Core Components
The architecture consists of three main components working in unison:Infisical CLI
The client-side interface used to initiate access requests. It creates a local listener that forwards traffic securely to the Gateway.
Infisical Gateway
A lightweight service deployed within your private network (e.g., VPC, on-prem). It acts as a proxy, intercepting traffic to enforce policies and record sessions before forwarding requests to the target resource.
Access Flow
When a user accesses a resource (e.g., viainfisical access), the following workflow occurs:
- Connection Initiation: The Infisical CLI initiates a connection to the Relay server.
- Tunnel Establishment: The Relay facilitates an end-to-end encrypted tunnel between the CLI and the Gateway.
- Proxy & Credential Injection: The Gateway authenticates the request and connects to the target resource on the user’s behalf. It automatically injects the necessary credentials (e.g., database passwords, SSH keys), ensuring the user never directly handles sensitive secrets.
- Traffic Forwarding: Traffic flows securely from the user’s machine, through the Relay, to the Gateway, and finally to the resource.
Session Recording & Auditing
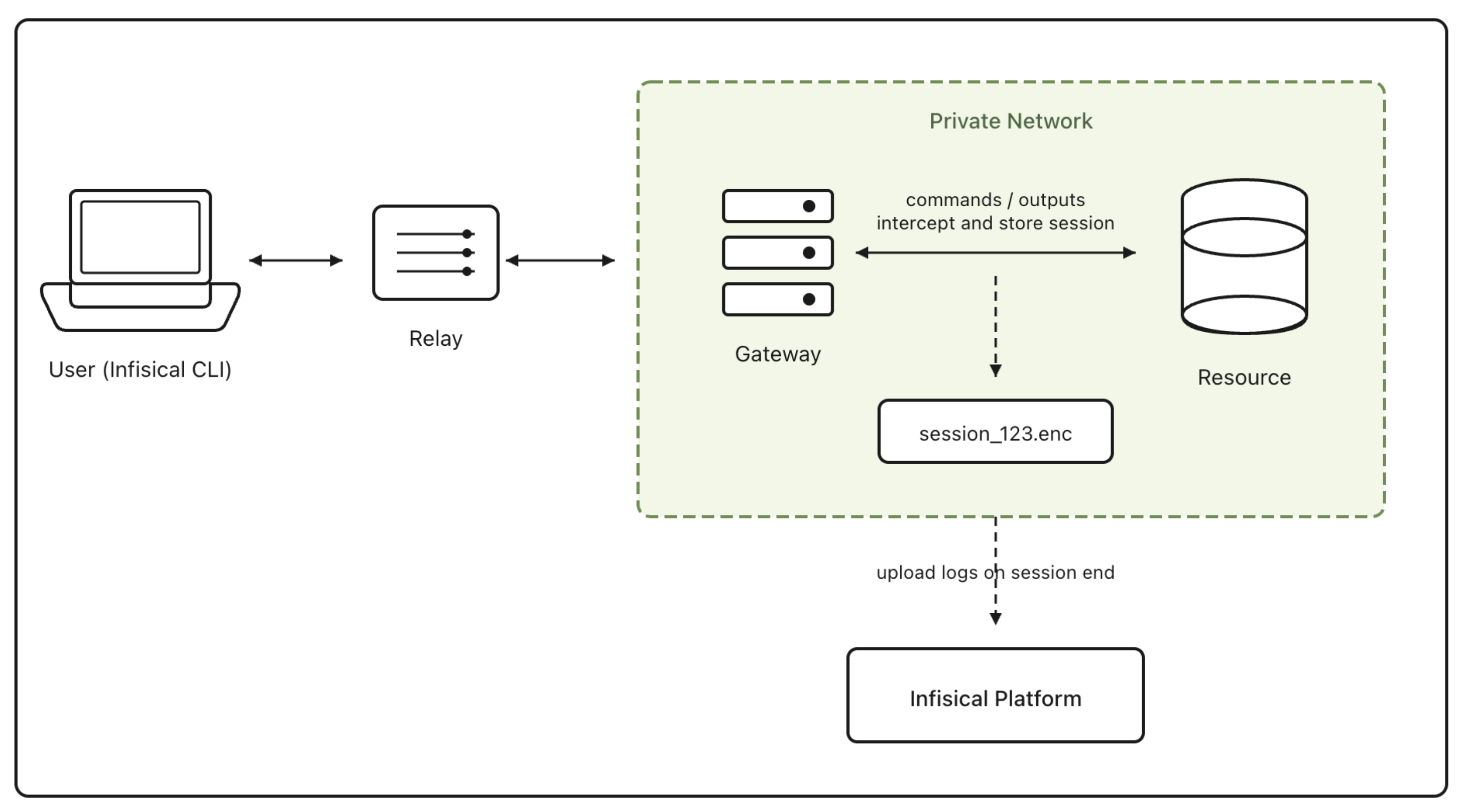 A key feature of the Gateway is its ability to act as a “middleman” for all session traffic.
A key feature of the Gateway is its ability to act as a “middleman” for all session traffic.
- Interception: Because the Gateway sits between the secure tunnel and the target resource, it intercepts all data flowing through the connection.
- Logging: This traffic is logged as part of Session Recording. The Gateway temporarily stores encrypted session logs locally.
- Upload: Once the session concludes, the logs are securely uploaded to the Infisical platform for storage and review.
Security Architecture
The PAM security model allows you to maintain a zero-trust environment while enabling convenient access.End-to-End Encryption
The connection between the Infisical CLI (client) and the Gateway is end-to-end encrypted. The Relay server acts solely as a router for encrypted packets and cannot decrypt or inspect the traffic passing through it.Network Security
The Gateway uses SSH reverse tunnels to connect to the Relay. This design offers significant security benefits:- No Inbound Ports: You do not need to open any inbound firewall ports (like 22 or 5432) to the internet.
- Outbound-Only: The Gateway only requires outbound connectivity to the Relay server and Infisical API.

