In August 2023, HashiCorp changed their from license MPL 2.0 to to BuSL. This decision has led many companies and developers to look for alternative solutions to HashiCorp tools, including Vault. The good news is there is a number of open source Hashicorp Vault alternatives that provide comprehensive tooling for secret management.
1. Infisical
Infisical is an open source secret management platform. It provides an end-to-end set of tools that cover all aspects of secret management: from encrypted version-controled secret storage, to dynamic secret management, to integrations across infrastructure, to secret scanning, leak prevention, and certificate lifecycle management.
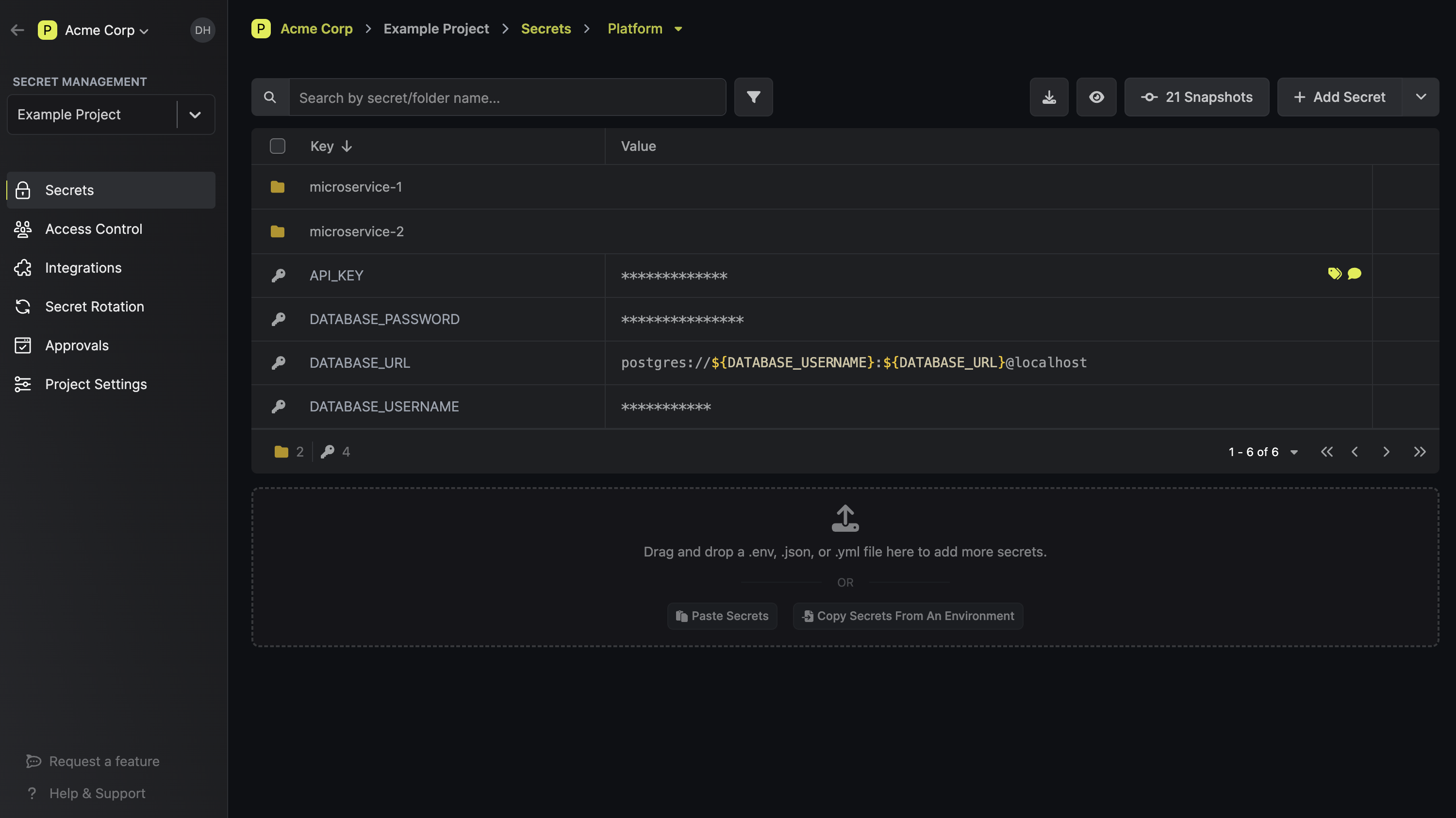
Industry Usage
Infisical supports a myriad of companies and organizations ranging from Fortune 500 companies, to the fastest-growing startups, to international governments.
