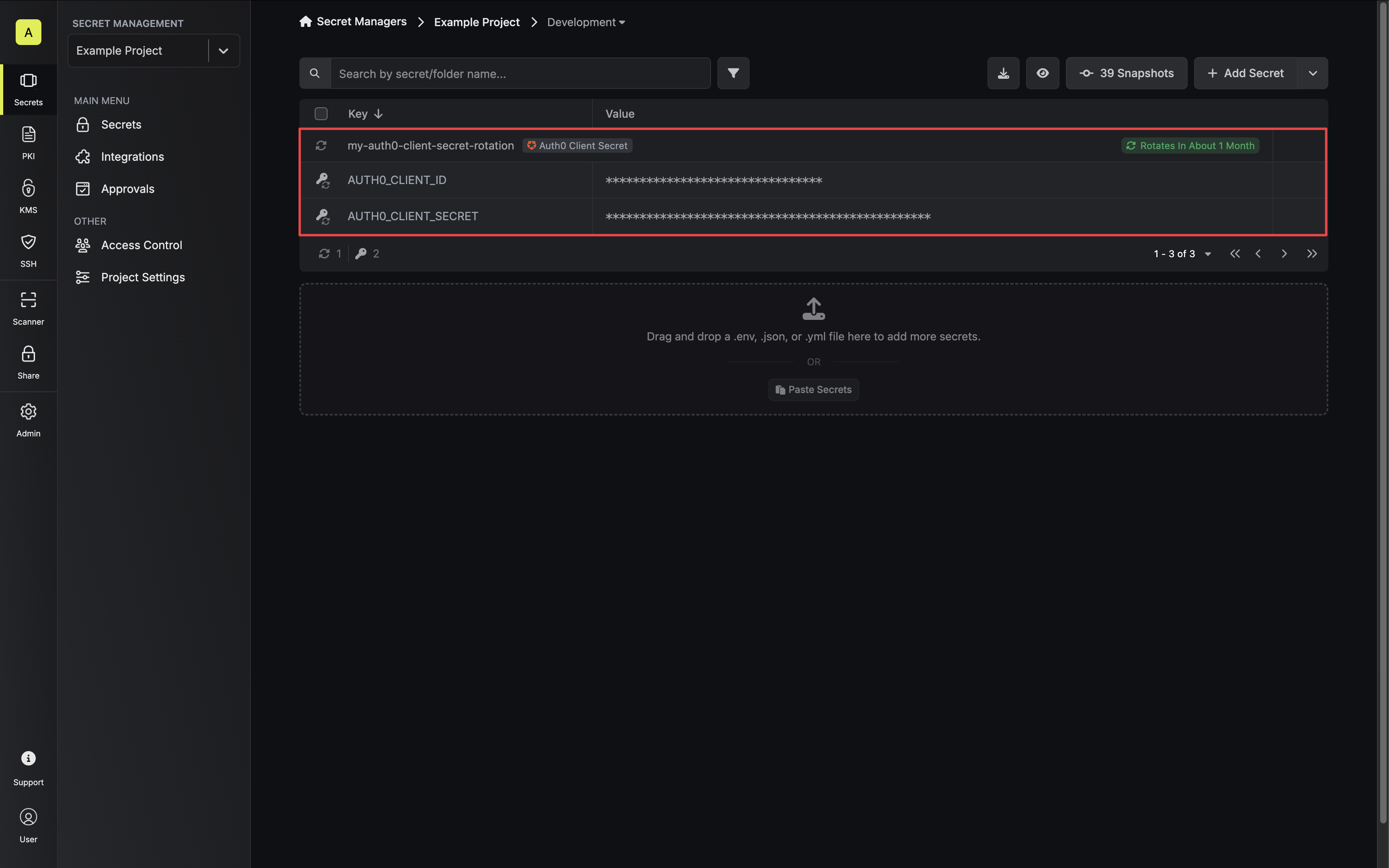
Rotation Type: Single-PhaseThis rotation updates a single credential set in place. Old credentials become invalid immediately upon rotation. This means that clients using the previous credentials will fail to authenticate until they retrieve the new credentials.This is a limitation of the Auth0 platform and cannot be rectified by Infisical.
