Guide to Creating a Webhook Alert
To create an alert, head to your Certificate Management Project > Alerting and press Create Certificate Alert.
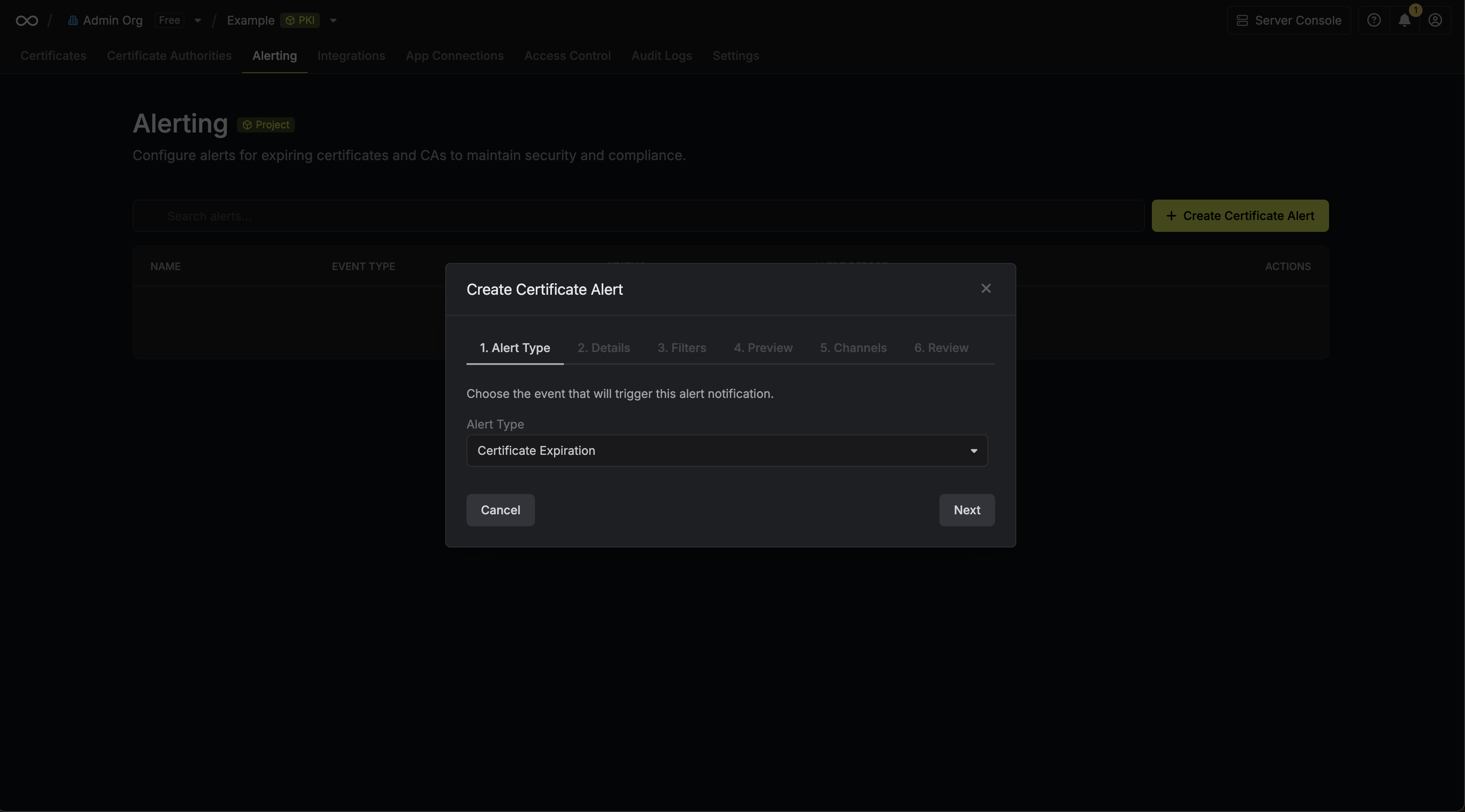 Here’s some guidance for each field in the alert configuration sequence:
Here’s some guidance for each field in the alert configuration sequence:
- Alert Type: The type of alert to create such as Certificate Expiration.
- Alert Name: A slug-friendly name for the alert such as
tls-expiry-alert. - Description: An optional description for the alert.
- Alert Before: The time before certificate expiration to trigger the alert such as 30 days denoted by
30d. - Filters: A list of filters that determine which certificates the alert applies to. Each row includes a Field, Operator, and Value to match against. For example, you can filter for certificates with a common name containing
example.comby setting the field to Common Name, the operator to Contains, and the value toexample.com.
