May 2024 has been one of the most exciting months for Infisical yet! Our team released many great features and has a lot of awesome news to share!
1: AWS, GCP, Azure, and Kubernetes Native Auth Methods
It is now possible for applications to fetch secrets back from Infisical without needing to explicitly manage an additional secret to authenticate with the platform in the first place.
Here’s how each method works:
-
Kubernetes Auth: Pods can use Kubernetes-native service accounts to have a service account credential mounted at a specified path. This credential can be used to authenticate with Infisical.
-
AWS Auth: AWS IAM principals for services like EC2 and Lambda can send a signed query containing a computed signature specific to the underlying IAM principal to authenticate with Infisical.
-
GCP Auth: GCP services like Compute Engine, App Engine, Cloud Functions, and Kubernetes Engine can use GCP-native ID tokens to authenticate with Infisical.
-
Azure Auth: Azure services like VMs, App Services, Functions, and Kubernetes Service can use Azure-native managed identity access tokens to authenticate with Infisical.
By treating Kubernetes, AWS, GCP, and Azure as trusted identity providers to supply and verify native platform tokens, we achieve a near “secretless” authentication pattern for applications running on these platforms. It’s now as seamless as pointing your application to Infisical to fetch back secrets.

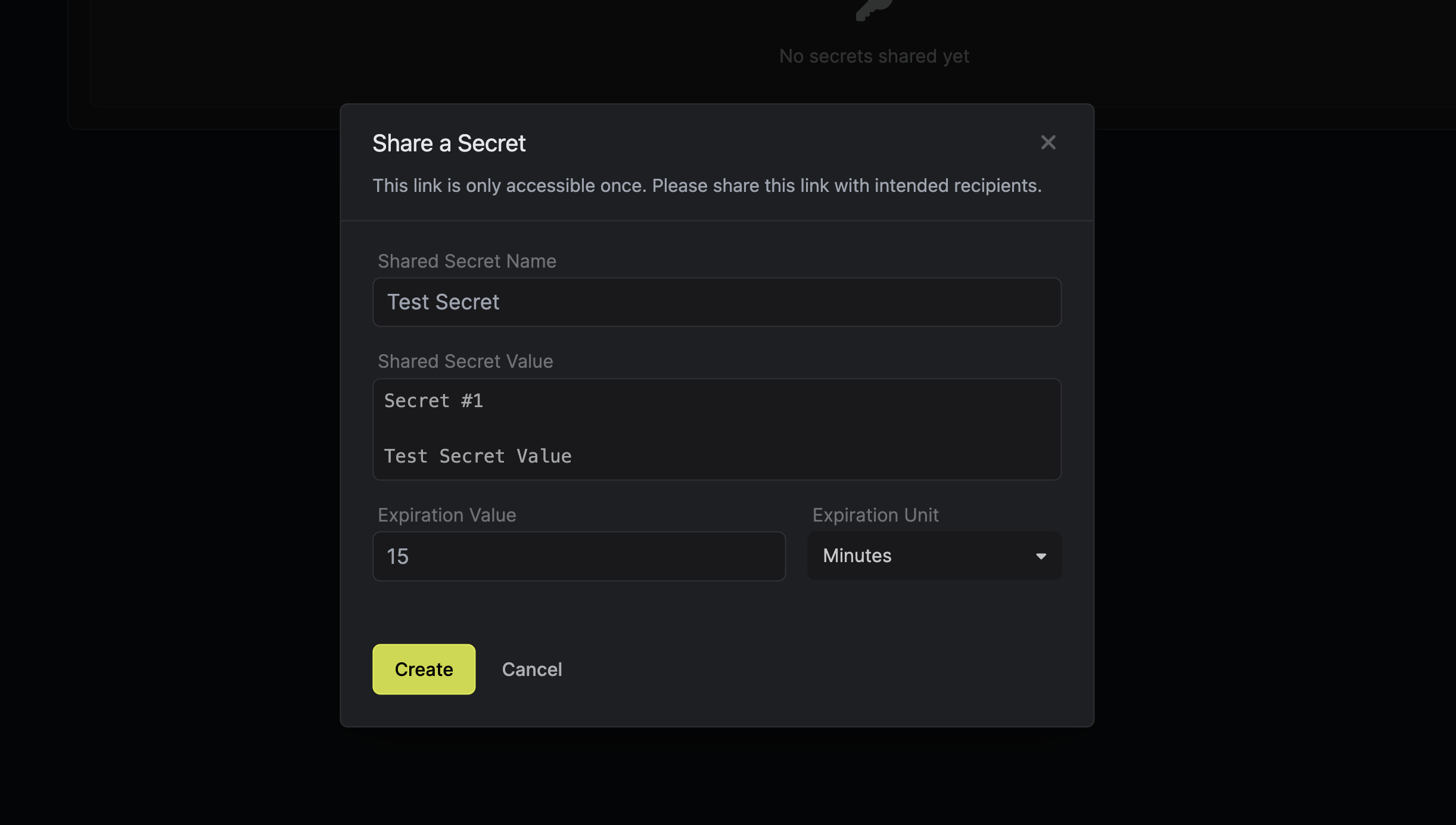
2: Secret Sharing Infrastructure
Developers frequently need to share secrets with team members, contractors, or other third parties. This can be risky due to potential leaks or misuse. Infisical now offers a secure solution for sharing secrets over the Internet in a time-bound manner. With its zero-knowledge architecture, secrets shared via Infisical remain unreadable even to Infisical itself.