Prerequisites
- Create an Auth0 Connection with the required Secret Rotation audience and permissions
Create an Auth0 Client Secret Rotation in Infisical
- Infisical UI
- API
-
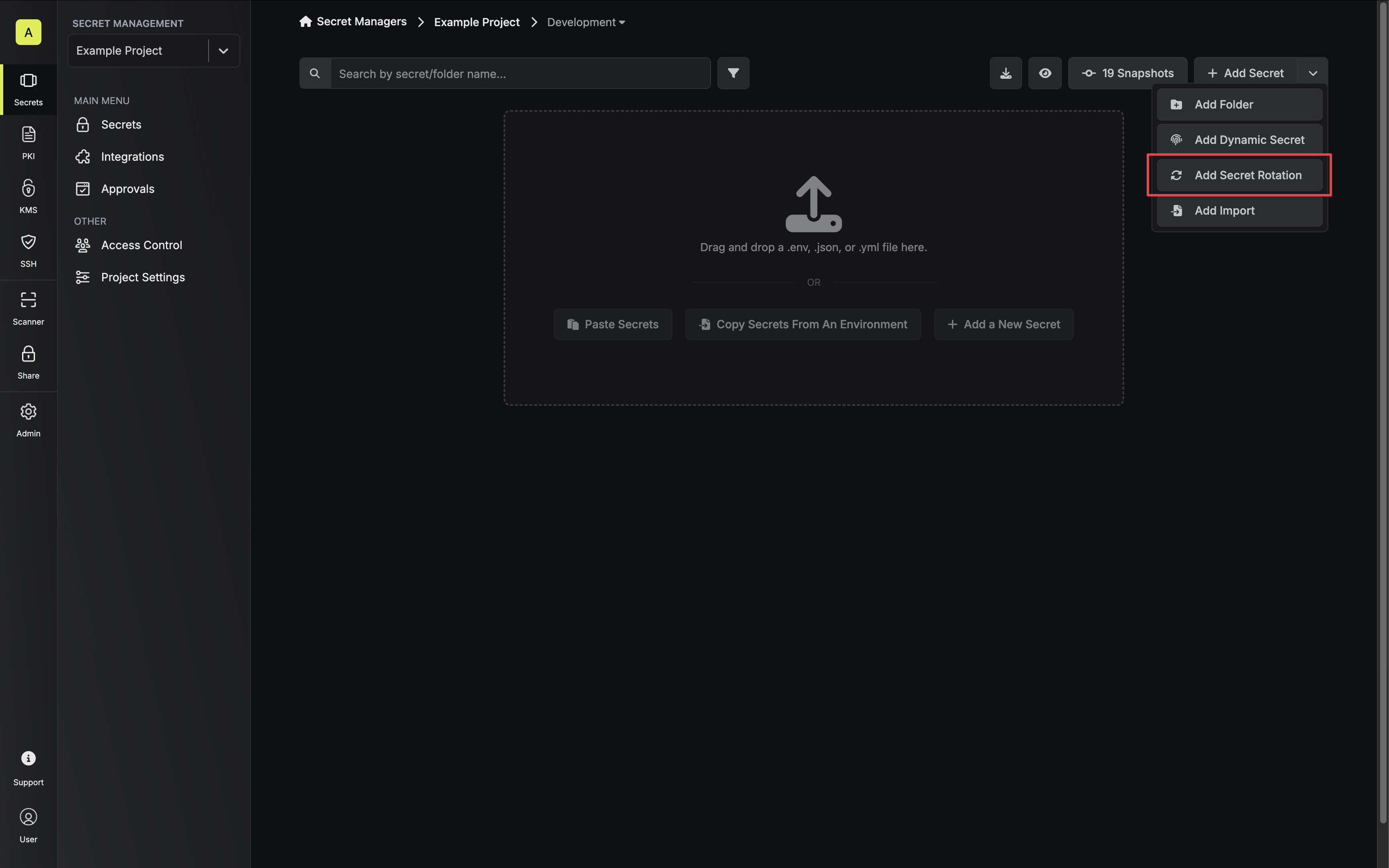
Navigate to your Secret Manager Project’s Dashboard and select Add Secret Rotation from the actions dropdown.
