Concept
Infisical can be used as a Key Management System (KMS), referred to as Infisical KMS, to centralize management of keys to be used for cryptographic operations like encryption/decryption. By default your Infisical data such as projects and the data within them are encrypted at rest using Infisical’s own KMS. This ensures that your data is secure and protected from unauthorized access. If you are on-premise, your KMS root key will be created at random with theROOT_ENCRYPTION_KEY environment variable. You can also use a Hardware Security Module (HSM), to create the root key. Read more about HSM.
Keys managed in KMS are not extractable from the platform. Additionally, data
is never stored when performing cryptographic operations.
Workflow
The typical workflow for using Infisical KMS consists of the following steps:- Creating a KMS key. As part of this step, you specify a name for the key and the encryption algorithm meant to be used for it (e.g.
AES-GCM-128,AES-GCM-256). - Encryption: To encrypt data, you would make a request to the Infisical KMS API endpoint, specifying the base64-encoded plaintext and the intended key to use for encryption; the API would return the base64-encoded ciphertext.
- Decryption: To decrypt data, you would make a request to the Infisical KMS API endpoint, specifying the base64-encoded ciphertext and the intended key to use for decryption; the API would return the base64-encoded plaintext.
Note that this workflow can be executed via the Infisical UI or manually such
as via API.
Encryption
Guide to Encrypting Data
In the following steps, we explore how to generate a key and use it to encrypt data.- Infisical UI
- API
Creating a KMS key
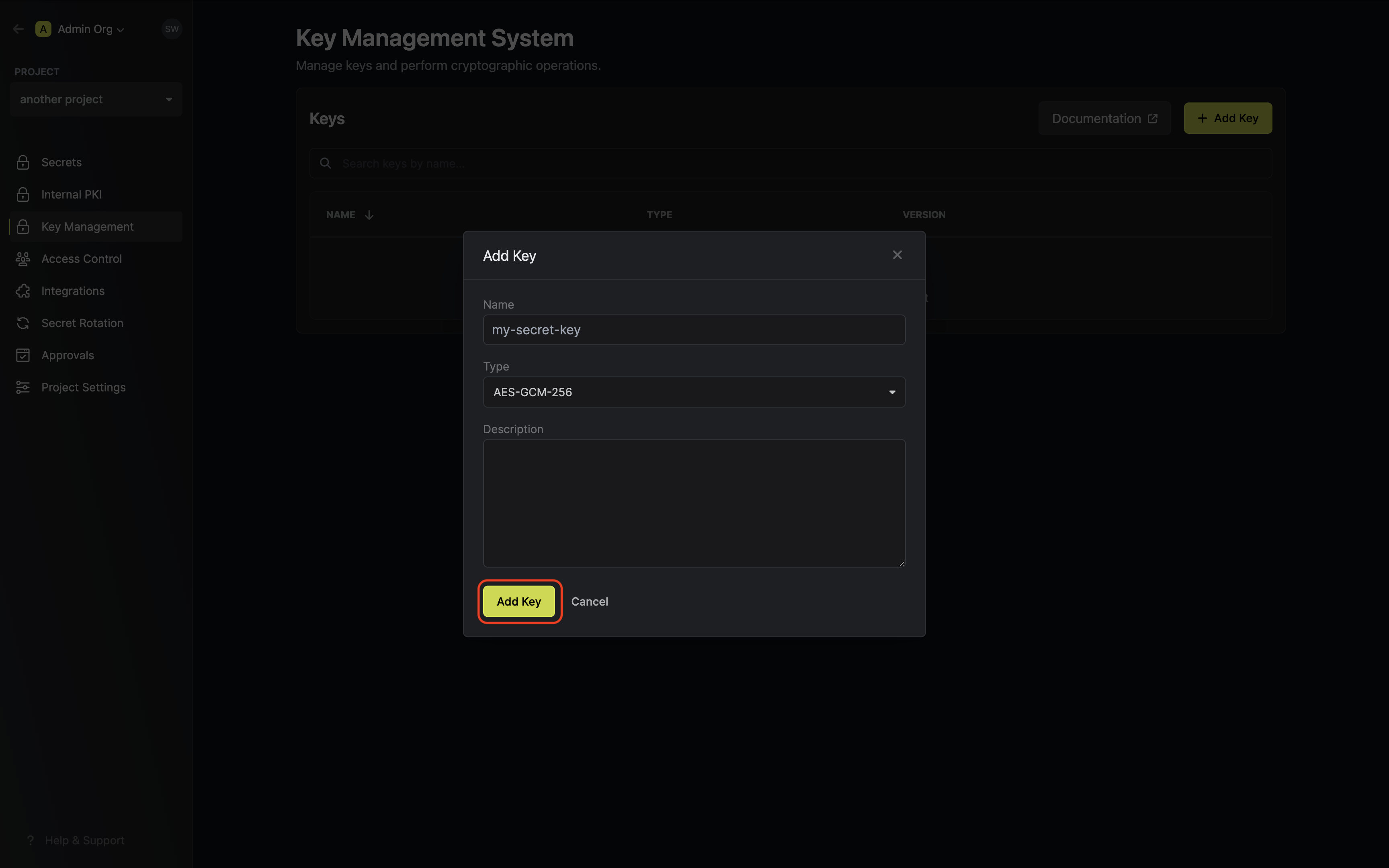
Navigate to Project > Key Management and tap on the Add Key button.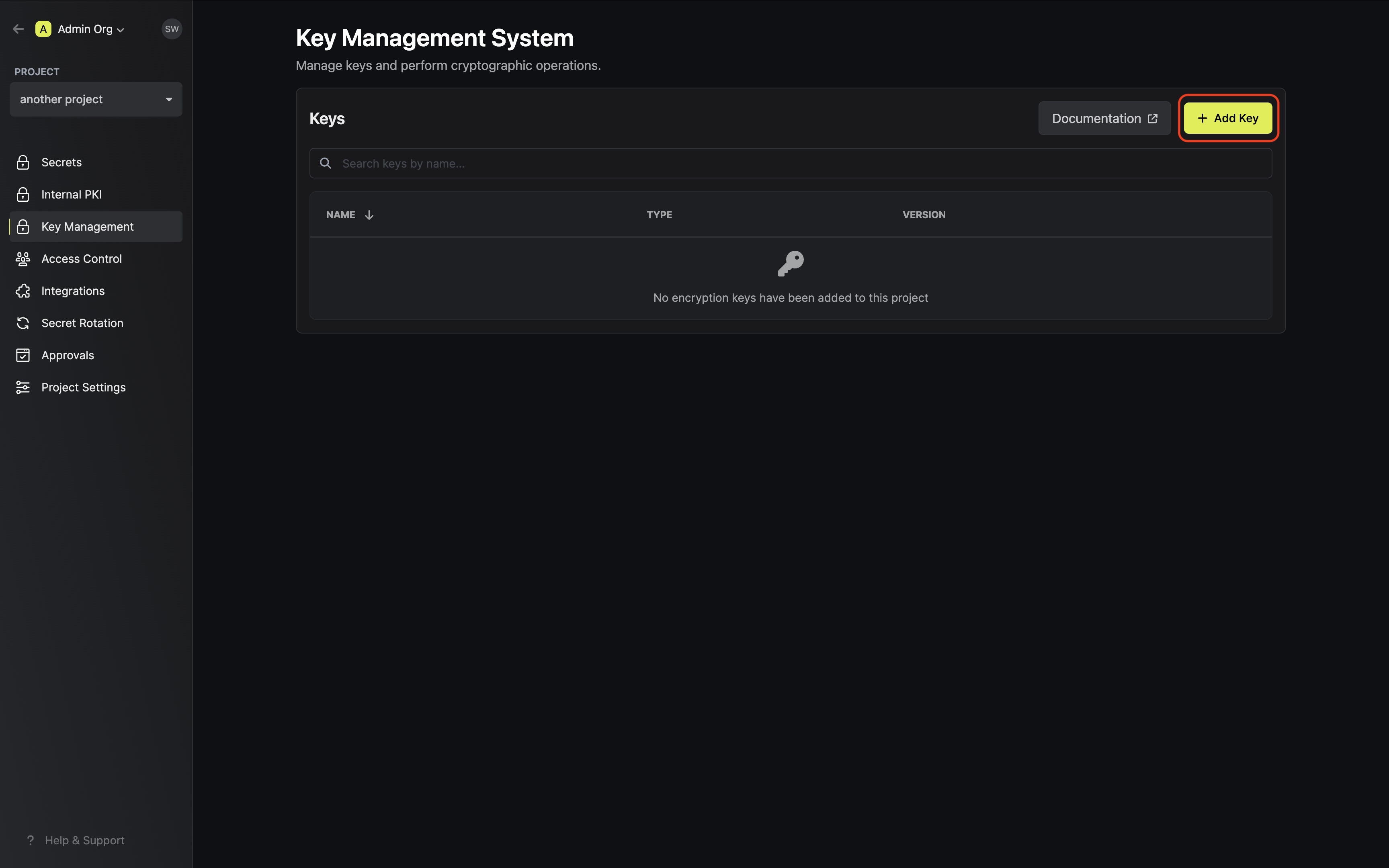 Specify your key details. Here’s some guidance on each field:
Specify your key details. Here’s some guidance on each field:
 Specify your key details. Here’s some guidance on each field:
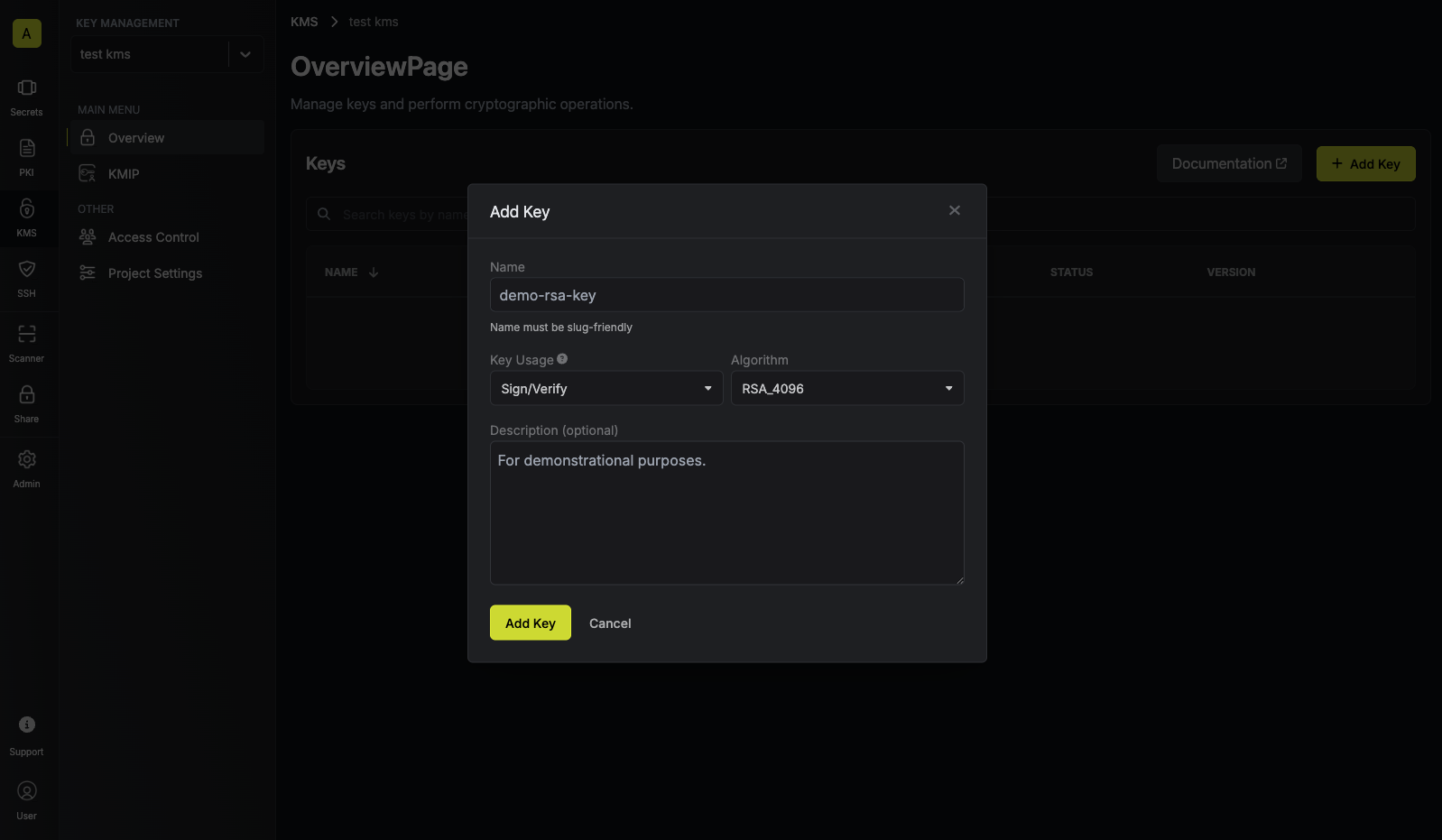
Specify your key details. Here’s some guidance on each field:- Name: A slug-friendly name for the key.
