Prerequisites
Before you begin, make sure you have:- An Apache HTTP Server running on a Linux system with administrative access.
- A certificate profile configured with the ACME enrollment method in Infisical.
- Network connectivity from your Apache server to Infisical.
- Port 80 open and reachable for ACME HTTP-01 validation.
Guide
Obtain ACME Configuration from Infisical
Navigate to your certificate management project in Infisical and locate your certificate profile configured with the ACME enrollment method. Click the Reveal ACME EAB option to view the ACME configuration details.
Click the Reveal ACME EAB option to view the ACME configuration details.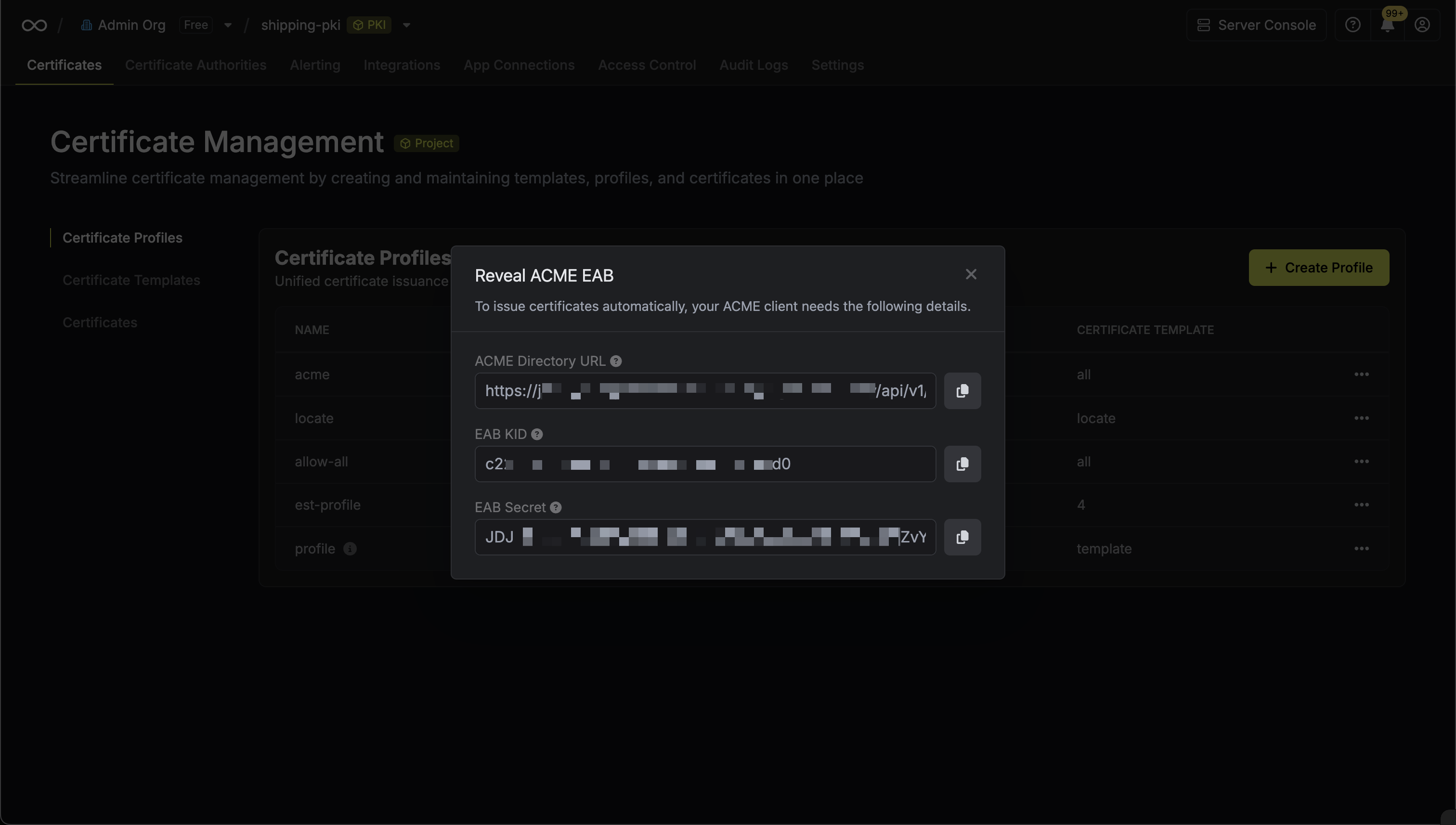 From the ACME configuration, gather the following values:
From the ACME configuration, gather the following values:
 Click the Reveal ACME EAB option to view the ACME configuration details.
