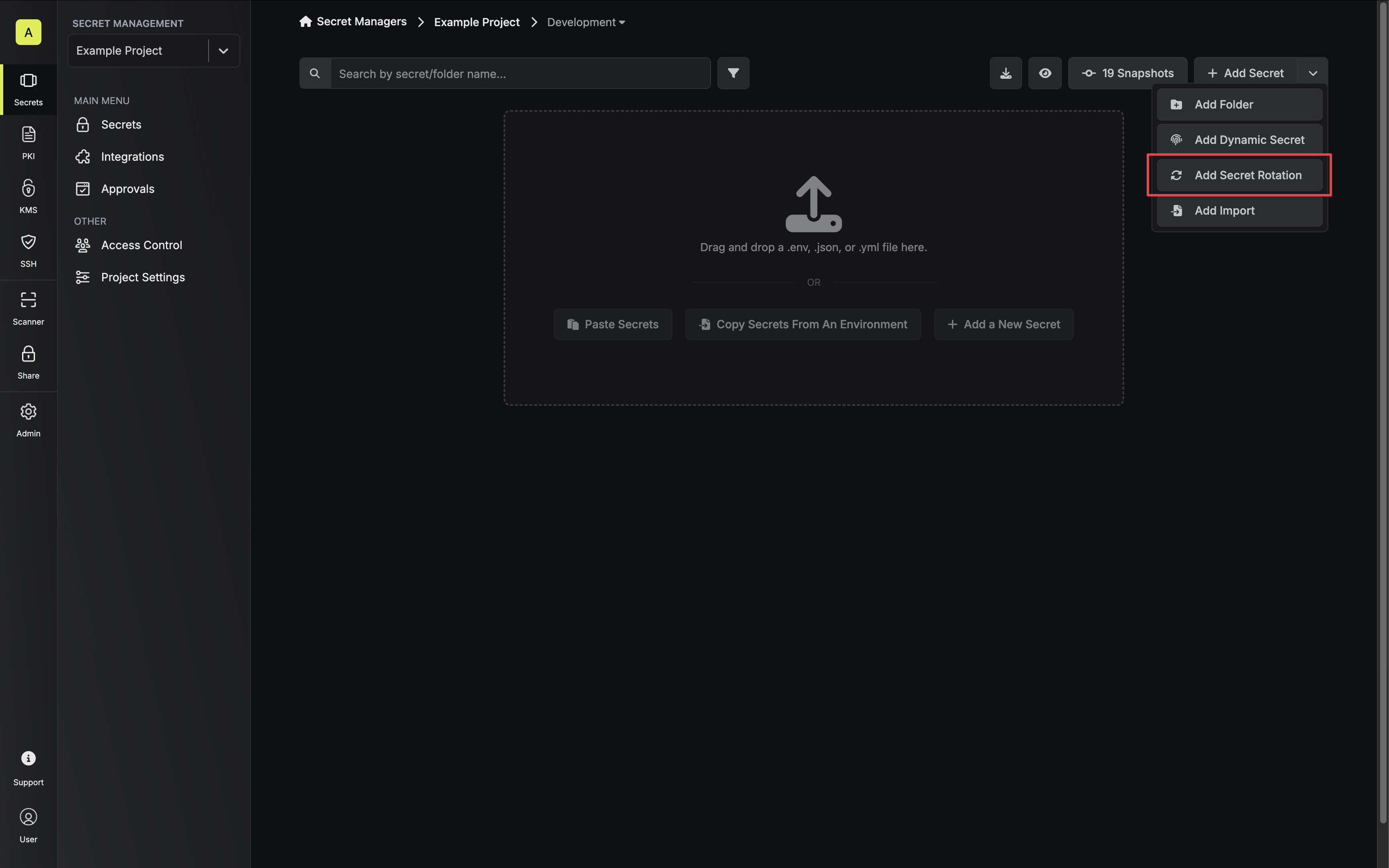
Navigate to your Secret Manager Project’s Dashboard and select Add Secret Rotation from the actions dropdown.
