PKI architecture is a complex topic and there are many ways to orchestrate
certificate management including renewal operations. For specific guidance and
access to enterprise features, we recommend reaching out to
sales@infisical.com to schedule a demo.
Concept
A certificate is the (X.509) leaf certificate issued for a certificate profile. Once issued, a certificate is kept track of in the certificate inventory where you can manage various aspects of its lifecycle including deployment to cloud key stores, server-side auto-renewal behavior, revocation, and more.Guide to Viewing Certificate Details
You can view comprehensive details for any certificate by clicking on it in the certificates table. This opens the certificate details page where you can see all certificate information and perform management actions.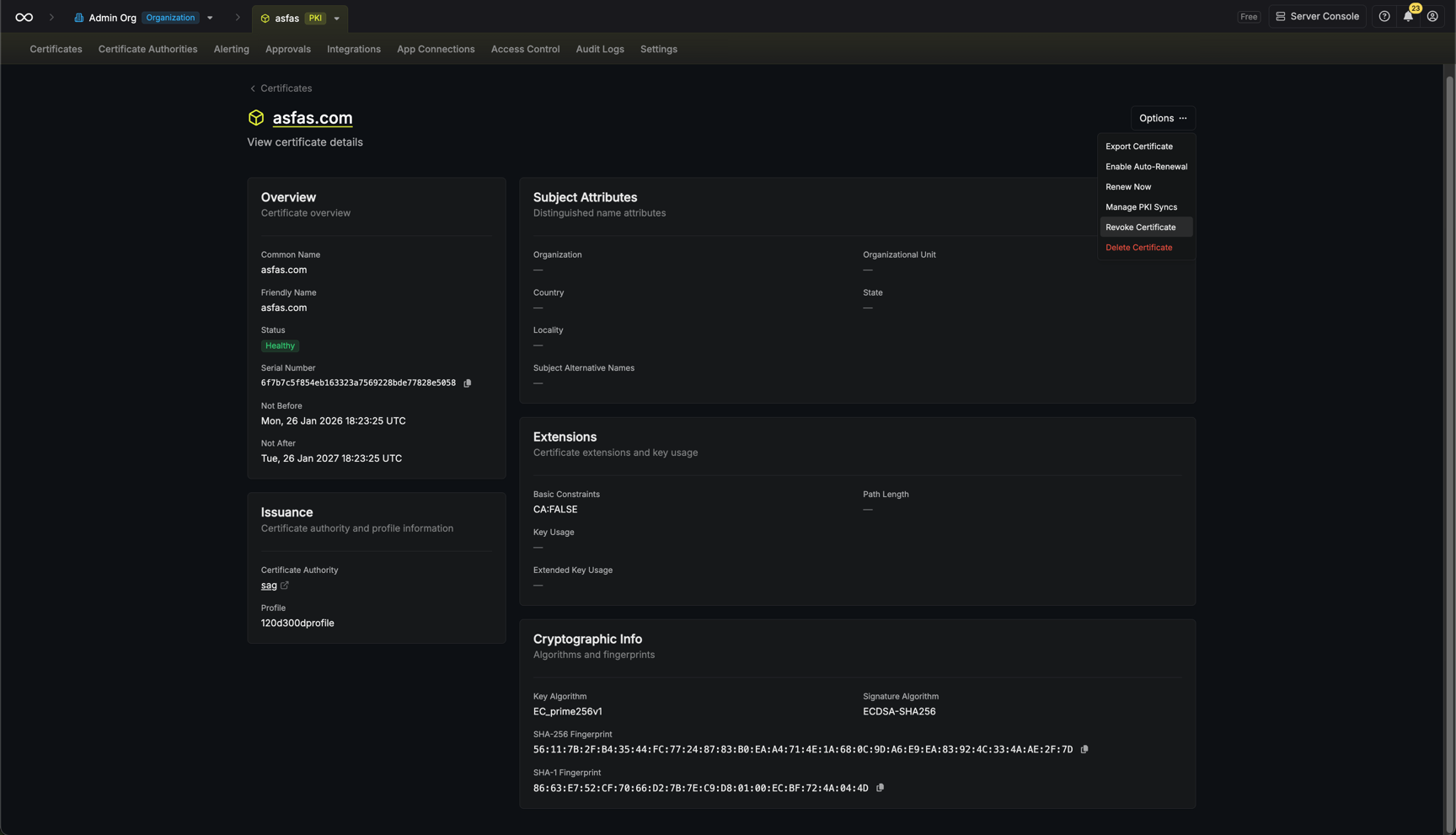
Certificate Information
The details page displays:- Overview: Common name, friendly name, status badge, serial number, and validity period. Dates are shown in UTC with local time available on hover.
- Issuance: The issuing Certificate Authority (with link to CA details), certificate profile used, and renewal chain showing if the certificate was renewed from or has been renewed by another certificate.
- Subject Attributes: Full distinguished name components including Organization, Organizational Unit, Country, State, Locality, and Subject Alternative Names.
- Extensions: Basic constraints (CA flag and path length), Key Usage flags, and Extended Key Usage purposes.
- Cryptographic Info: Key algorithm, signature algorithm, and certificate fingerprints (SHA-256 and SHA-1).
Certificate Metadata
Certificates and certificate requests support custom key-value metadata that can be used to organize and track additional information.-
At issuance: You can attach metadata key-value pairs when issuing a certificate or creating a certificate request through the issuance modal.