It is a highly comprehensive solution with a strong community of 10,000s of developers around it. In fact, Infisical is one of the top-10 most popular security projects on GitHub. In addition, Infisical's core functionality is available under the MIT license which makes it much easier to integrate without being slowed down by the organization approval processes.
Infisical Enterprise edition is comparable in feature set with Vault Enterprise, while Infisical as an organization is able to provide 24/7 support and SLAs.
Cost
Despite HashiCorp Vault being a very expensive tool, Infisical provides multiple offerings depending on the needs and budget of any organization. First, Infisical is open source under the MIT license at its core which provides the following functionalities:
- unlimited number of instances, users, projects, environments, secrcets, etc.
- basic access controls;
- all ways of accessing secrets including CLI, API, SDKs, Webhooks, Agent, etc.
- integrations with Kubernetes, Terraform, Ansible, etc.
- integrations with CI/CD tools like GitHub Actions, Circle CI, Jenkins, etc.
- integrations with Cloud platforms like AWS, Vercel, Heroku, and other secret managers;
- secret referencing, importing, and overrides;
- certificate lifecycle management;
- secret scanning and leak prevention;
- secret sharing.
Other more advanced features like multi-region replication or custom role-based access controls are available through an enterprise license which you can easily request by contacting sales@infisical.com or booking a demo directly.
If you are looking for a managed solution, Infisical Cloud provides a generous free tier that also allows for all of the functionality listed above. The rest of the more advanced features can be easily obtained by upgrading to one of the paid tiers.
How does Infisical's feature set compare to HashiCorp Vault?
In short, Infisical provides a more developer-friendly platform with some overlapping and some fairly different tools (e.g., secret scanning and secret sharing).
| Infisical | HashiCorp Vault | |
|---|---|---|
| Open Source <br/> Audit code, contribute to roadmap, and build integrations | ✅ | ❌ |
| Self-hostable <br/> Host on your own infrastructure (if required) | ✅ | ✅ |
| Self-serve Upgrade <br/> Free to try, no mandatory sales calls | ✅ | ❌ |
| Dynamic Secrets and Rotation <br/> Automatically rotate database access tokens and more | ✅ | ✅ |
| Integrations and Ecosystem <br/> Seamlessly integrate with existing tools in your ecosystem | ✅ | ✅ |
| Developer Workflows <br/> Self-serve secrets with Approval Workflows, Access Requests, etc. | ✅ | ❌ |
| Secret Scanning <br/> Automatically identify secret leaks to Git and other systems | ✅ | ❌ |
| Secret Sharing <br/> Share secrets secure among people in and outside of your organization | ✅ | ❌ |
| Encryption as a Service <br/> Secure encryption and decryption of data in-transit | ❌ | ✅ |
| PKI <br/> Create Private CA hierarchies and issue X.509 certificates. | ✅ | ✅ |
| Governance <br/> Audit log, roles-based access, permissions | ✅ | ✅ |
| Developer Community <br/> Wide developer adoption across the world for better reliability and support | ✅ | ✅ |
2. Mozilla SOPS
Mozilla SOPS (Secrets OperationS) is a tool that provides an easy and secure way to manage secrets (such as API keys, passwords, or certificates) in your projects. It's designed to simplify the process of encrypting and decrypting files, ensuring that sensitive data is kept secure. It's not a full-fledged secrets manager but rather a tool for storing sensitive data in encrypted files.
SOPS is praised for its simplicity and ease of setup. It integrates well with CI/CD pipeline tools, and its method of keeping files encrypted on disk and decrypting them in RAM for editing is seen as a secure and convenient feature.
SOPS can integrate with cloud services like AWS KMS, GCP KMS, and Azure Key Vault for key management. This means you can use these services to control access to the encryption keys.
While it's a quick and cheap solution for storing sensitive data, SOPS has its limitations, especially when it comes to API access to secrets. It's not designed for complex secrets management tasks and might not be suitable for expanded use cases.
Cost
Being open-source, SOPS is free to use, making it accessible for a wide range of projects, especially those looking to minimize costs.
Budget Limitations at Mozilla
Due to budget cuts in Mozilla, SOPS is currently not being actively maintained which could lead to unresolved bugs and security issues. It should be noted that the project is currently under a transfer to a different organization which might make its future clearer.
3. Cyberark Conjur
CyberArk Conjur and Conjur Enterprise are a solution designed to fight secret sprawl and integrate with DevOps methodologies, enabling businesses to continuously deliver new applications and functionalities without compromising on security. It is focused on managing application identities and providing secure access to cloud resources.