-
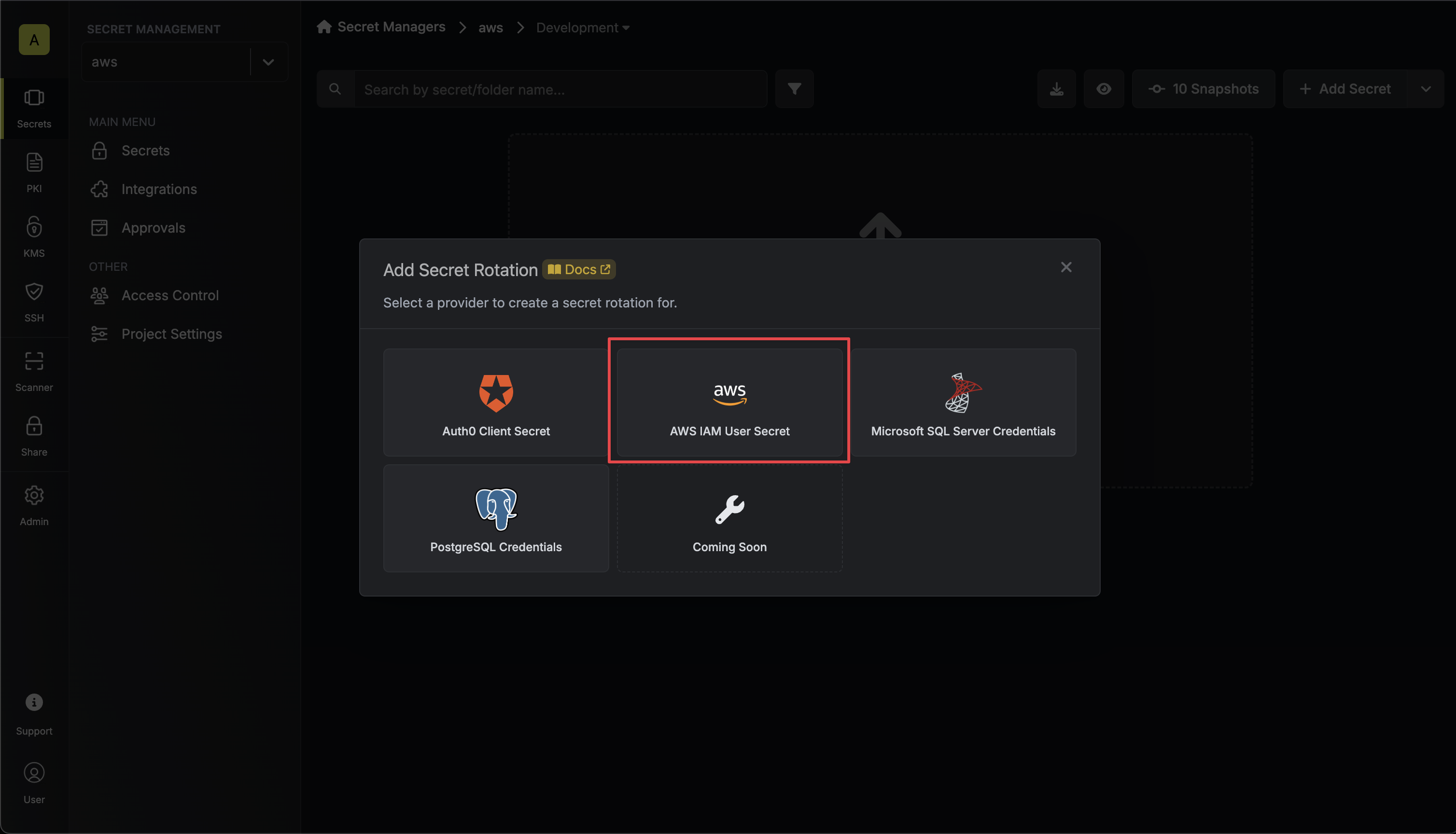
Select the AWS IAM User Secret option.
-
Select the AWS Connection to use and configure the rotation behavior. Then click Next.