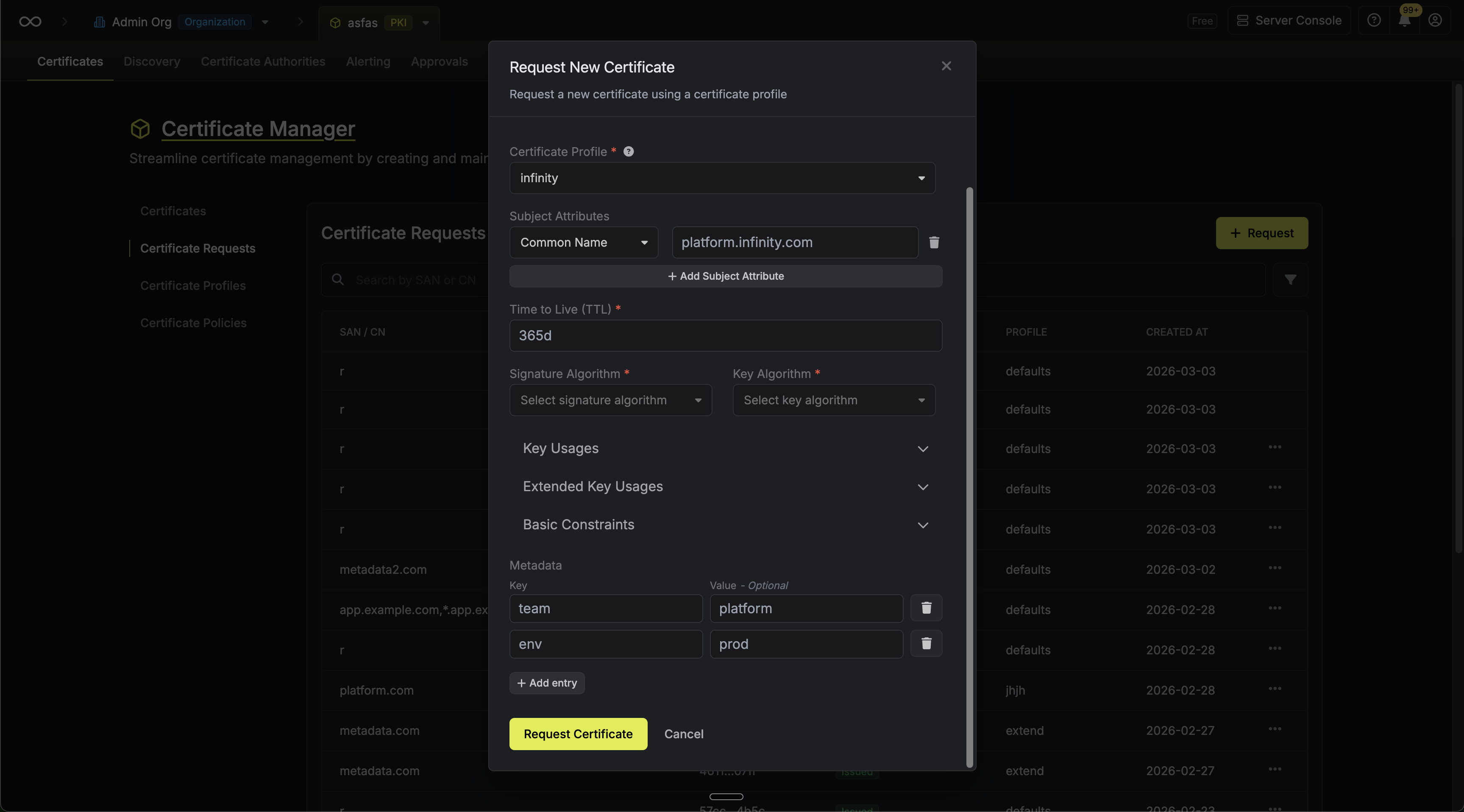
-
On the details page: After issuance, certificate metadata can be viewed and edited from the certificate details page. Certificate request metadata is read-only after creation.
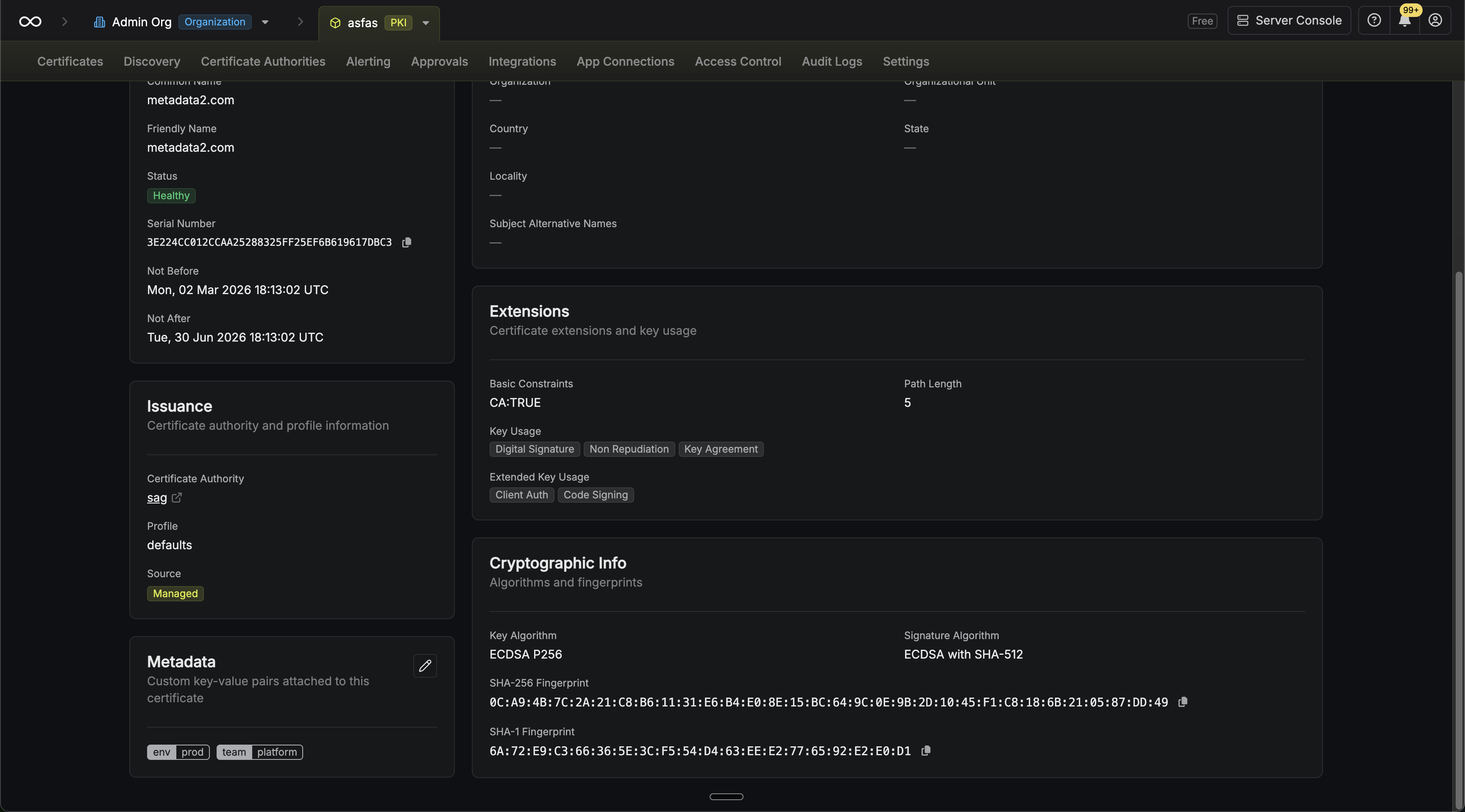
-
Filtering: You can filter the certificates and certificate requests list views by metadata key-value pairs.