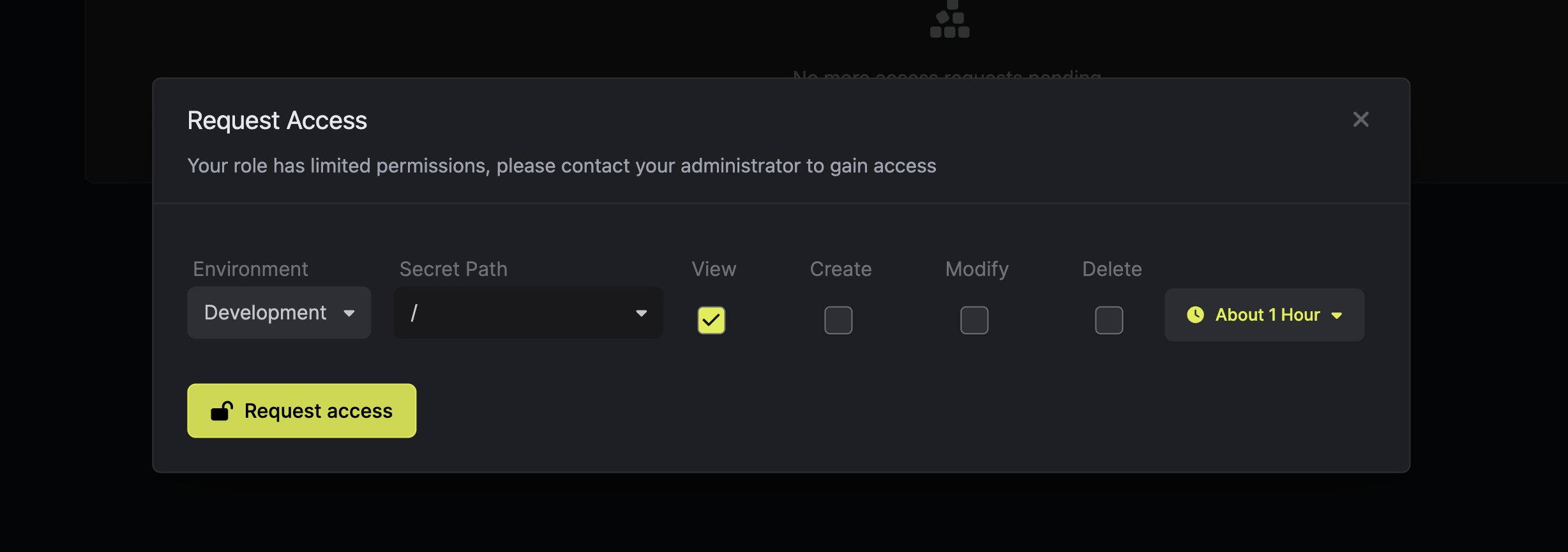
3: Access Requests and JIT Access
Infisical users can now request access to particular environments, folders, and secrets directly from Infisical. Based on the predefined policies, admins are able to approve or deny such requests to automatically provision access to users. Such access can be either permanent or temporary (also known as Just-in-time Access Provisioning).
