Prerequisites
Before you begin, make sure you have:- A Windows Server instance running with administrative access.
- A certificate profile configured with the ACME enrollment method in Infisical.
- Network connectivity from your Windows Server to Infisical.
Guide
Obtain ACME Configuration from Infisical
Navigate to your certificate management project in Infisical and locate your certificate profile configured with the ACME enrollment method.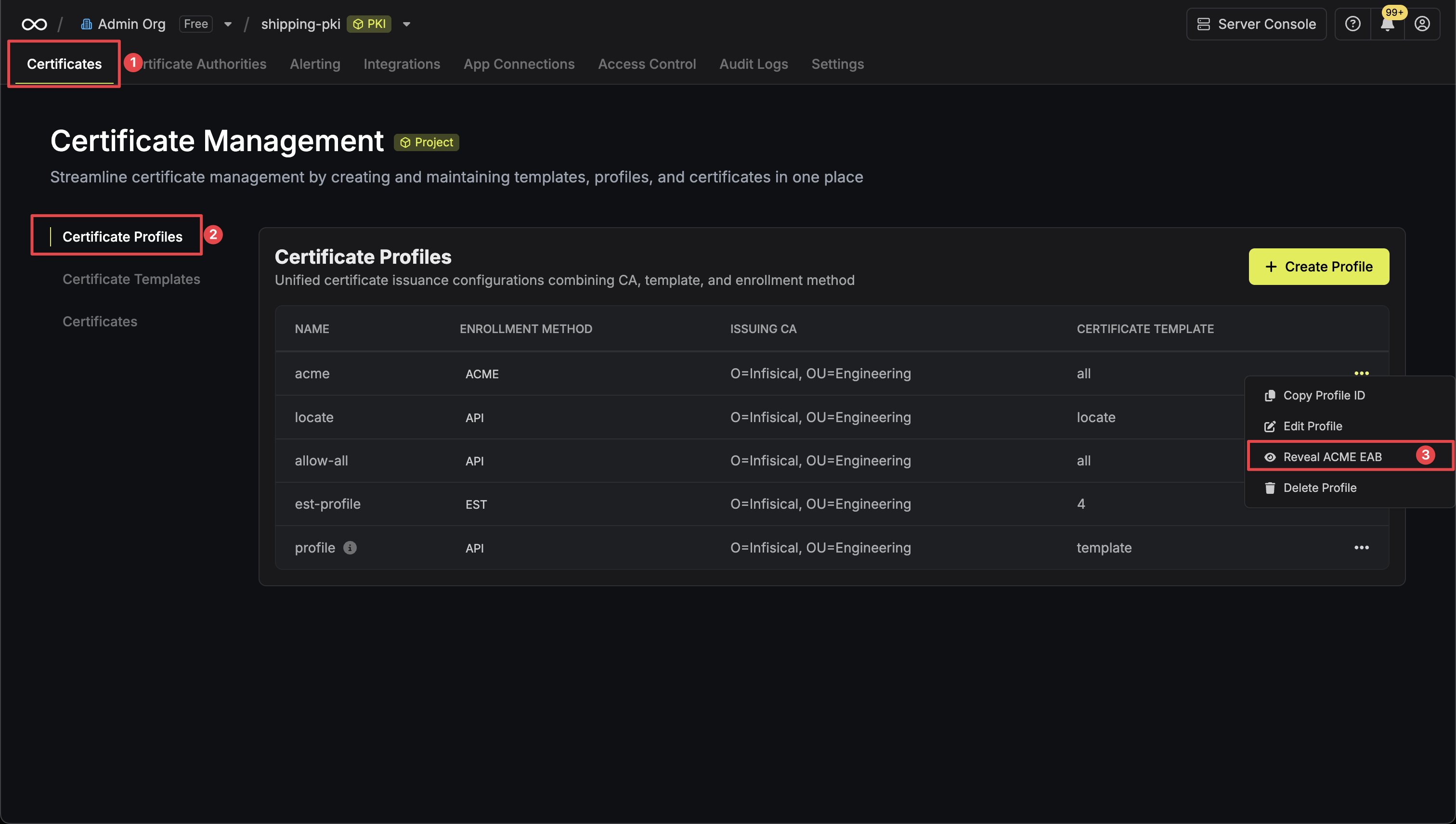 Click the Reveal ACME EAB option to view the ACME configuration details.