CyberArk acquired Conjur Inc., the company behind CyberArk Conjur, in 2017. This acquisition marked the integration of Conjur's technology into CyberArk's suite of security solutions.
CyberArk Conjur's important strength lies in its robust security framework. It effectively manages application identities and secures access to cloud resources, which is crucial for businesses operating in highly regulated industries.

Industry Usage
Conjur does not disclose the companies that are using it – which is a very common practive for security companies. It should be noted that Conjur's GitHub project is significantly less popular than Vault or Infisical – it only has around 600 GitHub stars. Partly, this could also be explained by project's GNU Lesser General Public License which is less understandable for developers and organizations. LGPL is more complex and has more conditions compared to the very straightforward MIT License.
The relatively low number of stars on its repository indicates limited engagement from the developer community, which can be a red flag for organizations considering its adoption. Active community engagement is often a good indicator of a product's reliability and the availability of peer support.
Developer Experience
Despite being a versatile tool from the Ops perspective, CyberArk Conjur has been criticized for being overly complex and providing poor developer experience and interface. This aspect is crucial as a user-friendly interface and positive developer experience are essential for widespread adoption and efficient utilization of any tool in tech environments within any organization.
Next to that, it should be noted that the maintenance of CyberArk Conjur can be complex, requiring dedicated resources and expertise. This complexity might result in additional overhead costs for businesses.
Cost
The cost of implementing CyberArk Conjur, especially the enterprise version, can be fairly high. This cost factor might be a significant barrier for small to medium-sized enterprises or startups. For smaller businesses or startups, these costs might be prohibitive.
Something to take into account is that this cost includes not only the software itself but also potential expenses related to deployment, maintenance, and employee training.
It is also important to note that, unlike with Infisical, high availability features are only available in Conjur Enterprise.
4. Building In-House Secret Management Tools
In the realm of secrets management, organizations often face the decision of choosing between off-the-shelf solutions like Infisical or Vault and developing an in-house system tailored to their specific needs. In the past decade, organizations like Lyft, Pinterest, and Segment have committed to building out their own solutions. While this option can offer high customization, it comes with its own set of challenges and considerations.

Pros of Building an In-House Secrets Management Solution
-
Customization: The most significant advantage of an in-house solution is the ability to tailor it precisely to your infrastructure and operational needs. This customization can result in a system that aligns perfectly with your existing workflows, systems, and security policies.
-
Control Over Updates and Changes: With an in-house system, you have complete control over when and how the system is updated or changed. This can be crucial for organizations operating in highly regulated industries or those with strict internal control requirements.
Cons of Building an In-House Secrets Management Solution
-
Resource-Intensive Development: Developing a secrets management solution in-house requires significant time investment in design, development, and testing. This process can divert valuable IT and development resources away from other critical projects.
-
Ongoing Maintenance and Support: Post-deployment, the system will require continuous maintenance to ensure its efficiency and security. This includes regular updates, patches, and security checks, all of which demand dedicated staff and resources.
-
Audit and Compliance Challenges: Custom-built systems can face heightened scrutiny from auditors, especially in industries with stringent regulatory standards. Ensuring compliance and passing audits can be more challenging as auditors may not be familiar with the custom system, unlike widely recognized commercial products.
-
Security Expertise Requirement: Building a secure and robust secrets management system requires a high level of security expertise. This includes not just the initial build but also ongoing threat assessment and response capabilities.
-
Lack of External Support: Unlike commercial solutions that come with vendor support, an in-house system lacks external support. This means any issues or challenges must be addressed internally, which can be a significant drawback in case of complex problems.
-
Training for New Employees: A custom solution requires specific training for new employees, which can be more resource-intensive compared to using a standard, widely-used solution where employees might already have some familiarity or where extensive training resources are readily available.
-
Scalability Concerns: As the organization grows, the in-house solution might need significant re-engineering to scale effectively, which can be a resource-intensive process.
Is Infisical right for you?
Here's our (short) sales pitch.
We're biased (obviously), but we think Infisical is a perfect HashiCorp Vault replacement if:
- You are looking for a developer-focused solution that will last you many years ahead. With Infisical, you get much more than just a secure key-value storage (e.g., secret scanning, certificate management, secret sharing, and more).
- You value transparency. We're open source and open core under the MIT license.
- You want to try before you buy. Infisical is self-serve with a generous free tier.
Check out our product page and read our documentation to learn more.
If you have any questions or want to schedule a product demo, you can talk to one of our experts.