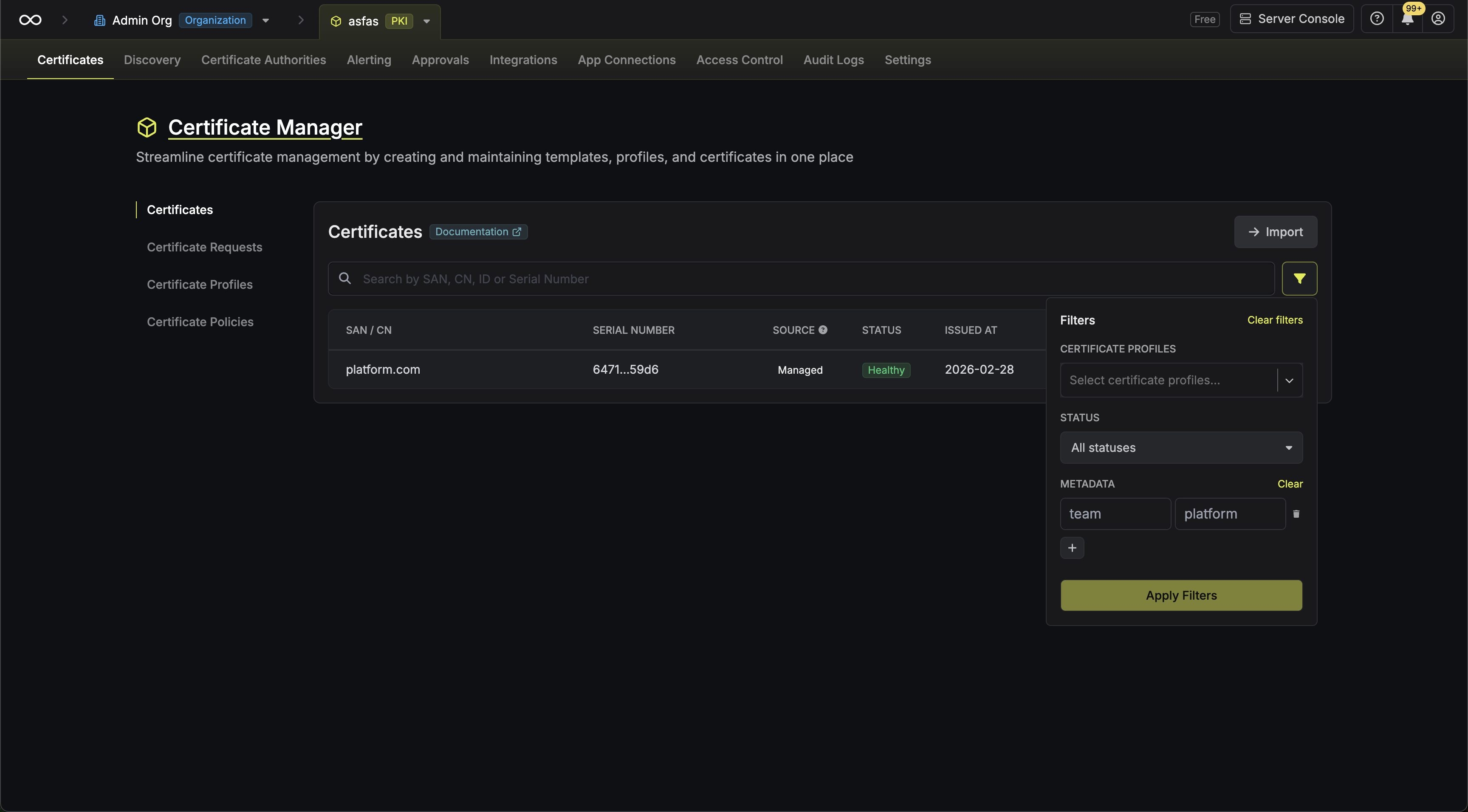
When a certificate is renewed, its metadata is automatically carried over to the renewed certificate.
Managing Certificates
From the certificate details page, you can perform various actions using the Options dropdown menu:- Export Certificate: Download the certificate in PEM or PKCS12 format
- Enable/Manage Auto-Renewal: Configure server-driven certificate renewal (available for API-enrolled certificates with server-generated keys)
- Renew Now: Manually trigger certificate renewal
- Manage PKI Syncs: Configure destinations to sync the certificate to cloud key stores
- Revoke Certificate: Revoke the certificate with a specified reason
- Delete Certificate: Permanently remove the certificate from the inventory
Guide to Issuing Certificates
To issue a certificate, you must first create a certificate profile and a certificate policy to go along with it.- Self-Signed Certificates: To issue a self-signed certificate, you must configure the certificate profile to use the
Self-Signedissuer type. You can then use the API enrollment method to request a self-signed certificate against it. - CA-Issued Certificates: To issue a certificate from a certificate authority, you must configure the certificate profile to use the
Certificate Authorityissuer type and select the issuing CA to use. You can then use one of the enrollment methods to request a certificate against it.
- Infisical UI
- API
Issue a certificate
To issue a certificate, navigate to your Project > Certificates > Certificate Requests and click Request. Select the certificate profile and choose the Request Method:
Select the certificate profile and choose the Request Method: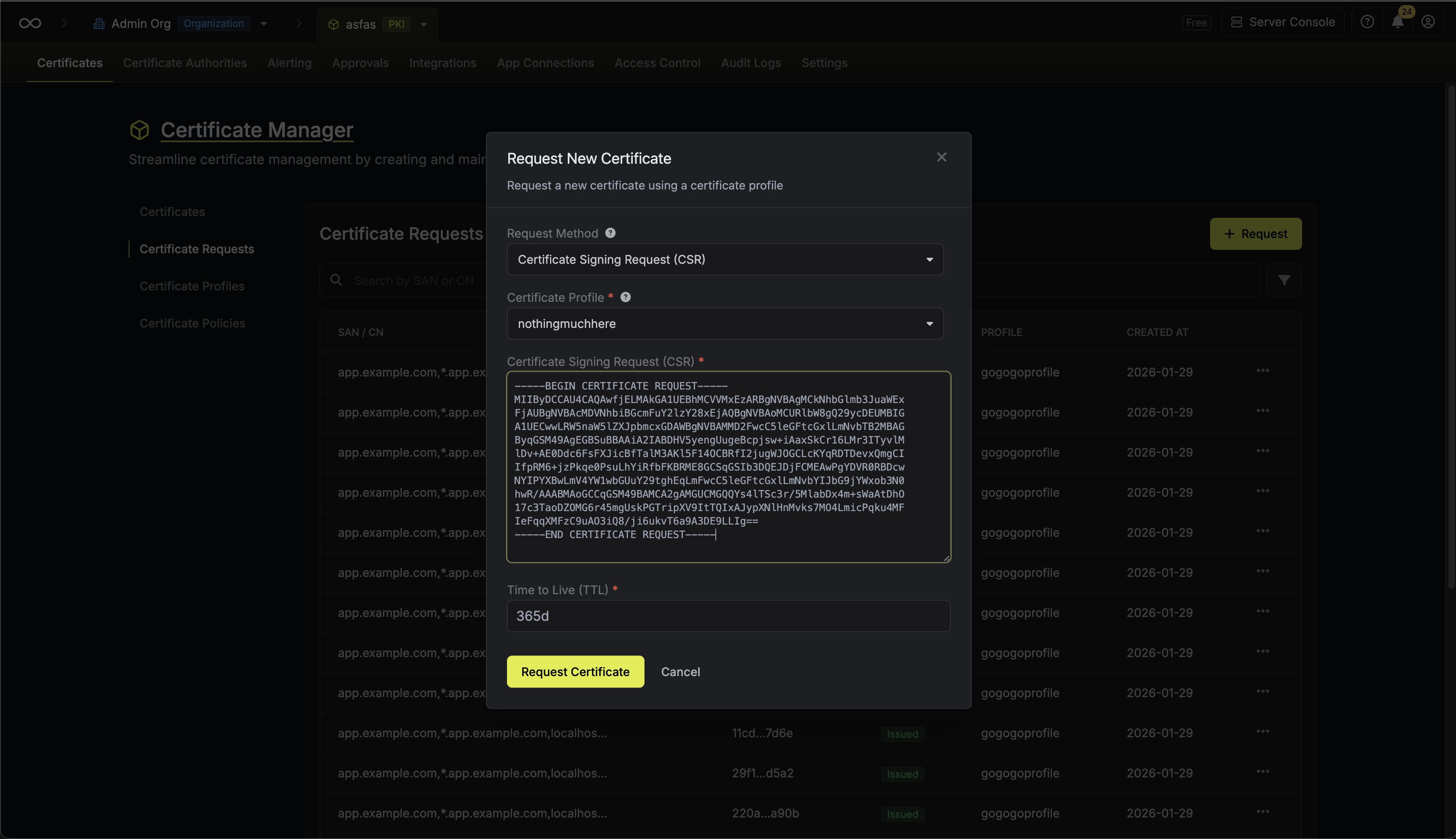
 Select the certificate profile and choose the Request Method:
Select the certificate profile and choose the Request Method:- Managed: Infisical generates and manages the private key for you. Fill out the subject attributes, SANs, algorithms, and other certificate details.