-
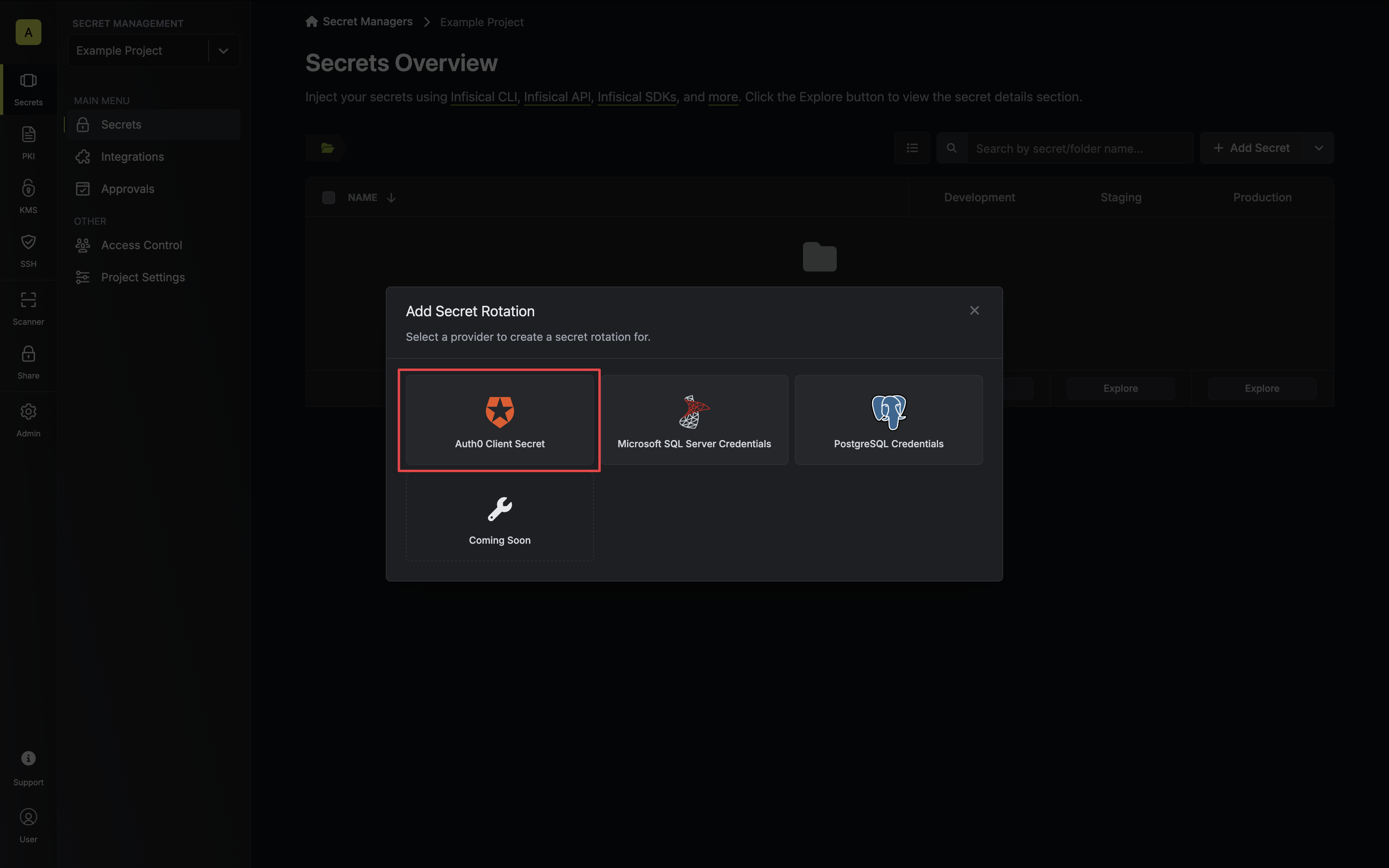
Select the Auth0 Client Secret option.
-
Select the Auth0 Connection to use and configure the rotation behavior. Then click Next.