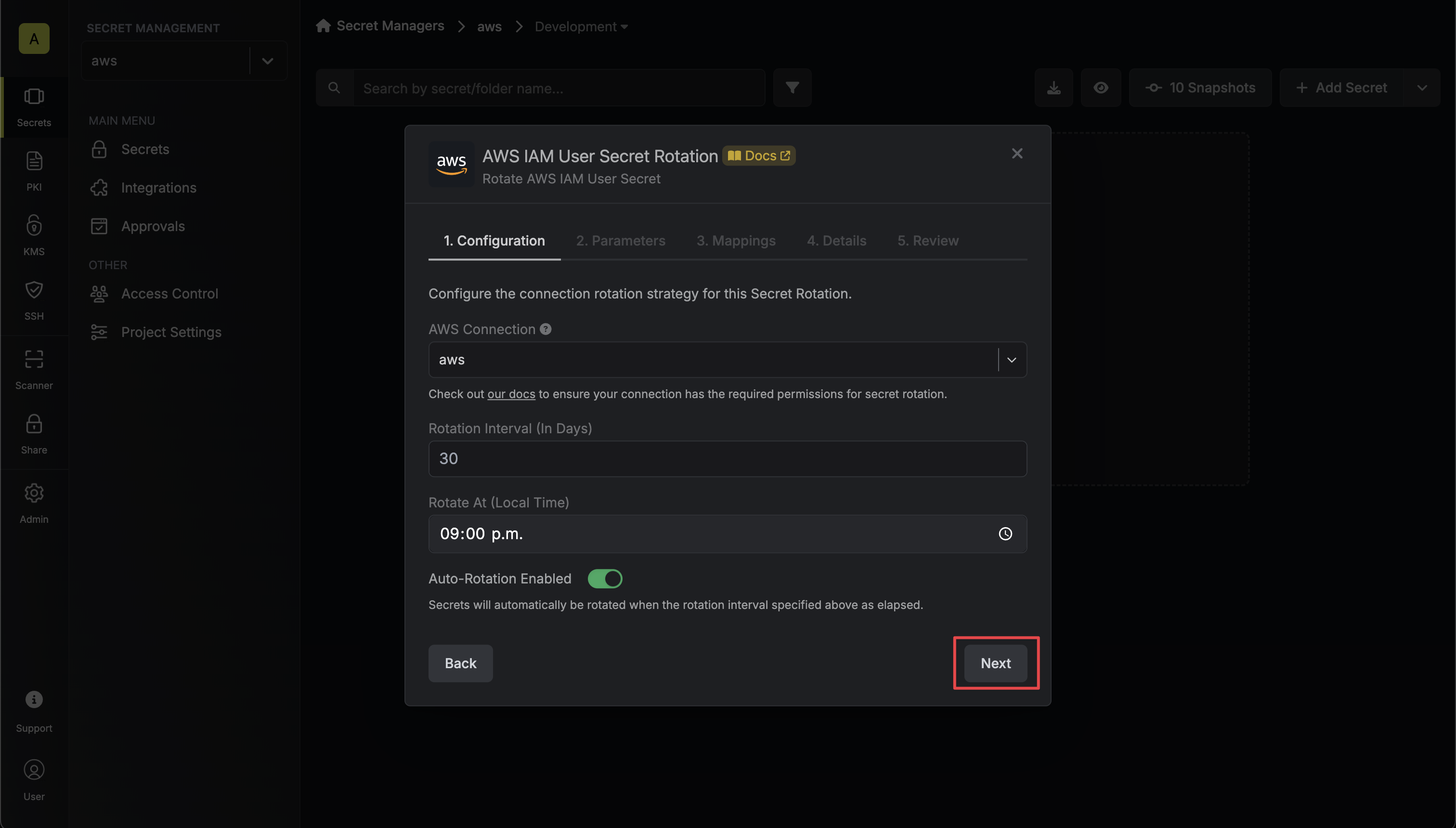
- AWS Connection - the connection that will perform the rotation of the specified application’s Client Secret.
- Rotation Interval - the interval, in days, that once elapsed will trigger a rotation.
- Rotate At - the local time of day when rotation should occur once the interval has elapsed.
- Auto-Rotation Enabled - whether secrets should automatically be rotated once the rotation interval has elapsed. Disable this option to manually rotate secrets or pause secret rotation.