-
CSR (Certificate Signing Request): Provide your own CSR when you need to manage your private key externally. The certificate will be issued using the subject information and public key contained in your CSR. See Issue a Certificate with CSR for more details.


When using a CSR, the subject attributes, subject alternative names, and key algorithm are extracted from your CSR. You only need to specify the TTL for the certificate. The CSR must be a valid PEM-encoded PKCS#10 request.
Guide to Renewing Certificates
To renew a certificate, you can either request a new certificate from a certificate profile or have the platform automatically request a new one for you to be delivered downstream to a target destination. Whether you pursue a client-driven or server-driven approach is totally dependent on the enrollment method configured on your certificate profile as well as your infrastructure use-case.Client-Driven Certificate Renewal
Client-driven certificate renewal is when renewal is initiated client-side by the end-entity consuming the certificate. More specifically, the client (e.g. Infisical Agent, ACME client, etc.) monitors the certificate and makes a request for Infisical to issue a new certificate back to it when the existing certificate is nearing expiration. This is the most common approach to certificate renewal and is suitable for most use-cases.Server-Driven Certificate Renewal
Server-driven certificate renewal is when renewal is initiated server-side by Infisical rather than by the end-entity consuming the certificate. When a certificate considered for auto-renewal meets a specified renewal days before expiration threshold, Infisical reaches out to the issuing CA bound to the certificate profile of the expiring certificate to request for a new one. The resulting renewed certificate is stored in the platform and made available to be fetched back or pushed downstream to end-entities or external systems such as cloud key stores. Note that server-driven certificate renewal is only available for certificates issued via the API enrollment method where key pairs are generated server-side. A certificate can be considered for auto-renewal at time of issuance if the Enable Auto-Renewal By Default option is selected on its certificate profile or after issuance by toggling this option manually.For server-driven certificate renewal workflows, you can programmatically
fetch the latest active certificate bundle for a certificate profile using the
Get Latest Active Certificate
Bundle
API endpoint. This ensures you always retrieve the most current valid
certificate, including any that have been automatically renewed, making it
particularly useful for deployment pipelines and automation workflows where
you don’t want to track individual serial numbers.
- Using the ACME enrollment method, you may connect an ACME client like certbot to fetch back and renew certificates for Apache, Nginx, or other server. The ACME client will pursue a client-driven approach and submit certificate requests upon certificate expiration for you, saving renewed certificates back to the server’s configuration.
- Using the ACME enrollment method, you may use cert-manager with Infisical to issue and renew certificates for Kubernetes workloads; cert-manager will pursue a client-driven approach and submit certificate requests upon certificate expiration for you, saving renewed certificates back to Kubernetes secrets.
- Using the API enrollment method, you may push and auto-renew certificates to AWS and Azure using certificate syncs. Certificates issued over the API enrollment method, where key pairs are generated server-side, are also eligible for server-side auto-renewal; once renewed, certificates are automatically pushed back to their sync destination.