Click the Reveal ACME EAB option to view the ACME configuration details.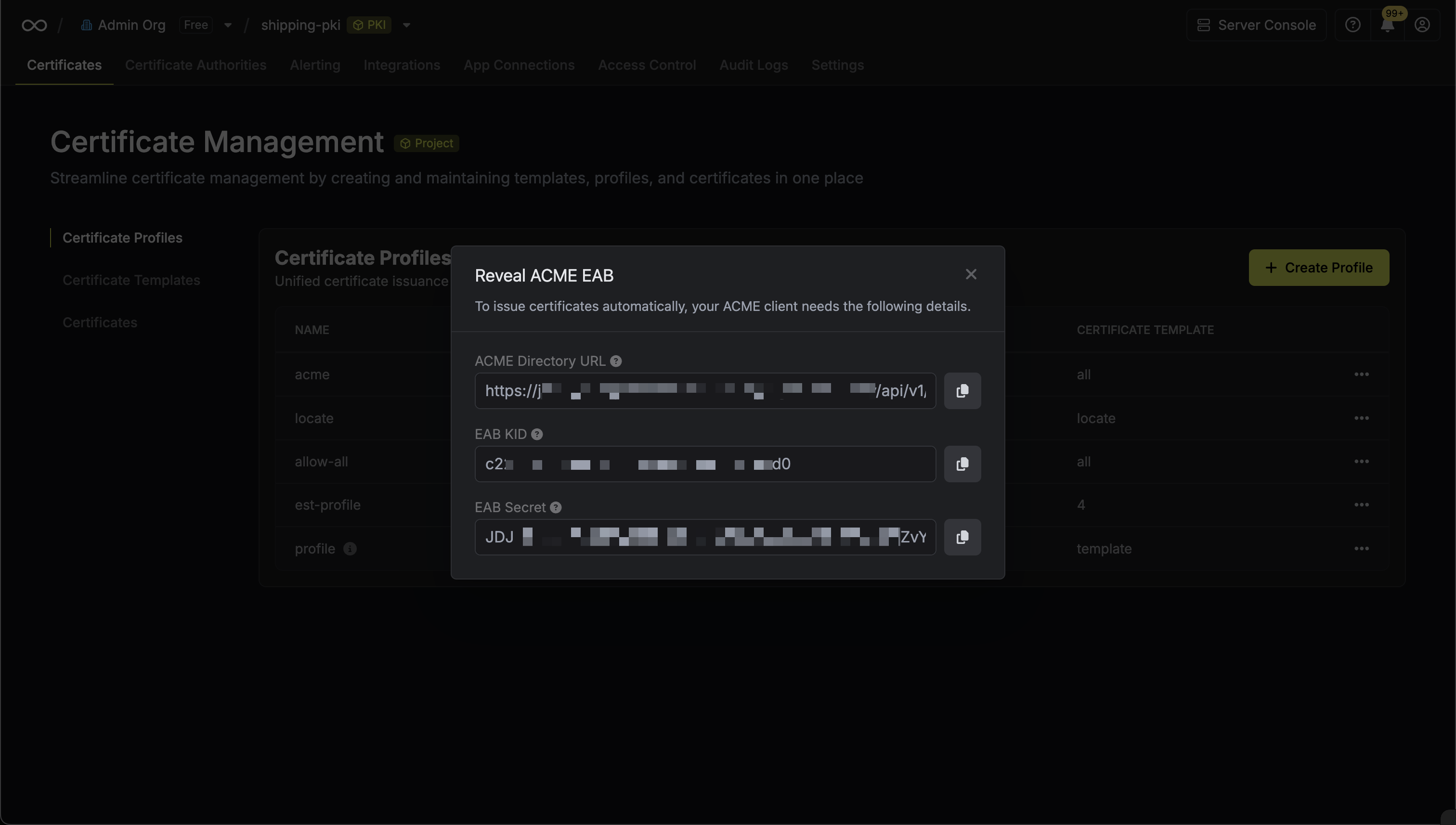 From the ACME configuration, gather the following values:
From the ACME configuration, gather the following values:
 Click the Reveal ACME EAB option to view the ACME configuration details.