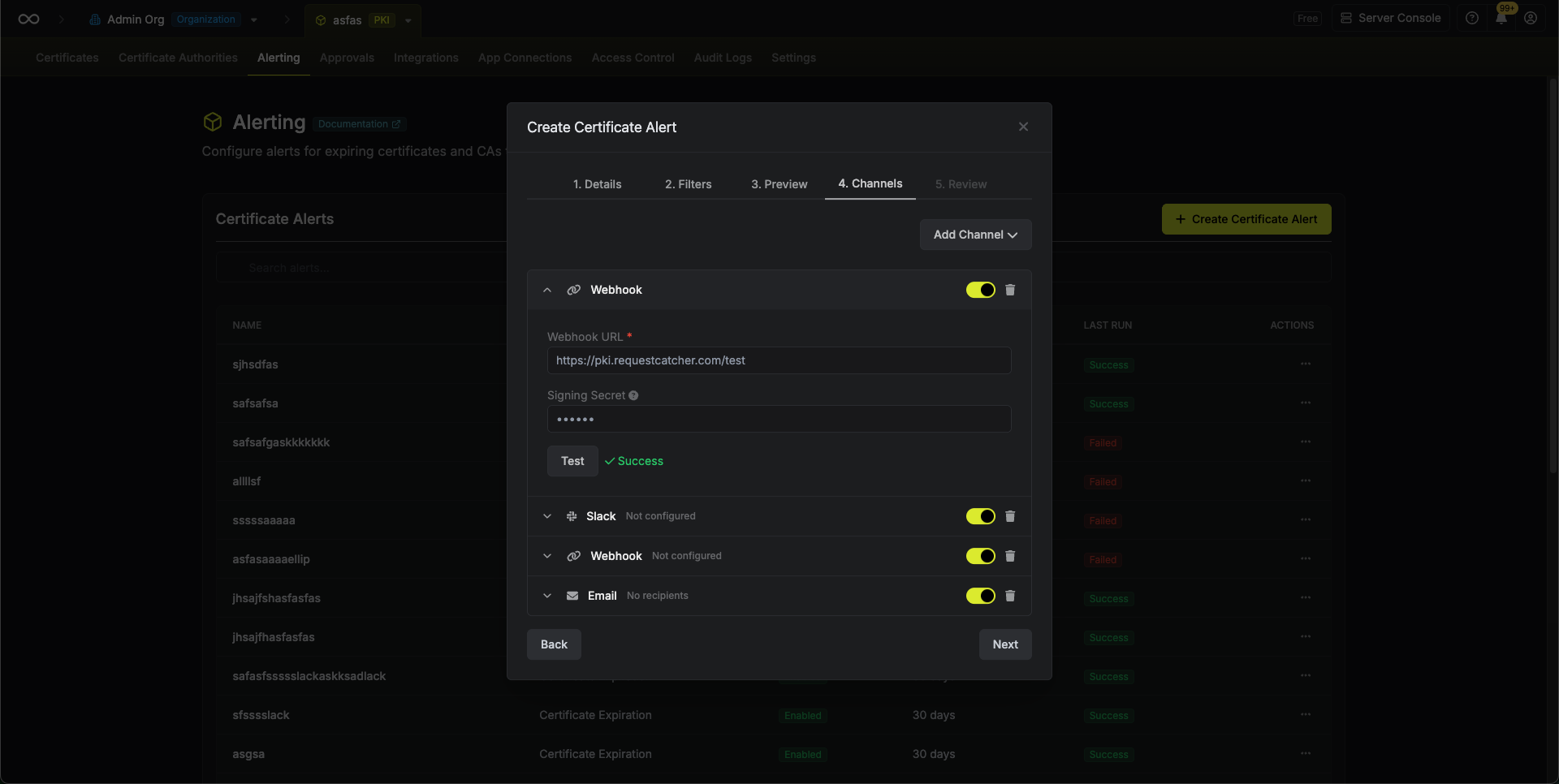
Webhook Payload Format
Webhook notifications are sent as HTTP POST requests with a CloudEvents-compliant JSON payload.Webhook Signature Verification
If you configure a signing secret for your webhook channel, Infisical will include anx-infisical-signature header with each request. This allows you to verify that the webhook payload originated from Infisical.
The header format is:
<timestamp>is the Unix timestamp (in milliseconds) when the signature was generatedv1indicates the signature version<signature>is the HMAC-SHA256 signature of the payload
- Extract the timestamp and signature from the header
- Construct the signature payload by concatenating the timestamp, a period (
.), and the raw request body:{timestamp}.{body} - Compute an HMAC-SHA256 hash using your signing secret
- Compare the computed signature with the signature from the header