Guide to Downloading Certificates
In the following steps, we explore different options for exporting already-issued certificates from Infisical in different formats for use in your applications and infrastructure.Download Latest Profile Certificate
You can download the latest certificate issued against a certificate profile using the latest certificate bundle endpoint.Download Specific Certificate
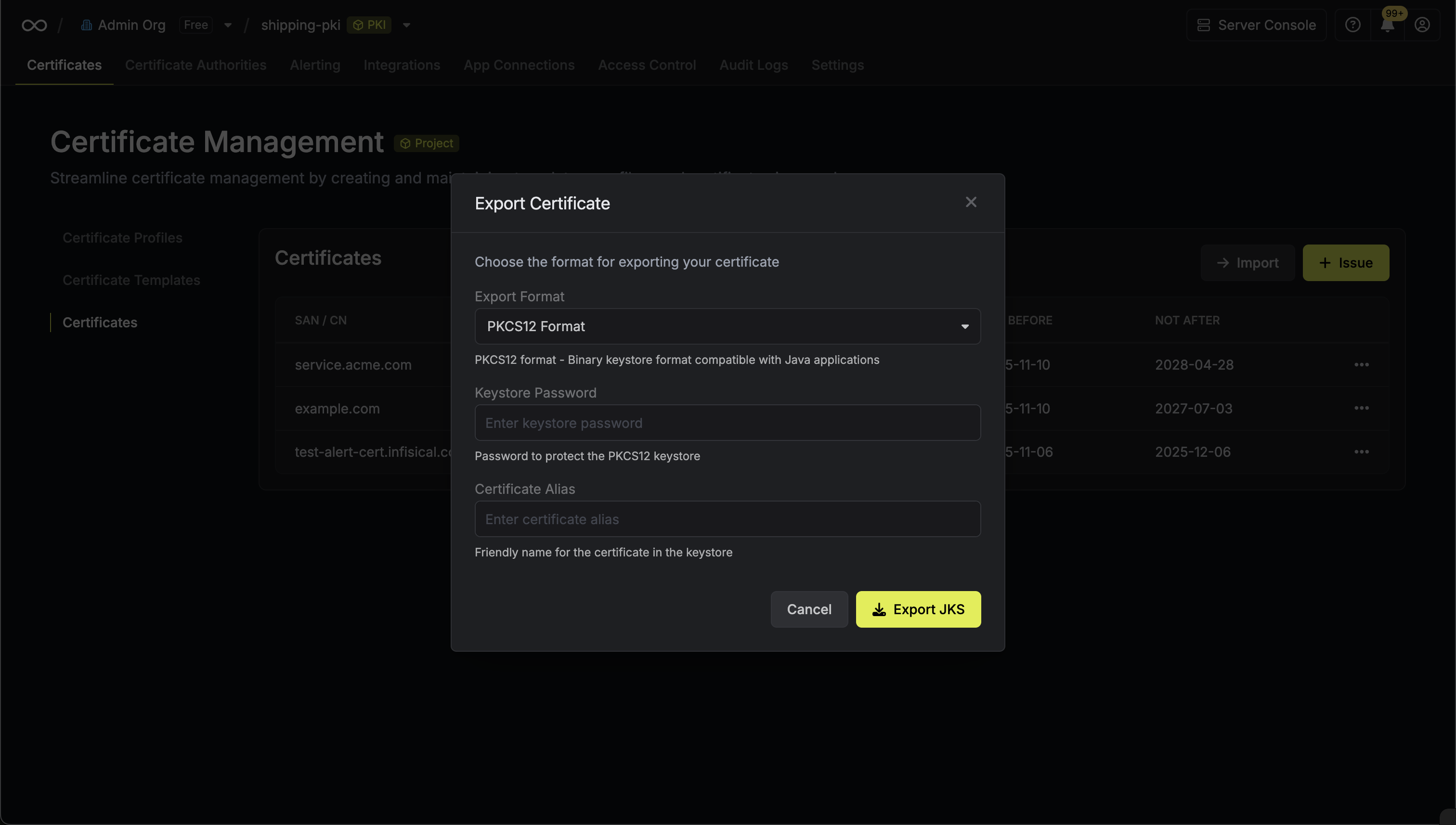
To export a specific certificate, first navigate to your project’s certificate inventory and locate the certificate you want to export. Click on the Export Certificate option from the certificate’s action menu.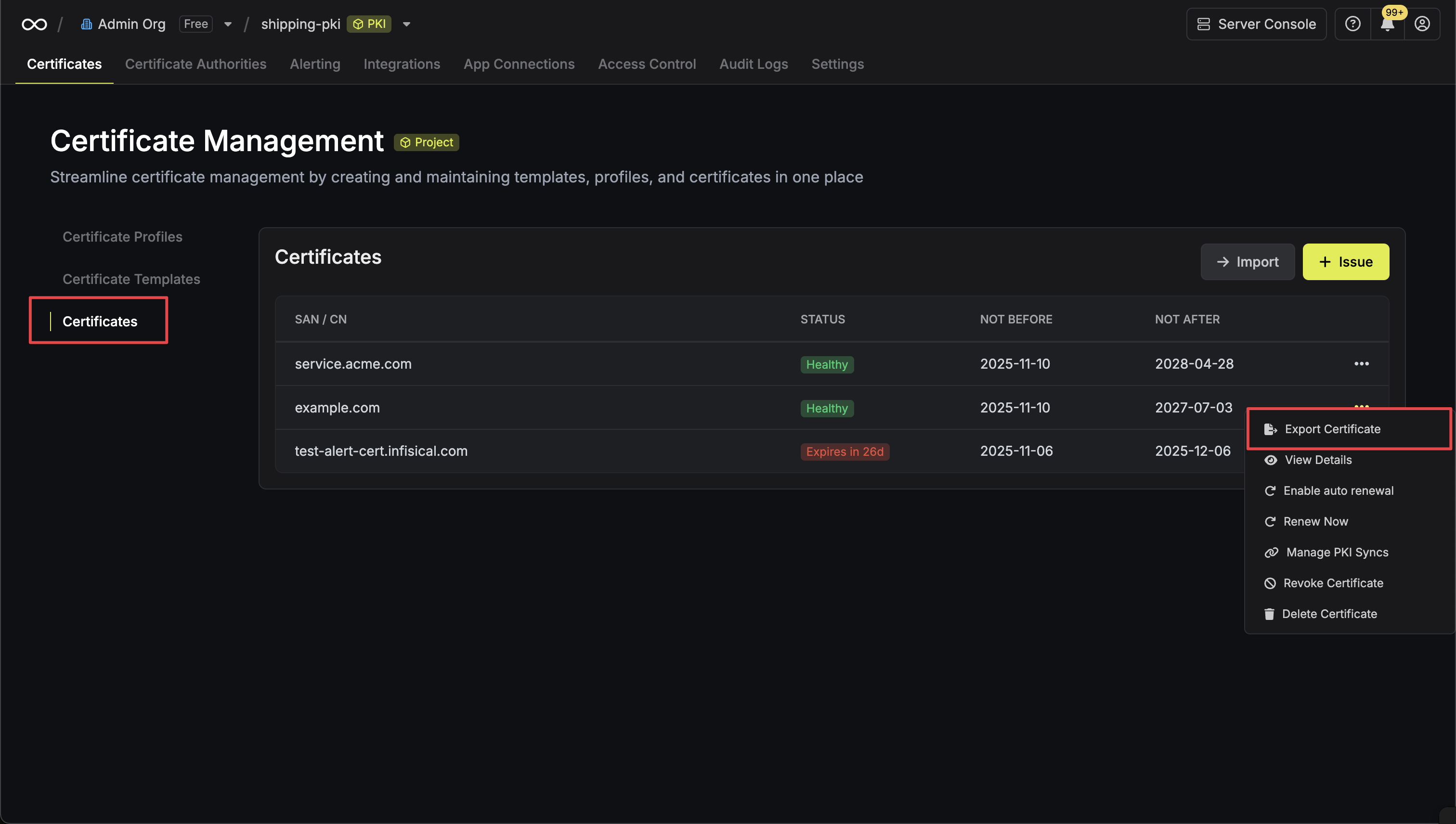
- PEM Format
- PKCS12 Format
Exporting in PEM Format
In the export modal, choose PEM as the format and click Export.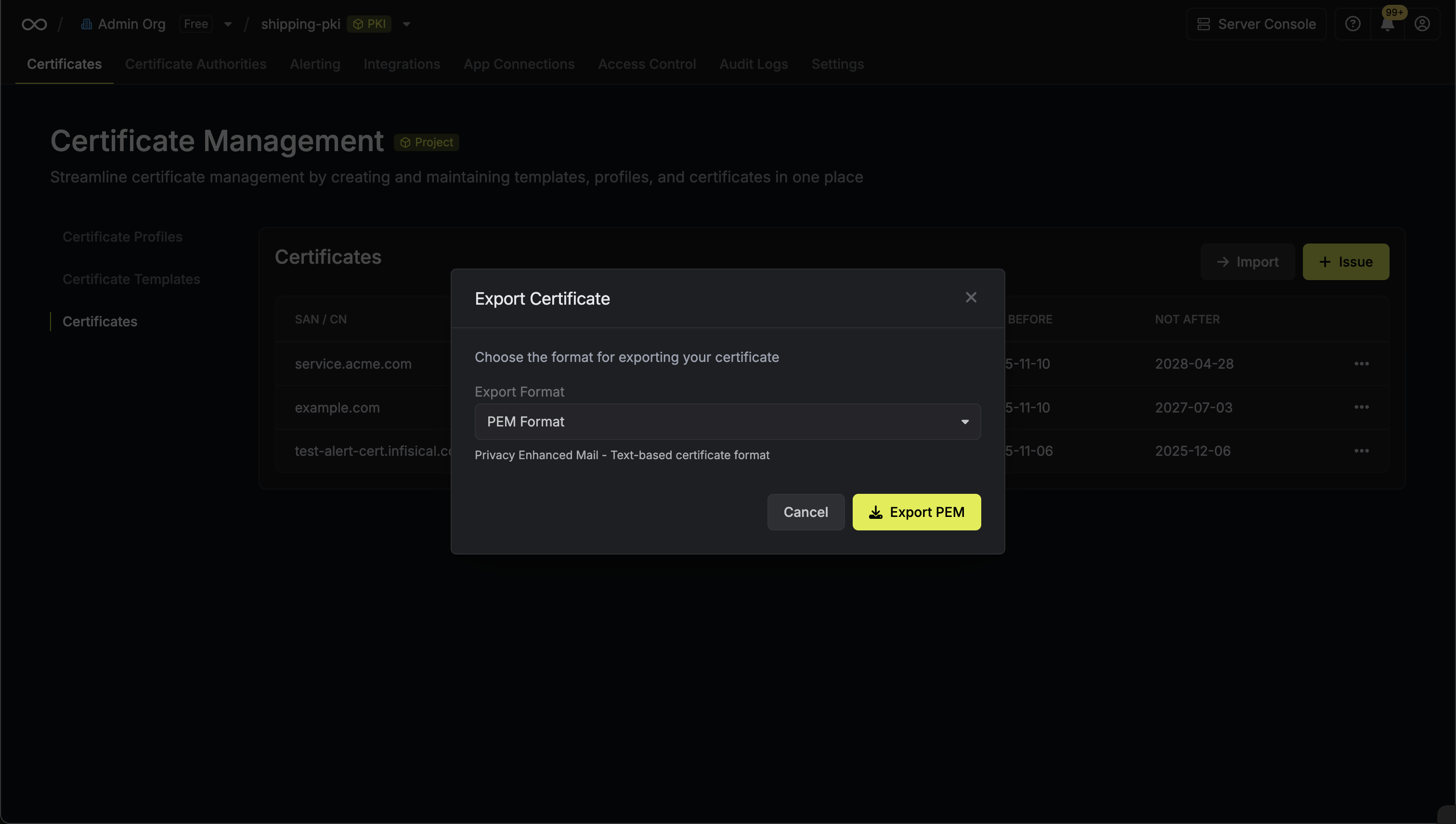 The PEM export modal will display the certificate details including:
The PEM export modal will display the certificate details including:
 The PEM export modal will display the certificate details including:
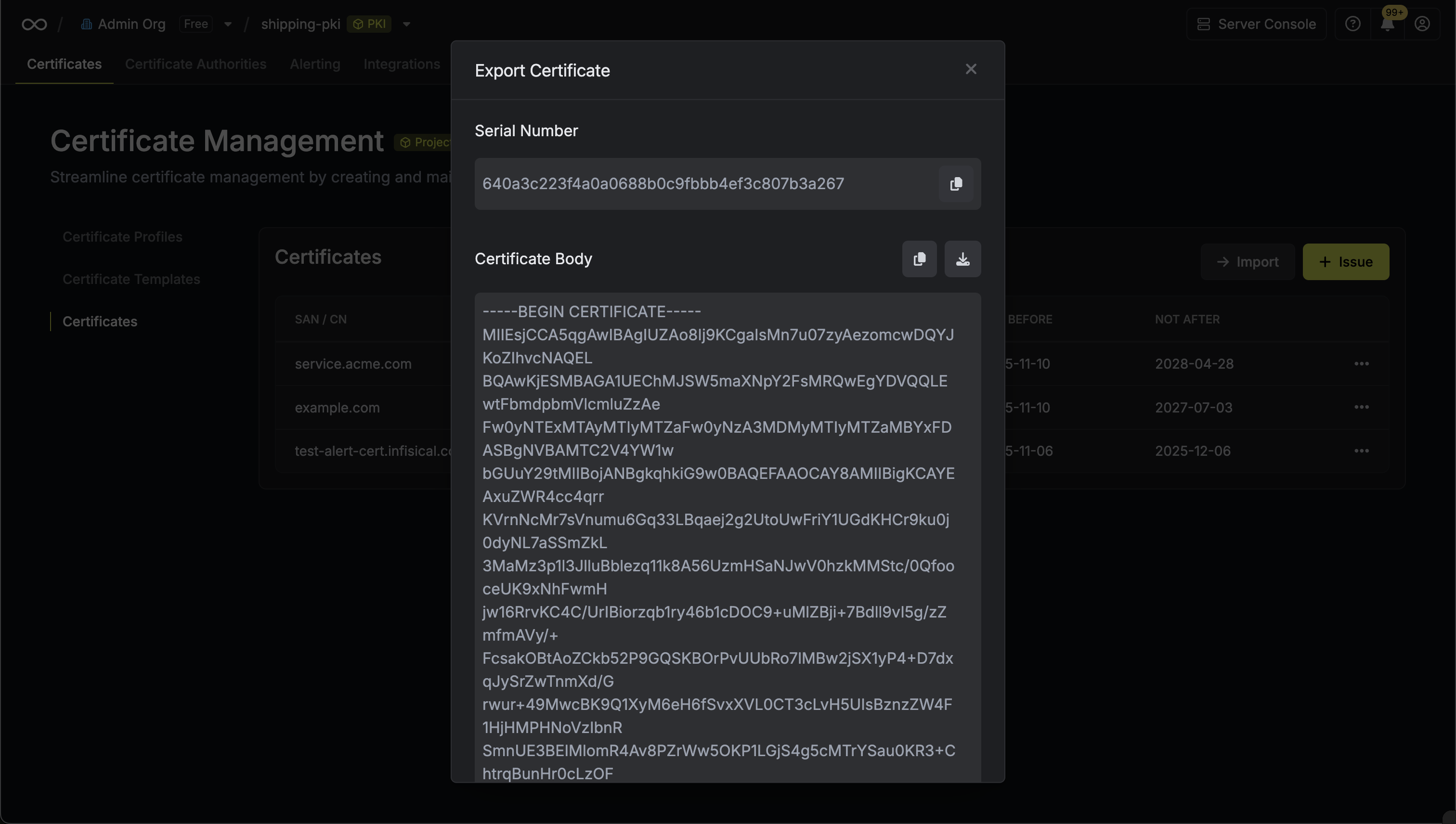
The PEM export modal will display the certificate details including:- Serial Number: The unique identifier for the certificate
- Certificate Body: The X.509 certificate in PEM format
- Certificate Chain: The intermediate and root CA certificates
-
Private Key: The private key associated with the certificate (if available)
Using PEM Certificates
PEM format certificates can be used directly with most web servers and applications:
- Apache HTTP Server: Configure SSL certificates in your virtual host
- Nginx: Use the certificate and private key files in your server configuration
- Docker containers: Mount certificate files for TLS-enabled applications
- Load balancers: Upload PEM certificates to AWS ALB, Azure Application Gateway, etc.