Click the Reveal ACME EAB option to view the ACME configuration details. From the ACME configuration, gather the following values:
From the ACME configuration, gather the following values:- ACME Directory URL: The URL that Certbot will use to communicate with Infisical’s ACME server. This takes the form
https://your-infisical-instance.com/api/v1/cert-manager/certificate-profiles/{profile-id}/acme/directory. - EAB Key Identifier (KID): A unique identifier that tells Infisical which ACME account is making the request.
- EAB Secret: A secret key that authenticates your ACME client with Infisical.
Keep your EAB credentials secure as they authenticate your ACME client with Infisical PKI. These credentials are unique to each certificate profile and should not be shared.
Install Certbot
Install Certbot with the Apache plugin on the server where Apache is running by following the official Certbot installation guide.The installation guide provides up-to-date instructions for various Linux distributions and package managers, ensuring you get the most current version and proper Apache plugin integration.After installation, you can verify that Certbot has been installed correctly by running:
Request Certificate Using Certbot
Run the following command to request a certificate from Infisical:For guidance on each parameter:After updating the virtual host configuration, test and reload Apache to apply the changes:If
certonly: Instructs Certbot to request a certificate without modifying your Apache configuration files; this mode is recommended if you prefer to manage your Apache SSL configuration manually or have a complex setup.--apache: Specifies the Apache plugin so Certbot can solve the HTTP-01 challenge by creating temporary files served by Apache.--server: The Infisical ACME directory URL from Step 1. This instructs Certbot to communicate with Infisical’s ACME server instead of Let’s Encrypt.--eab-kid: Your External Account Binding (EAB) Key Identifier from Step 1.--eab-hmac-key: The EAB secret associated with the KID from Step 1.-d: Specifies the domain name for which the certificate is being requested.--email: The contact email for expiration notices and account recovery.--agree-tos: Accepts the ACME server’s Terms of Service.--non-interactive: Runs Certbot without prompting for user input (recommended for automation).
/etc/letsencrypt/live/{domain-name}/.If --certonly is used: Certbot does not modify your Apache configuration, so you must manually update your Apache virtual host to reference the new certificate files and reload the server to apply the changes.Here’s an example SSL virtual host configuration for Apache:--certonly was not used: Certbot uses installer mode, which attempts to automatically configure HTTPS by updating your Apache virtual host configuration and reloading the server if needed.At this point, your Apache server should be successfully serving HTTPS using the certificate issued by Infisical.Verify Certificate Installation
After configuring Apache SSL, verify that your certificate was issued correctly and Apache is serving it properly.Check that the certificate files were created by Certbot:You should see files like:
cert.pem(your certificate)chain.pem(certificate chain)fullchain.pem(certificate + chain)privkey.pem(private key)
Renew Your Certificate with Certbot
Certbot automatically installs a To test the renewal process, run the following command:This command simulates the full renewal process without modifying your active certificate. If the dry run succeeds, automatic renewal will work as expected.To trigger an actual renewal immediately, run the following command:Note that after a certificate is renewed, Apache must be reloaded so it can begin using the new certificate. To do this, run the following command:To automate the process of renewing a certificate and reloading Apache, you can create a simple deploy hook that Certbot will run after every successful renewal.Inside Then make the hook executable:Alternatively, you can use the
systemd timer during installation. This timer runs twice per day and checks whether any certificates are due for renewal. Because Certbot stores the ACME server URL and EAB credentials from your initial request, renewal will automatically use the same Infisical ACME configuration—no additional settings are required.Note that Certbot automatically renews certificates when they are within 30 days of expiration; renewal settings can be adjusted in /etc/letsencrypt/renewal/{domain-name}.conf./etc/letsencrypt/renewal-hooks/deploy/reload-apache.sh, add the following:--post-hook option when manually renewing:Certbot automatically renews certificates when they are within 30 days of expiration using its built-in systemd timer. The deploy hook above will run after each successful renewal, handling the Apache reload automatically. Apache has native Certbot plugin integration, so no additional configuration is typically needed.