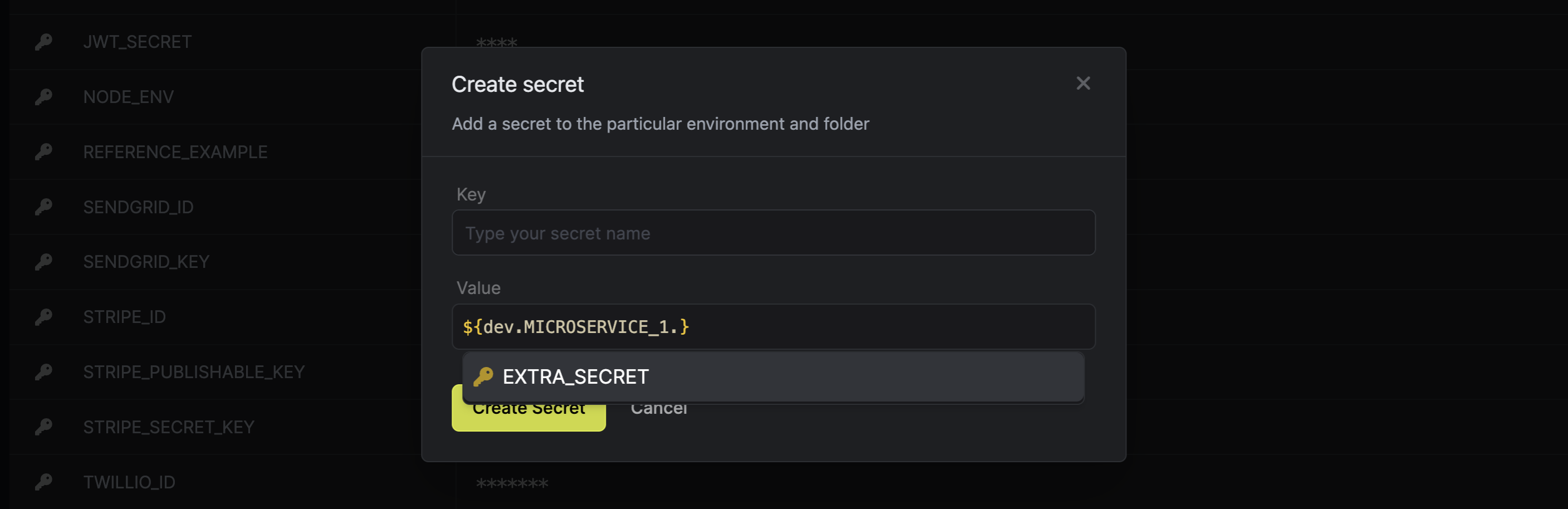
4: Secret Referencing Update
Secret Referencing is probably one of Infisical's most popular features. This month, our team has worked to expand support of secret references and imports to all Infisical clients (e.g., CLI, Kubernetes Operator, SDKs, integrations, and more) – no matter in which environments you are operating secrets with Infisical, Secret References will now be supported seamlessly.
On top of that, when creating secret references via UI, secret references are now automatically suggested in a dropdown. Just start typing ${} to see a list of possible secret references:
5: Infisical Jenkins Plugin
Even though it was already possible to operate secrets in Jenkins with Infisical CLI, you can now use the official Infisical Jenkins Plugin to fetch secrets in your pipelines and projects. On top of that, secrets are masked in the build log, so users can’t accidentally print them.
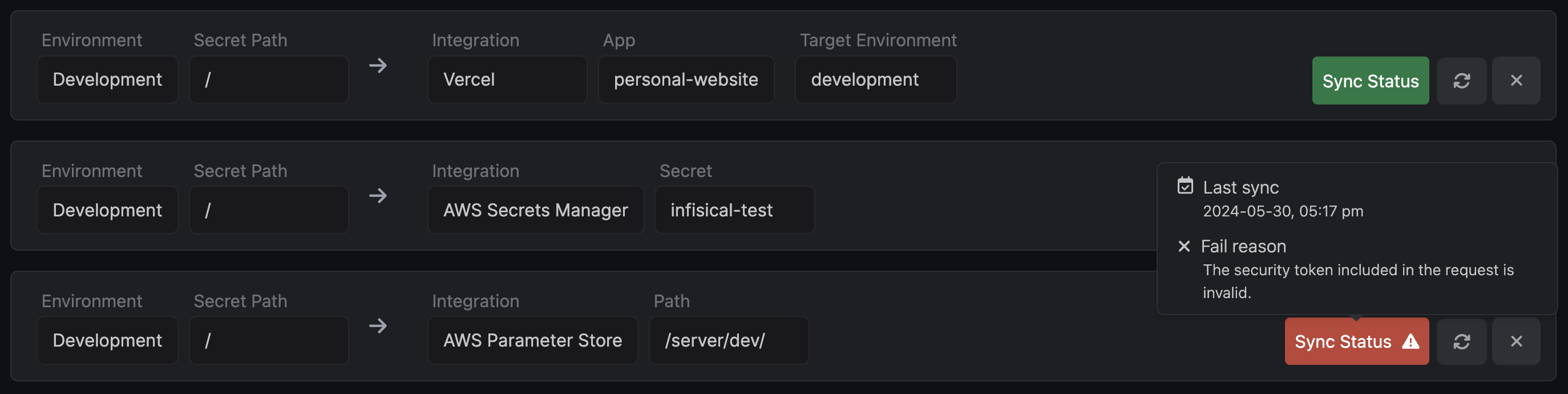
6: Statuses and Manual Sync for integrations
The integration experience has been significantly improved. It is now possible to manually trigger integrations. In addition, users can easily track statuses of their integrations as well as corresponding failure reasons in case something goes wrong.
Much more
- Audit Log Streaming to any external logging.
- Dynamic Secrets with AWS IAM.
- AWS Secrets Manager and Parameter Store Integrations now support syncing for tags and custom KMS keys.
- SCIM and User Groups now integrate with each other.
- Infisical is now available on AWS Marketplace.
That's it for our May 2024 update! If you have any feature requests or feedback for Infisical, please join our Slack community and share those in the #infisical-feedback channel.
If you have any questions about Infisical Pro or Enterprise, you can contact us at sales@infisical.com or sign up for a demo.