Guide to Revoking Certificates
In the following steps, we explore how to revoke a X.509 certificate and obtain a Certificate Revocation List (CRL) for a CA.- Infisical UI
- API
Revoking a Certificate
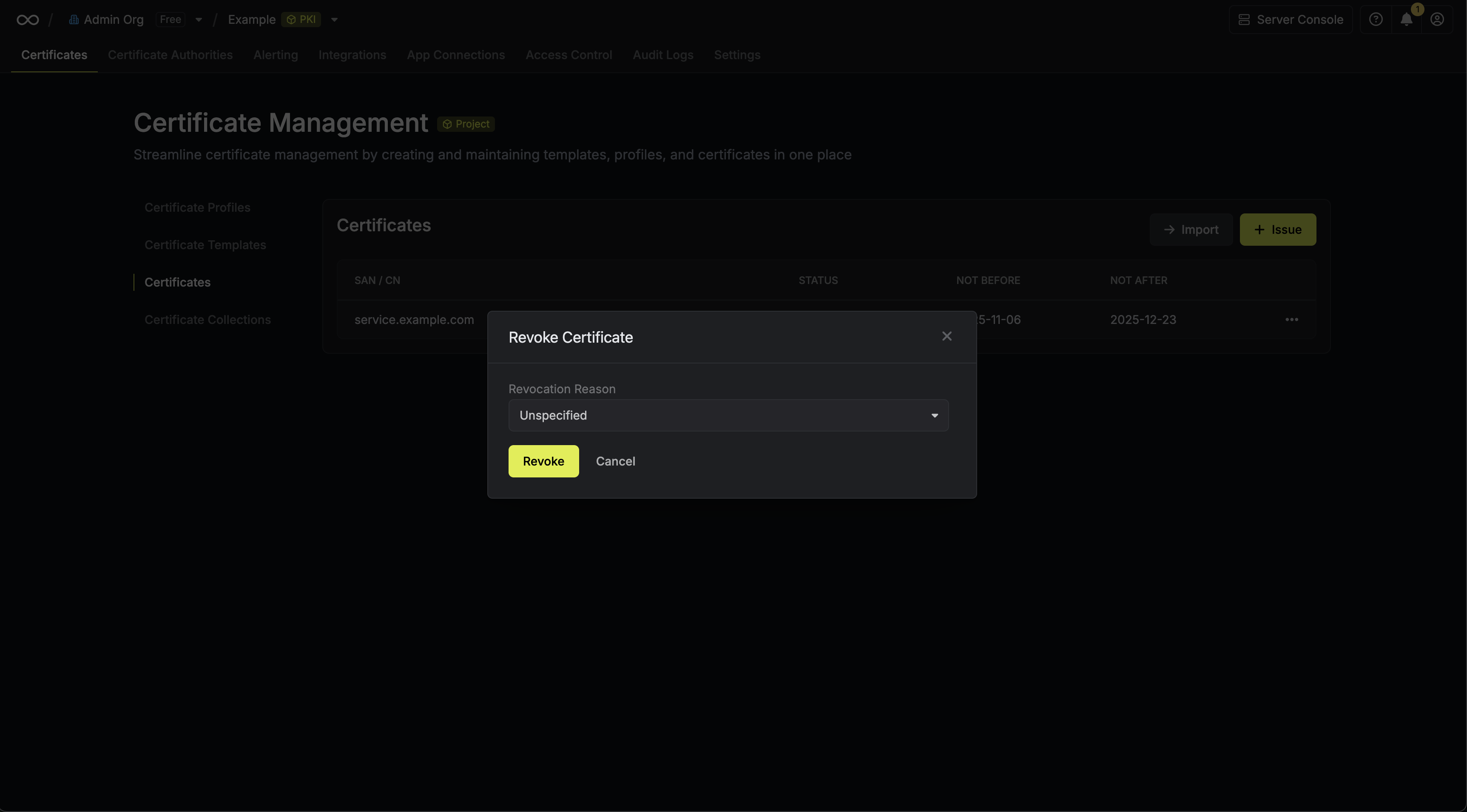
Assuming that you’ve issued a certificate under a CA, you can revoke it by
selecting the Revoke Certificate option for it and specifying the reason
for revocation.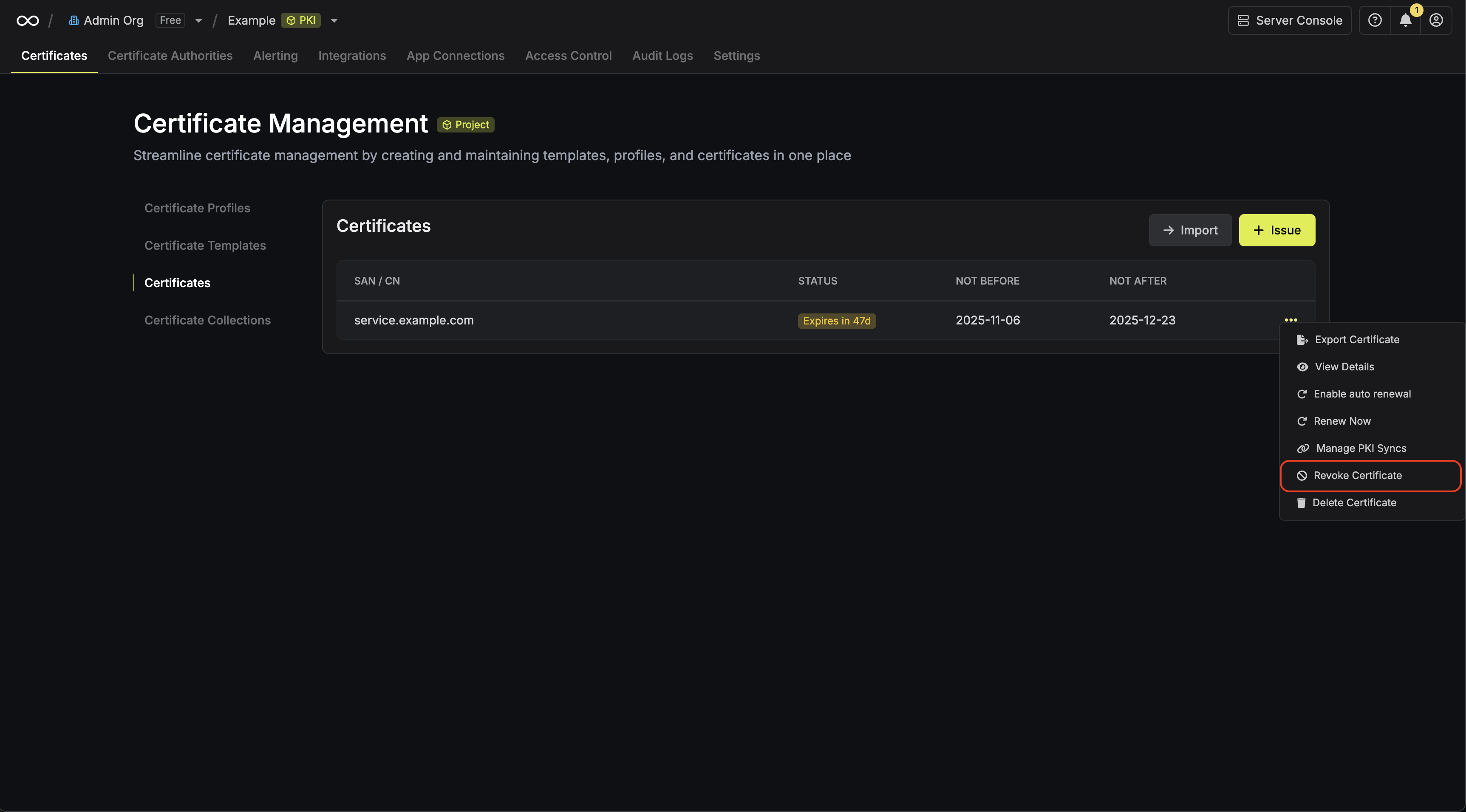


Obtaining a CRL
In order to check the revocation status of a certificate, you can check it
against the CRL of a CA by heading to its Issuing CA and downloading the CRL.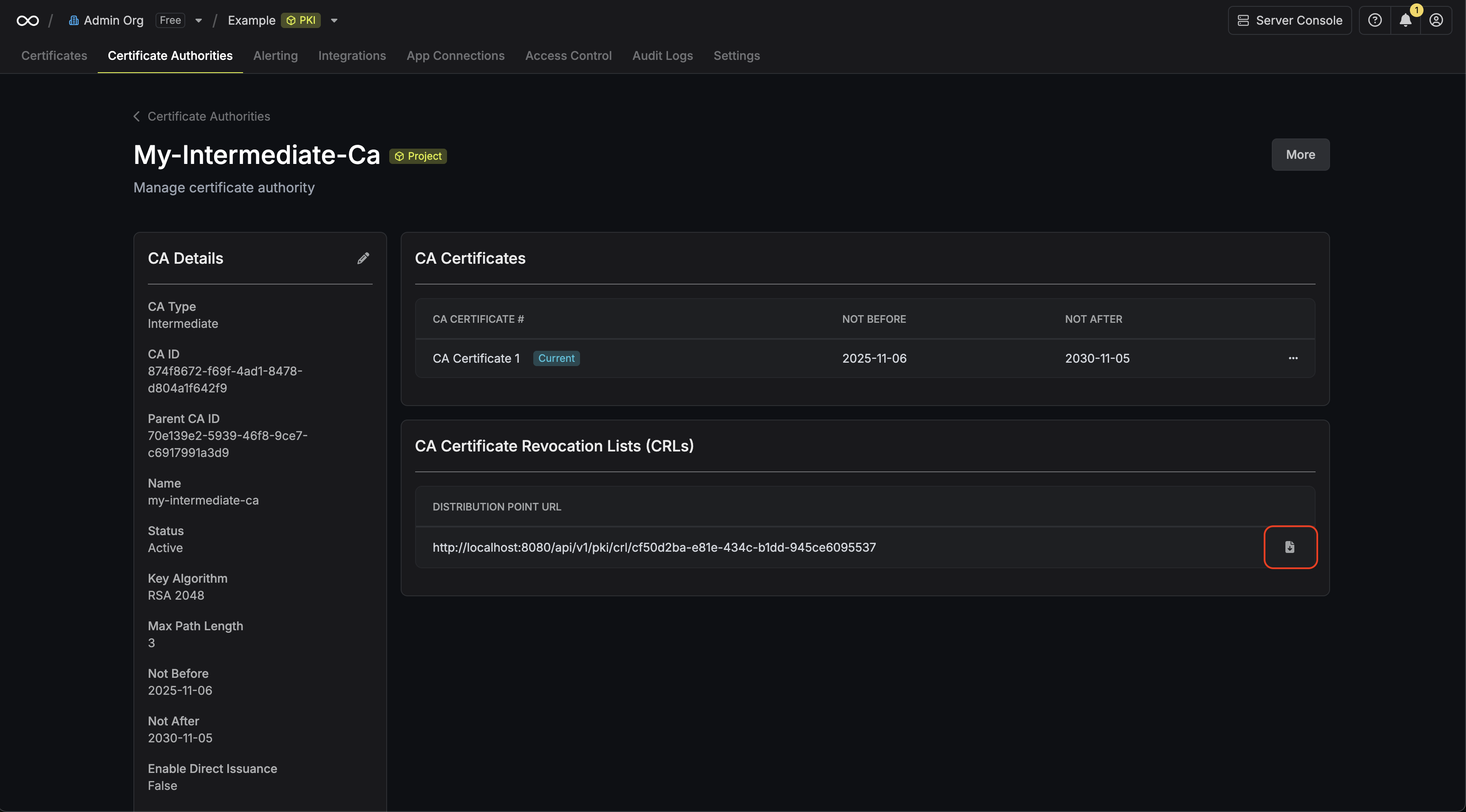 To verify a certificate against the
downloaded CRL with OpenSSL, you can use the following command:Note that you can also obtain the CRL from the certificate itself by
referencing the CRL distribution point extension on the certificate.To check a certificate against the CRL distribution point specified within it with OpenSSL, you can use the following command:
To verify a certificate against the
downloaded CRL with OpenSSL, you can use the following command:Note that you can also obtain the CRL from the certificate itself by
referencing the CRL distribution point extension on the certificate.To check a certificate against the CRL distribution point specified within it with OpenSSL, you can use the following command:
 To verify a certificate against the
downloaded CRL with OpenSSL, you can use the following command:
To verify a certificate against the
downloaded CRL with OpenSSL, you can use the following command: