Prerequisites
- Infisical account
- Docker version 20.10.24 or newer
- Basic knowledge of Docker Swarm
- Git installed on your system
- Familiarity with the Infisical Agent
Objective
Our goal is to deploy an Nginx instance in your Docker Swarm cluster, configured to display Infisical secrets on its landing page. This will provide hands-on experience in fetching and utilizing secrets from Infisical within Docker Swarm. The principles demonstrated here are also applicable to Docker Compose deployments.Cloning the Guide Assets Repository
Start by cloning the Infisical guide assets repository from Github. This repository includes necessary assets for this and other Infisical guides. Focus on the
docker-swarm-with-agent sub-directory, which we’ll use as our working directory.Setting Up Authentication with Infisical
To allow the agent to fetch your Infisical secrets, choose an authentication method for the agent. For this guide, we will use Universal Auth for authentication. Follow the instructions here to generate a client ID and client secret.
Entering Universal Auth Credentials
Copy the client ID and client secret obtained in the previous step into the
client-id and client-secret text files, respectively.Configuring the Infisical Agent
The Infisical Agent will authenticate using Universal Auth and retrieve secrets for rendering as specified in the template(s).
Adjust the
polling-interval to control the frequency of secret updates.In the example template, the secrets are rendered as an HTML page, which will be set as Nginx’s home page to demonstrate successful secret retrieval and utilization.- Agent Configuration
- Secret Template for Agent
infisical-agent-config
Some paths contain
/run/secrets/ because the contents of those files reside in a Docker secret.Creating the Docker Compose File
Define the
infisical-agent and nginx services in your Docker Compose file. infisical-agent will handle secret retrieval and storage. These secrets are stored in a volume, accessible by other services like Nginx.docker-compose.yaml
Verifying Secret Consumption
To confirm that secrets are properly rendered and accessible, navigate to 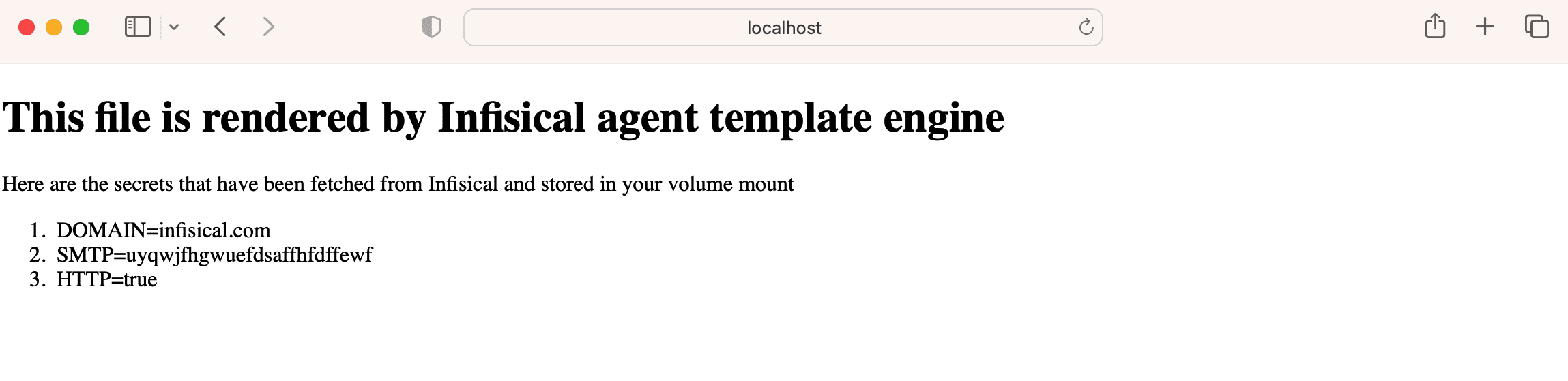
http://localhost. You should see the Infisical secrets displayed on the Nginx landing page.
Considerations
- Secret Updates: Applications that access secrets directly from the volume mount will receive updates in real-time, in accordance with the
polling-intervalset in agent config. - In-Memory Secrets: If your application loads secrets into memory, the new secrets will be available to the application on the next deployment.