Click the Reveal ACME EAB option to view the ACME configuration details. From the ACME configuration, gather the following values:
From the ACME configuration, gather the following values:- ACME Directory URL: The URL that win-acme will use to communicate with Infisical’s ACME server. This takes the form
https://your-infisical-instance.com/api/v1/cert-manager/certificate-profiles/{profile-id}/acme/directory. - EAB Key Identifier (KID): A unique identifier that tells Infisical which ACME account is making the request.
- EAB Secret: A secret key that authenticates your ACME client with Infisical.
Keep your EAB credentials secure as they authenticate your ACME client with Infisical PKI. These credentials are unique to each certificate profile and should not be shared.
Install win-acme
Install win-acme on your Windows Server using one of the following methods.
- Download from GitHub
- .NET Tool (Global Install)
- Visit the win-acme releases page.
- Download the latest stable release ZIP file.
- Extract the contents to a folder (e.g.,
C:\win-acme). - Open Command Prompt or PowerShell as Administrator.
- Navigate to the win-acme folder.
Request Certificate Using Command Line
Run the following win-acme command to request a certificate from Infisical:For guidance on each parameter:
--target manual: Specifies manual target configuration for domain specification.--host: The domain name for which the certificate is being requested.--baseuri: The Infisical ACME directory URL from Step 1. This instructs win-acme to communicate with Infisical’s ACME server instead of other ACME providers.--eab-key-identifier: Your External Account Binding (EAB) Key Identifier from Step 1.--eab-key: The EAB secret associated with the KID from Step 1.--validation selfhosting: Uses self-hosting validation method to solve the HTTP-01 challenge.--store pemfiles: Stores certificates as PEM files in a specified directory.--pemfilespath: Directory where certificates will be saved on your Windows Server.--verbose: Enables detailed logging for troubleshooting and monitoring the certificate request process.
Replace the placeholder values with your actual configuration:
example.infisical.com: Your actual domain namehttps://your-infisical-instance.com/api/v1/cert-manager/certificate-profiles/{profile-id}/acme/directory: Your Infisical ACME endpoint from Step 1your-eab-key-identifierandyour-eab-secret: Your External Account Binding credentials from Step 1C:\certificates: Your desired certificate storage location
Alternative Storage Options
Win-acme supports various certificate storage options beyond PEM files. Here are common alternatives for different deployment scenarios:
- Windows Certificate Store
- PFX Files
- IIS Central SSL
Store certificates directly in the Windows Certificate Store for integration with IIS and other Windows services:
Configure Automatic Renewal
Win-acme can automatically create a Windows Scheduled Task for certificate renewal. Because win-acme stores the ACME server URL and EAB credentials from your initial request, renewal will automatically use the same Infisical ACME configuration—no additional settings are required.Option 1: Enable during initial certificate requestInclude the Option 2: Test manual renewalYou can test the renewal process manually before setting up automation to ensure the configuration works correctly:This command simulates the full renewal process and verifies that win-acme can successfully contact Infisical and renew your certificate using the stored configuration.Option 3: Verify scheduled task creationCheck that the scheduled task was created successfully:The automatic renewal task will:
--setuptaskscheduler parameter in your initial command to automatically create the renewal task:- Run under the SYSTEM account for elevated privileges.
- Check certificates daily for renewal eligibility.
- Automatically renew certificates that are within the renewal threshold (typically 30 days before expiration).
- Log renewal activities to Windows Event Viewer and win-acme log files for monitoring and troubleshooting.
Win-acme stores renewal configurations automatically in its settings directory, so once a certificate is created, the renewal process will use the same parameters (ACME endpoint, EAB credentials, storage options) for future renewals. The renewal threshold can be adjusted in the win-acme configuration files if needed.
Verify Certificate Installation
After successful certificate issuance, verify that the certificate files have been created correctly based on your chosen storage method.