-
Key Usage: The type of key to create (e.g
Encrypt/Decryptfor encryption, andSign/Verifyfor signing). -
Algorithm: The encryption algorithm associated with the key (e.g.
AES-GCM-256). -
Description: An optional description of what the intended usage is for the key.
Encrypting data with the KMS key
Once your key is generated, open the options menu for the newly created key and select encrypt data.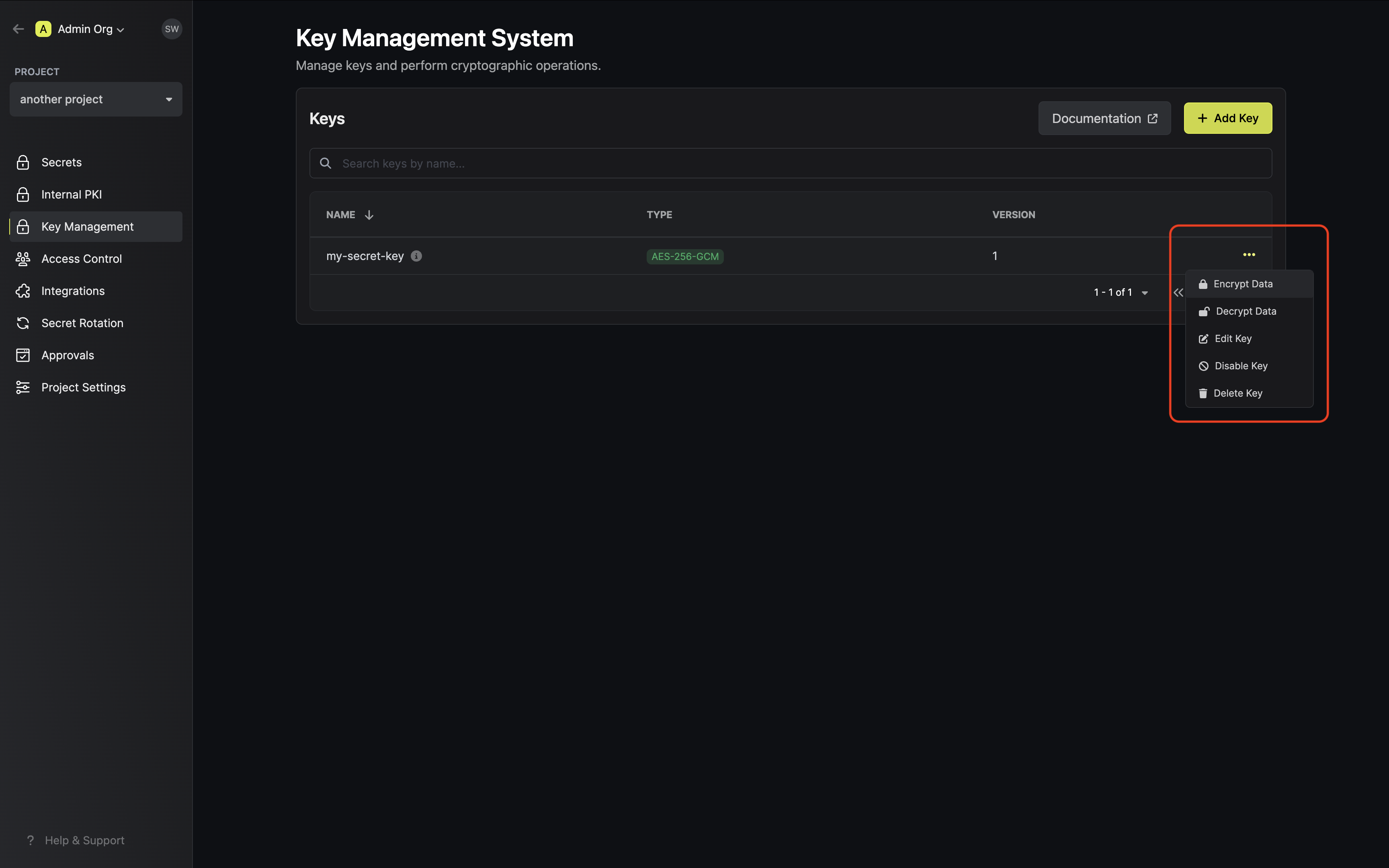 Populate the text area with your data and tap on the Encrypt button.