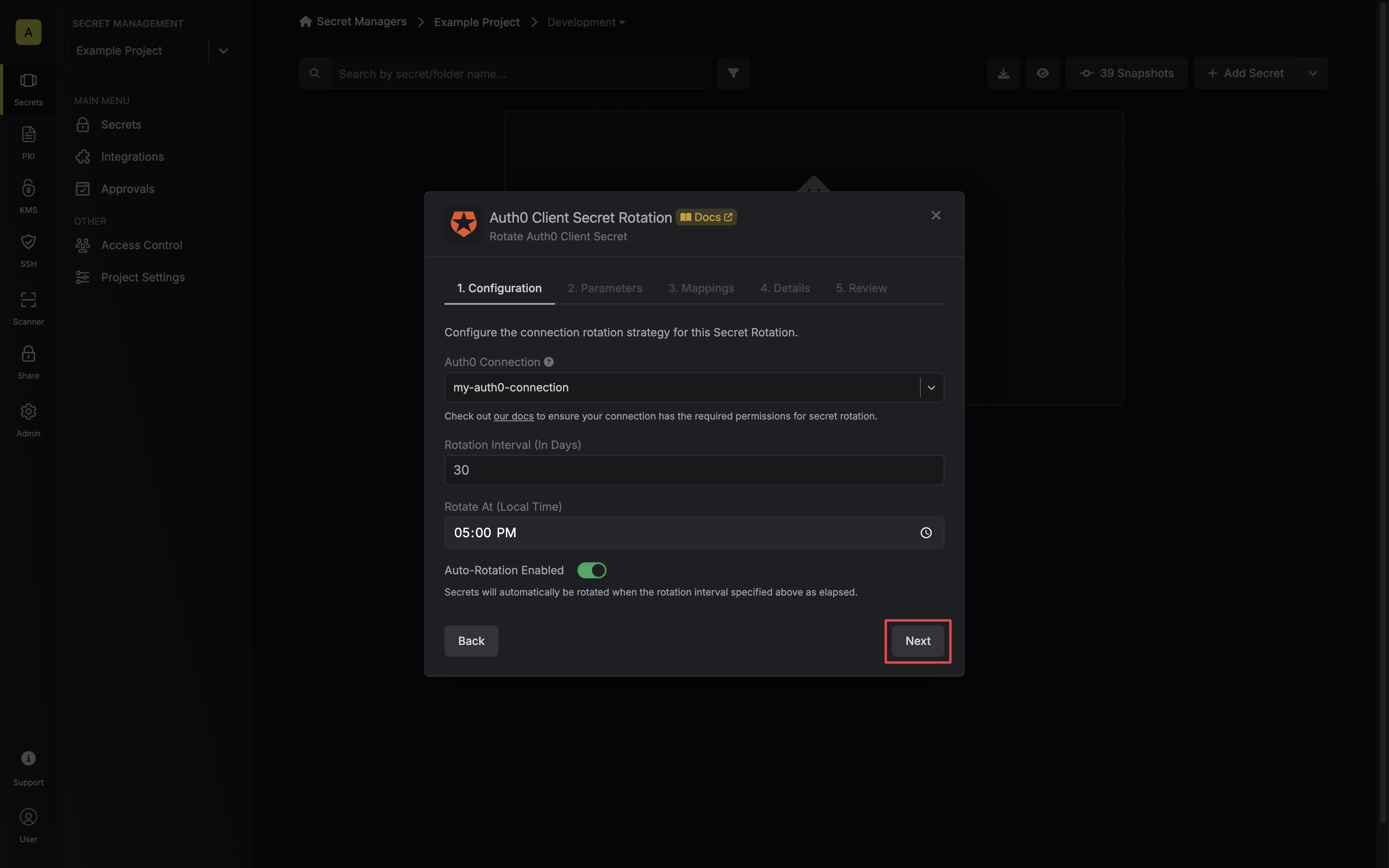
- Auth0 Connection - the connection that will perform the rotation of the specified application’s Client Secret.
- Rotation Interval - the interval, in days, that once elapsed will trigger a rotation.
- Rotate At - the local time of day when rotation should occur once the interval has elapsed.