-
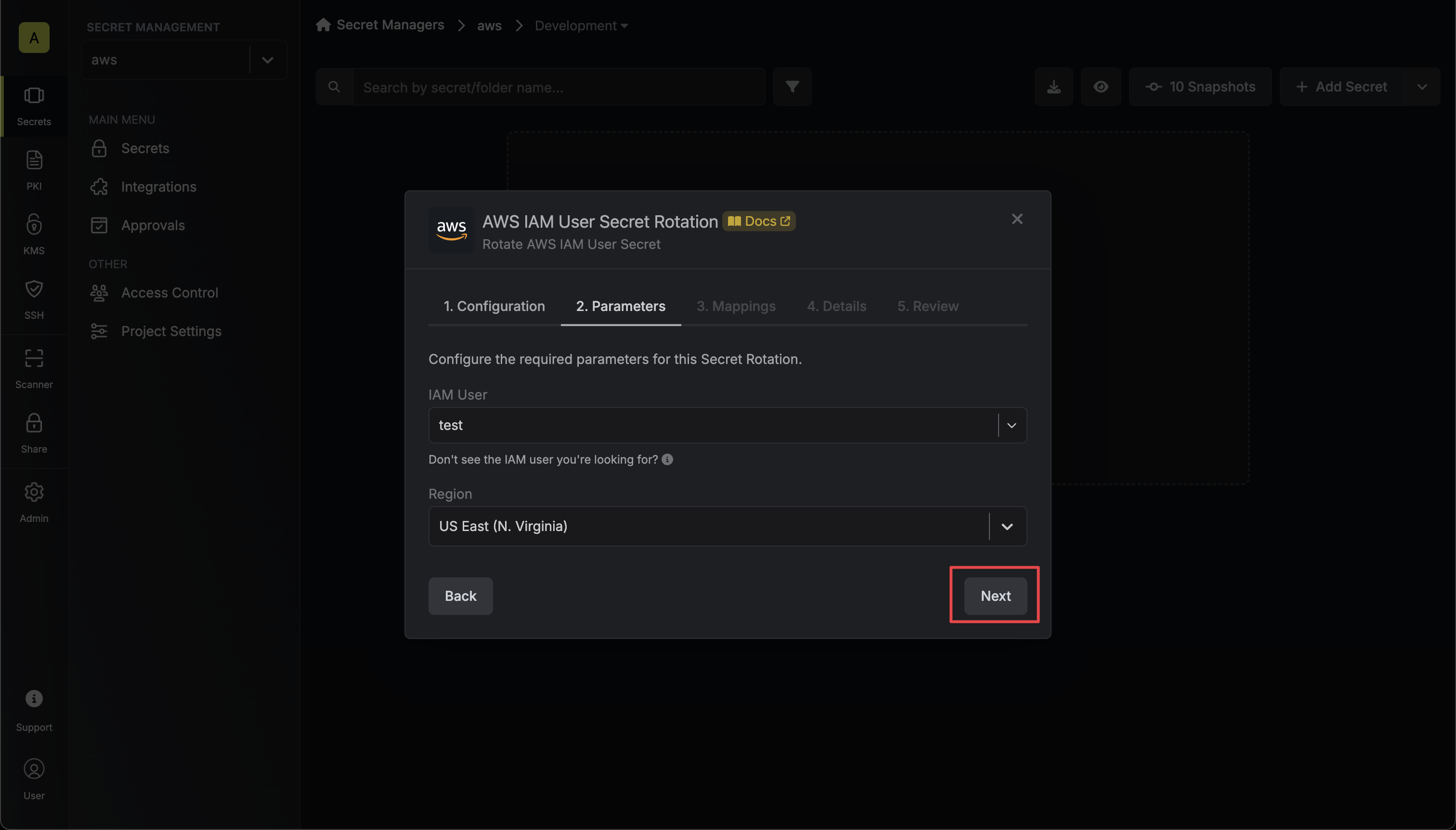
Select the AWS IAM user and the region of the user whose credentials you want to rotate. Then click Next.
-
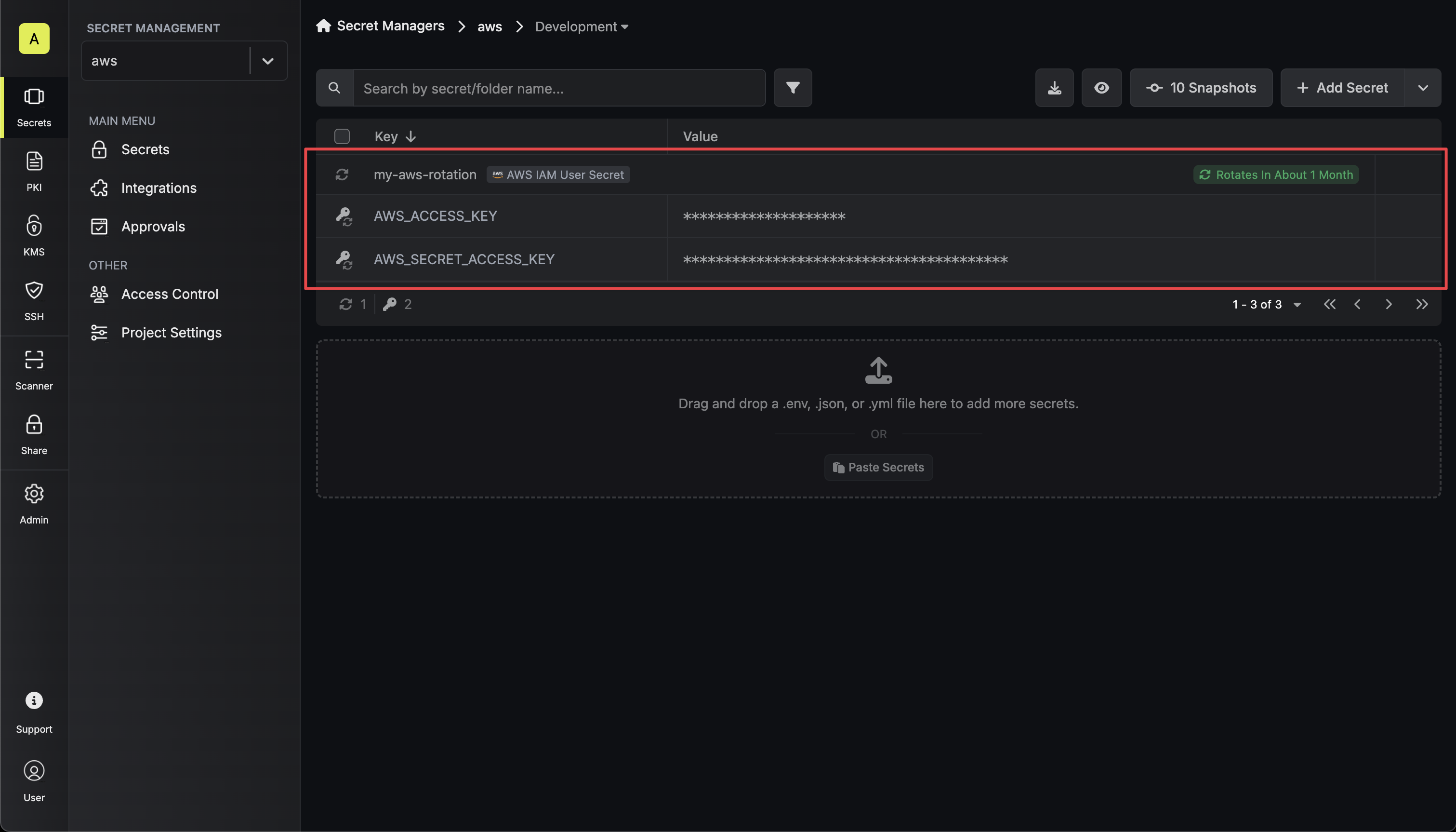
Specify the secret names that the AWS IAM access key credentials should be mapped to. Then click Next.