Populate the text area with your data and tap on the Encrypt button.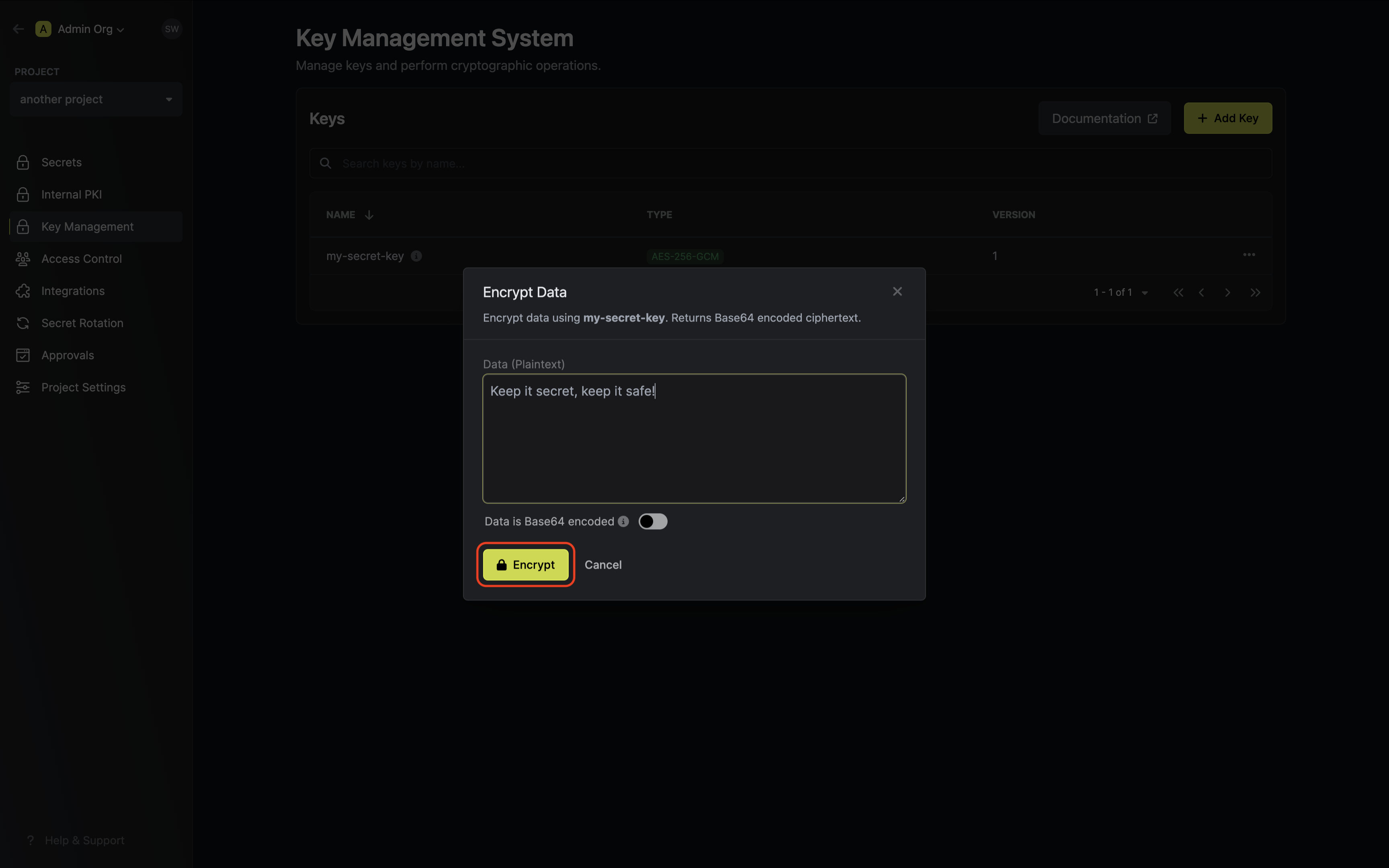 Copy and store the encrypted data.