- Auto-Rotation Enabled - whether secrets should automatically be rotated once the rotation interval has elapsed. Disable this option to manually rotate secrets or pause secret rotation.
Due to Auth0 Client Secret Rotations rotating a single credential set, auto-rotation may result in service interruptions. If you need to ensure service continuity, we recommend disabling this option. -
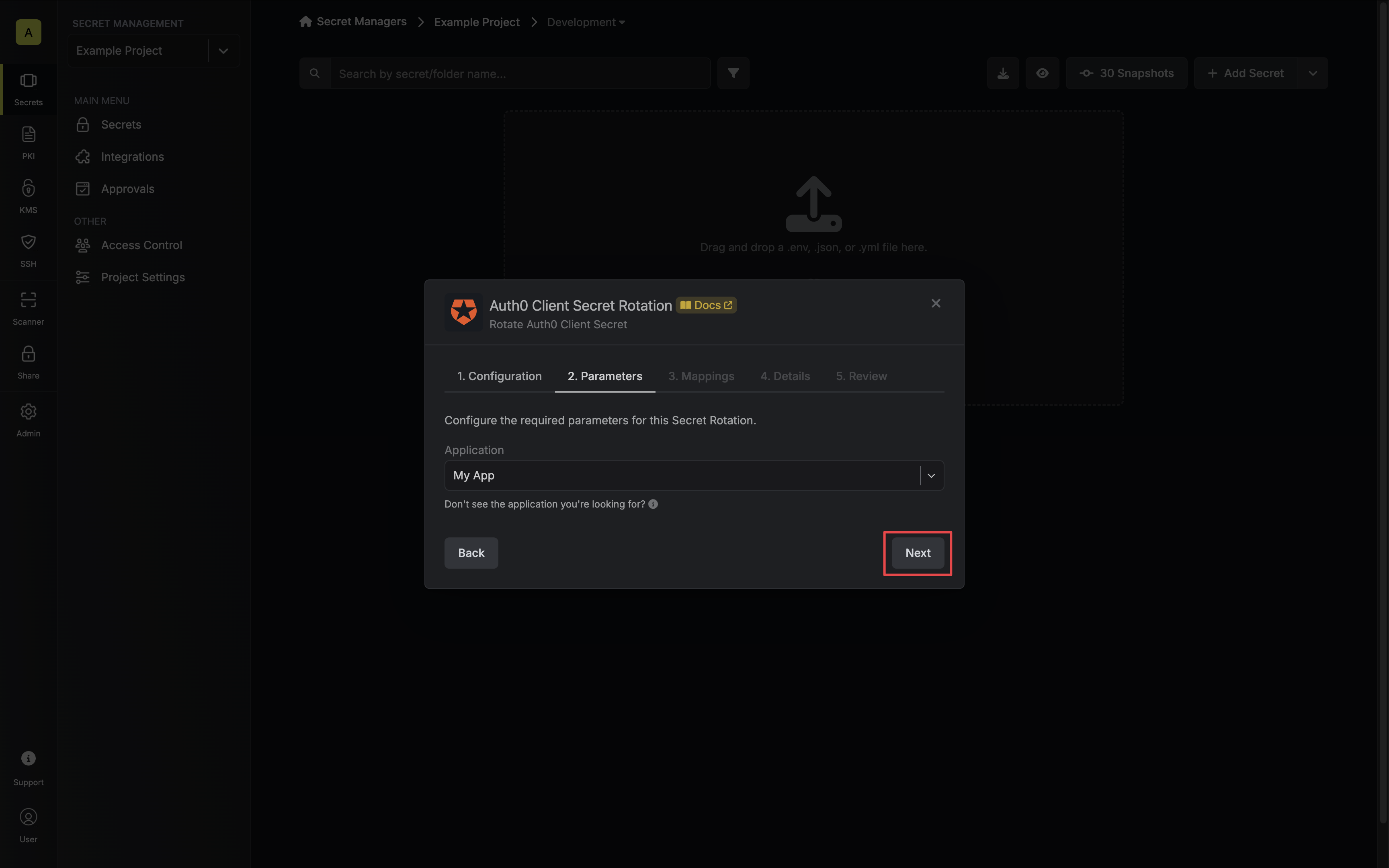
Select the Auth0 application whose Client Secret you want to rotate. Then click Next.
-
Specify the secret names that the client credentials should be mapped to. Then click Next.
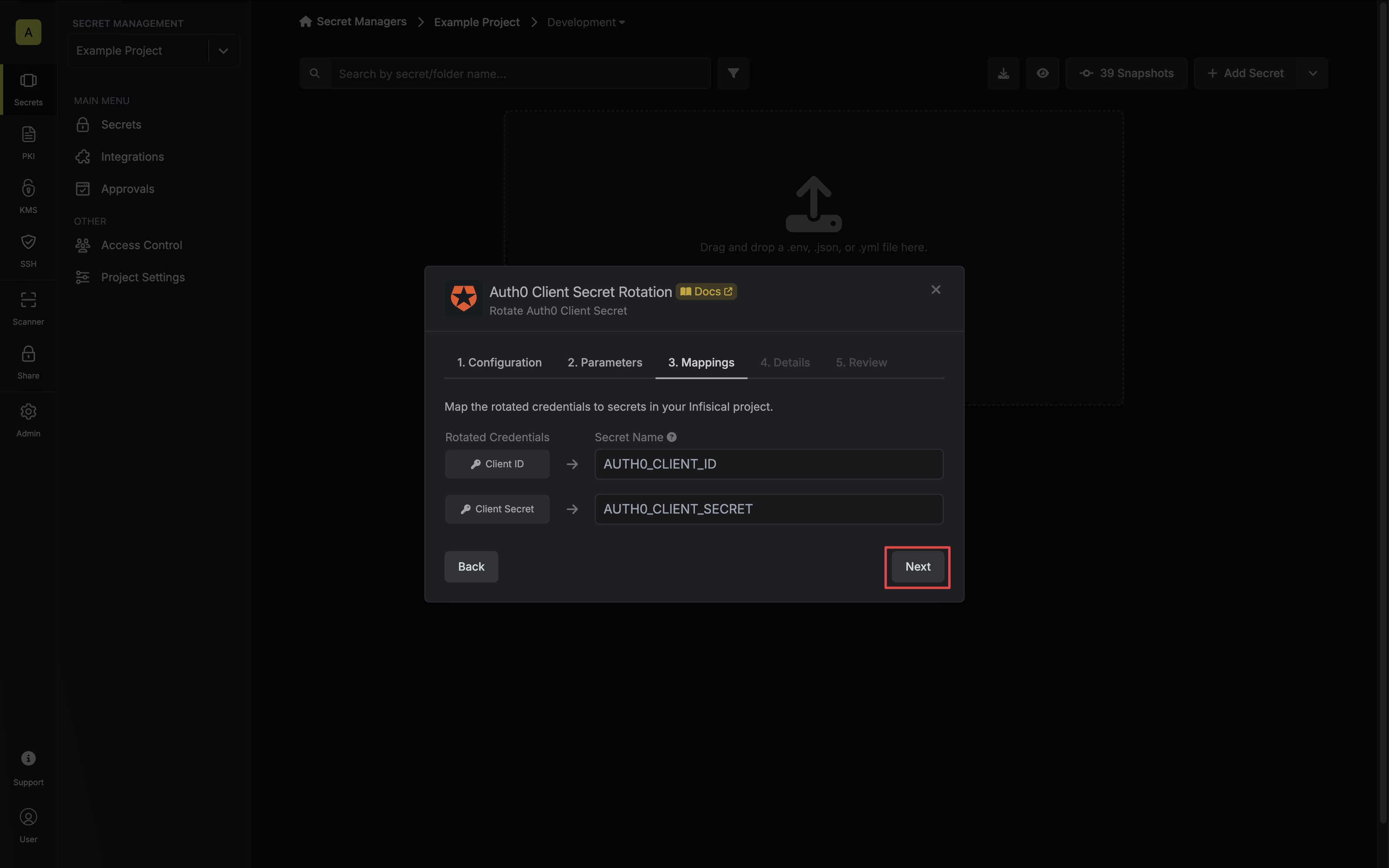
- Client ID - the name of the secret that the application Client ID will be mapped to.
- Client Secret - the name of the secret that the rotated Client Secret will be mapped to.
-
Give your rotation a name and description (optional). Then click Next.
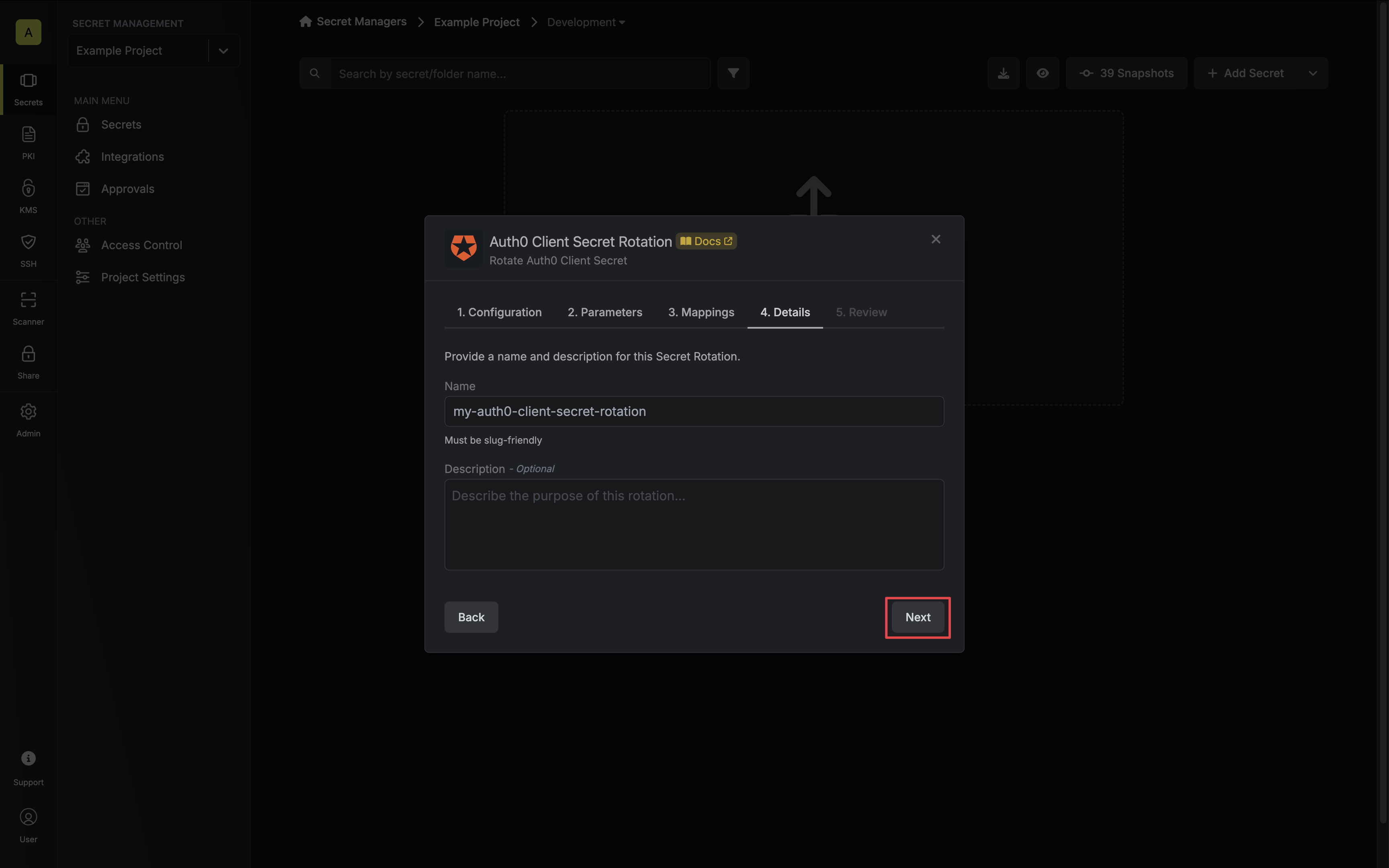
- Name - the name of the secret rotation configuration. Must be slug-friendly.
- Description (optional) - a description of this rotation configuration.
-
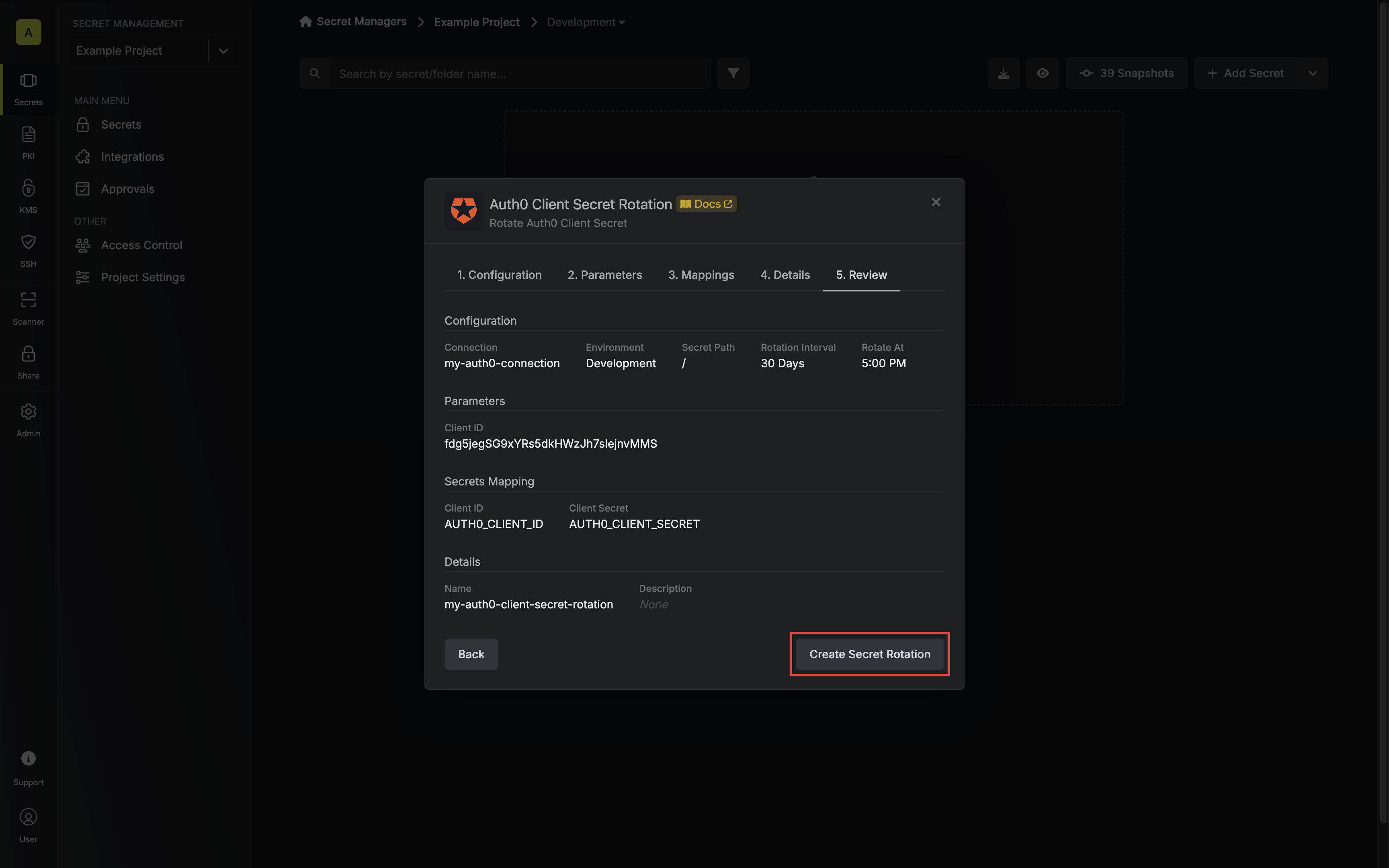
Review your configuration, then click Create Secret Rotation.
-
Your Auth0 Client Secret credentials are now available for use via the mapped secrets.