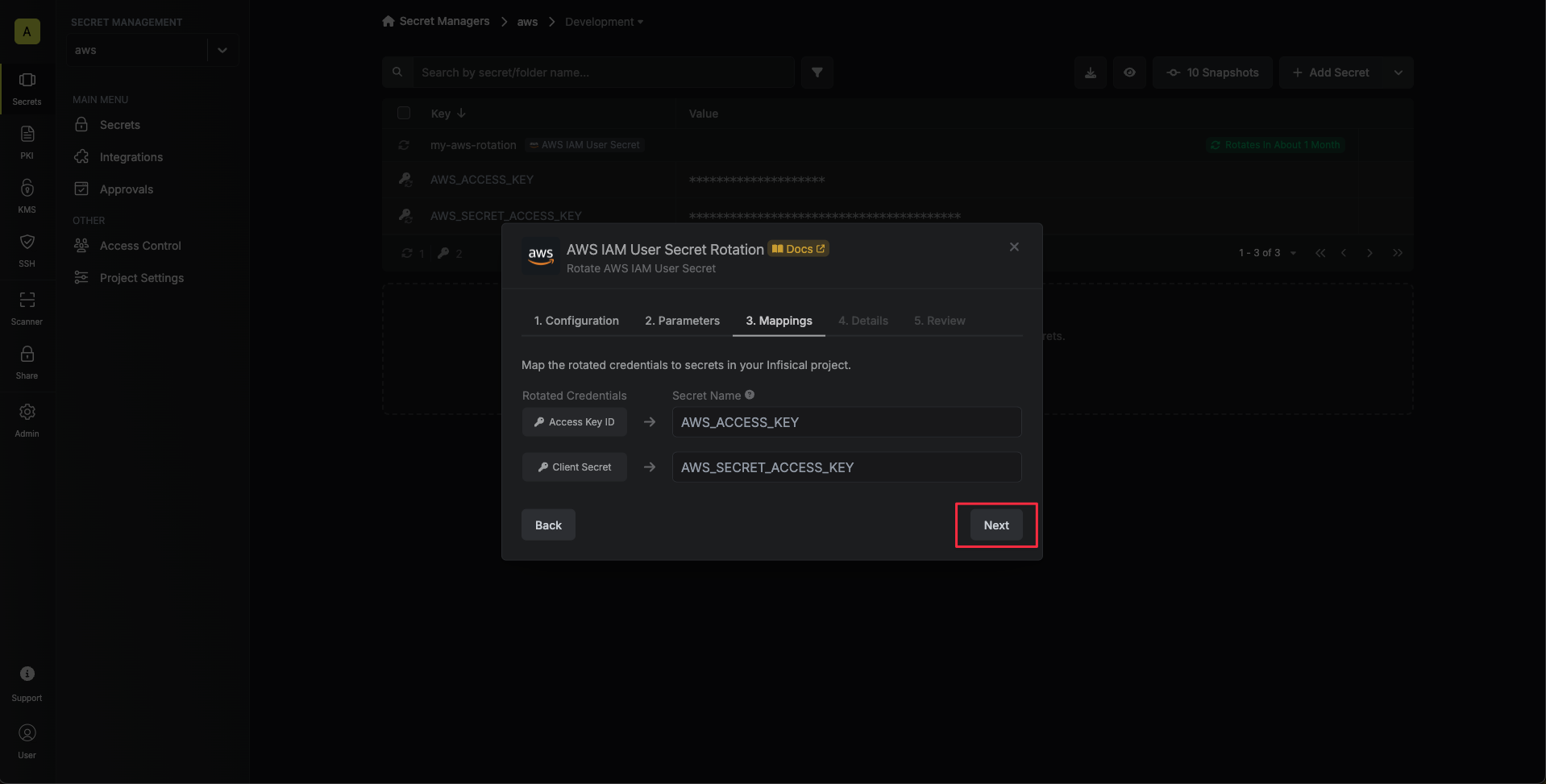
- Access Key ID - the name of the secret that the AWS access key ID will be mapped to.
- Secret Access Key - the name of the secret that the rotated secret access key will be mapped to.
-
Give your rotation a name and description (optional). Then click Next.
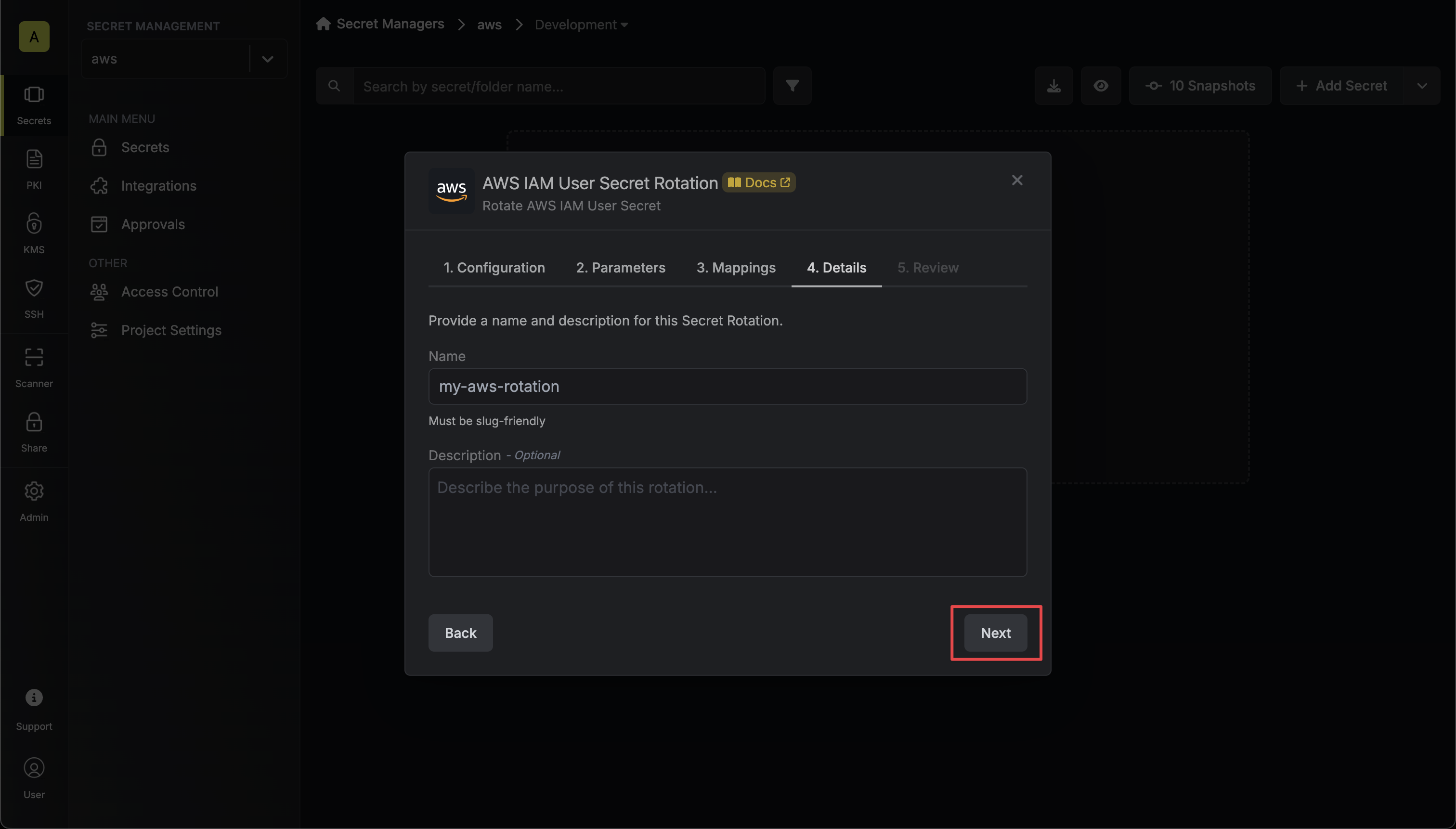
- Name - the name of the secret rotation configuration. Must be slug-friendly.
- Description (optional) - a description of this rotation configuration.
-
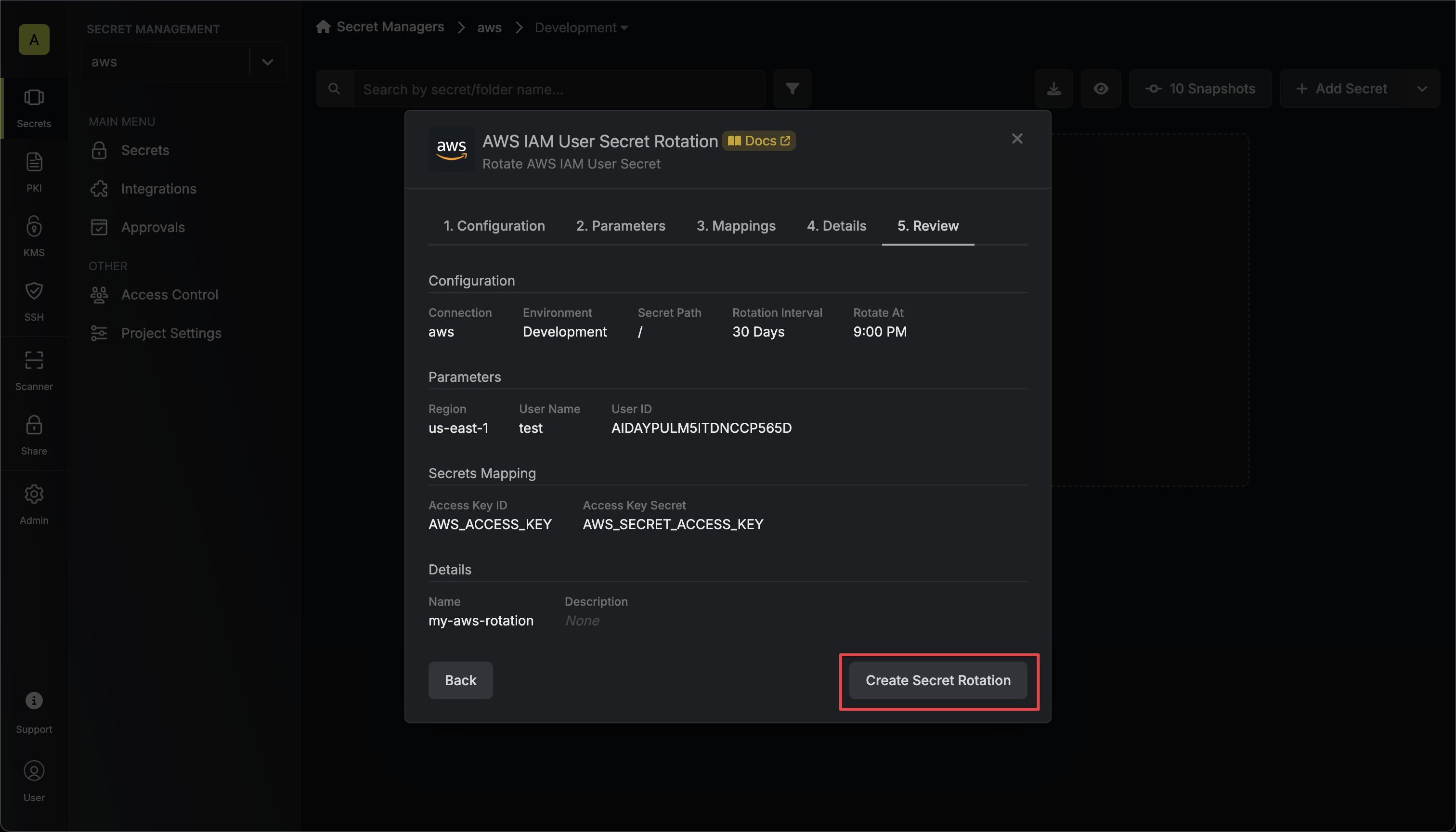
Review your configuration, then click Create Secret Rotation.
-
Your AWS IAM User credentials are now available for use via the mapped secrets.
Why are my AWS IAM credentials not rotating?
Why are my AWS IAM credentials not rotating?
There are a few reasons for why this might happen:
- The strategy configuration is invalid (e.g. the managing IAM user’s credentials are incorrect, the target AWS region is incorrect, etc.)
- The managing IAM user is insufficiently permissioned to rotate the credentials of the target IAM user. For instance, you may have setup paths for the managing IAM user and the policy does not have the necessary permissions to rotate the credentials.