Copy and store the encrypted data.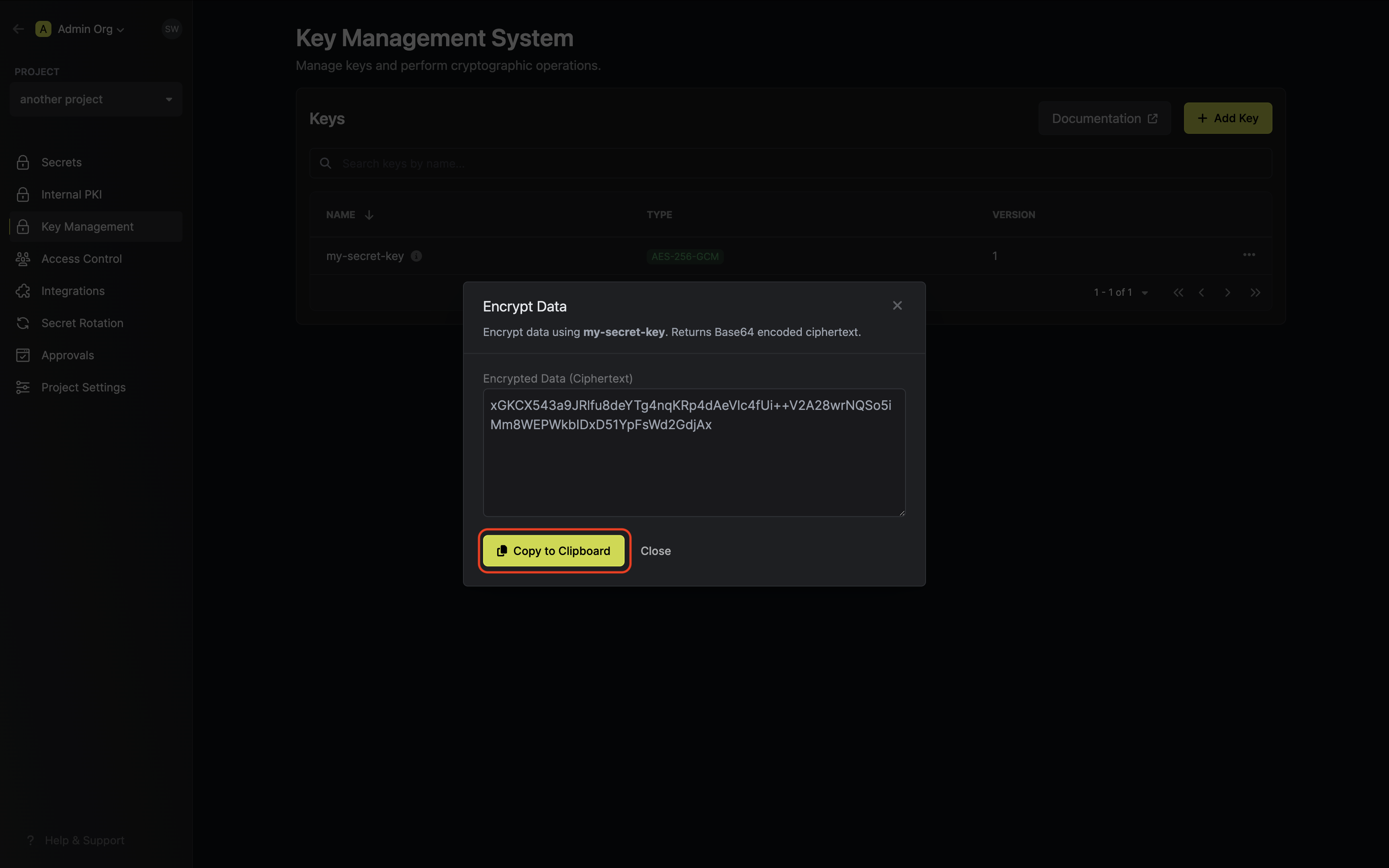
 Populate the text area with your data and tap on the Encrypt button.