- PEM Files
- Windows Certificate Store
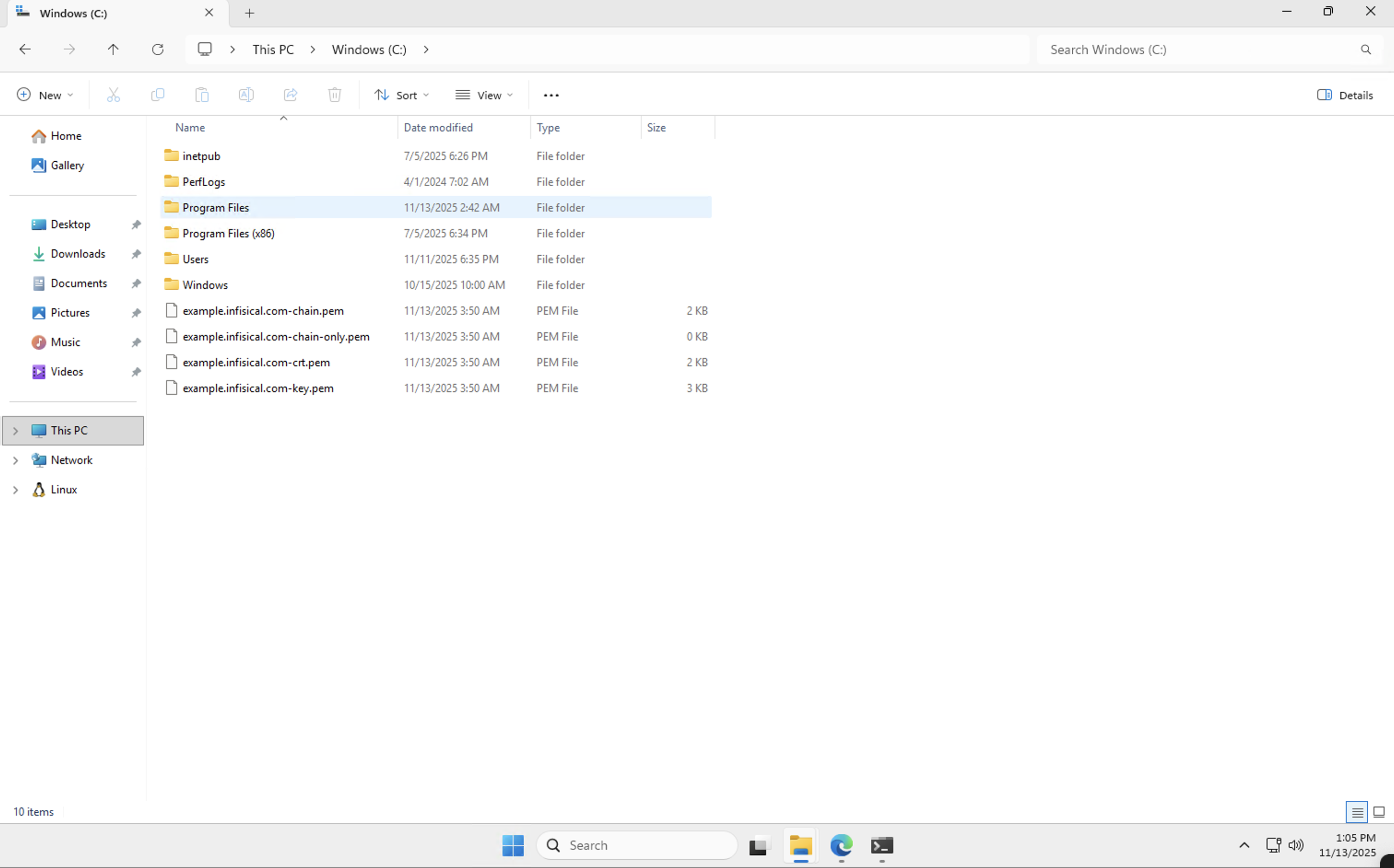
Check your specified PEM files directory to ensure all certificate components are present:You should see files like:
-
example.infisical.com-crt.pem(certificate) -
example.infisical.com-key.pem(private key) -
example.infisical.com-chain.pem(complete certificate chain) -
example.infisical.com-chain-only.pem(only certificate chain)