Populate the text area with your data and tap on the Encrypt button.
If your data is already Base64 encoded make sure to toggle the respective switch on to avoid
redundant encoding.

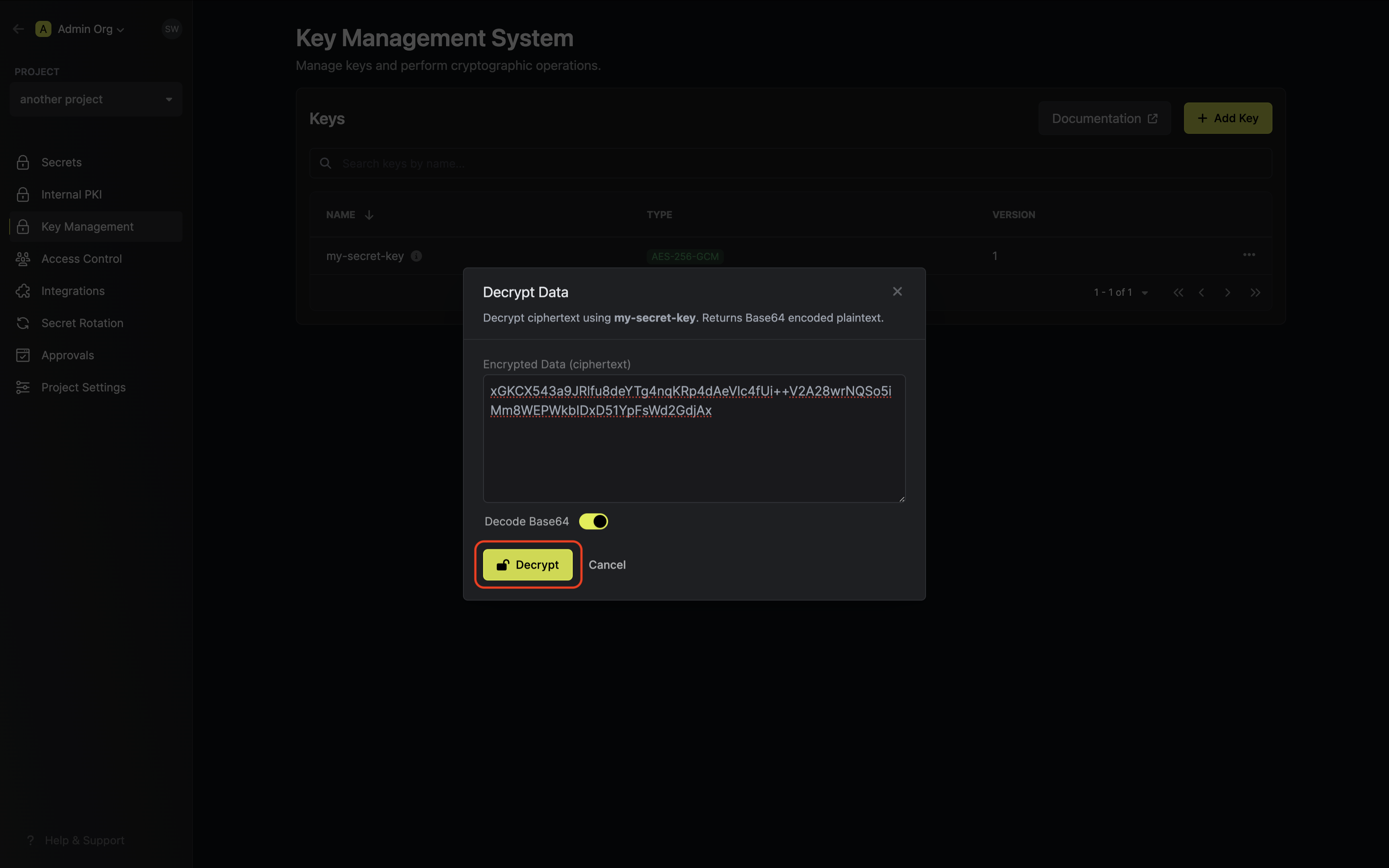
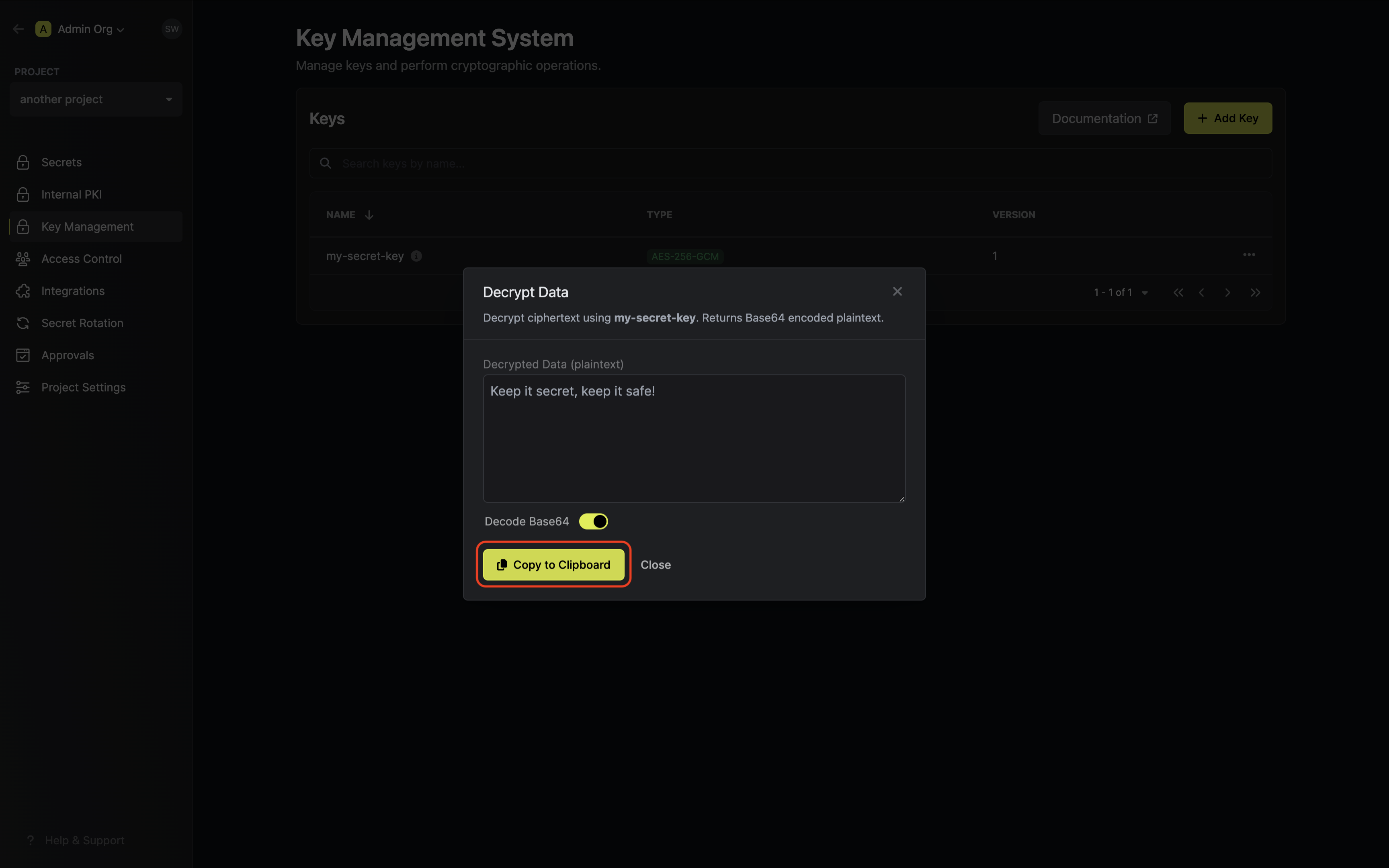
Guide to Decrypting Data
In the following steps, we explore how to use decrypt data using an existing key in Infisical KMS.- Infisical UI
- API
Accessing your key
Navigate to Project > Key Management and open the options menu for the key used to encrypt the data
you want to decrypt.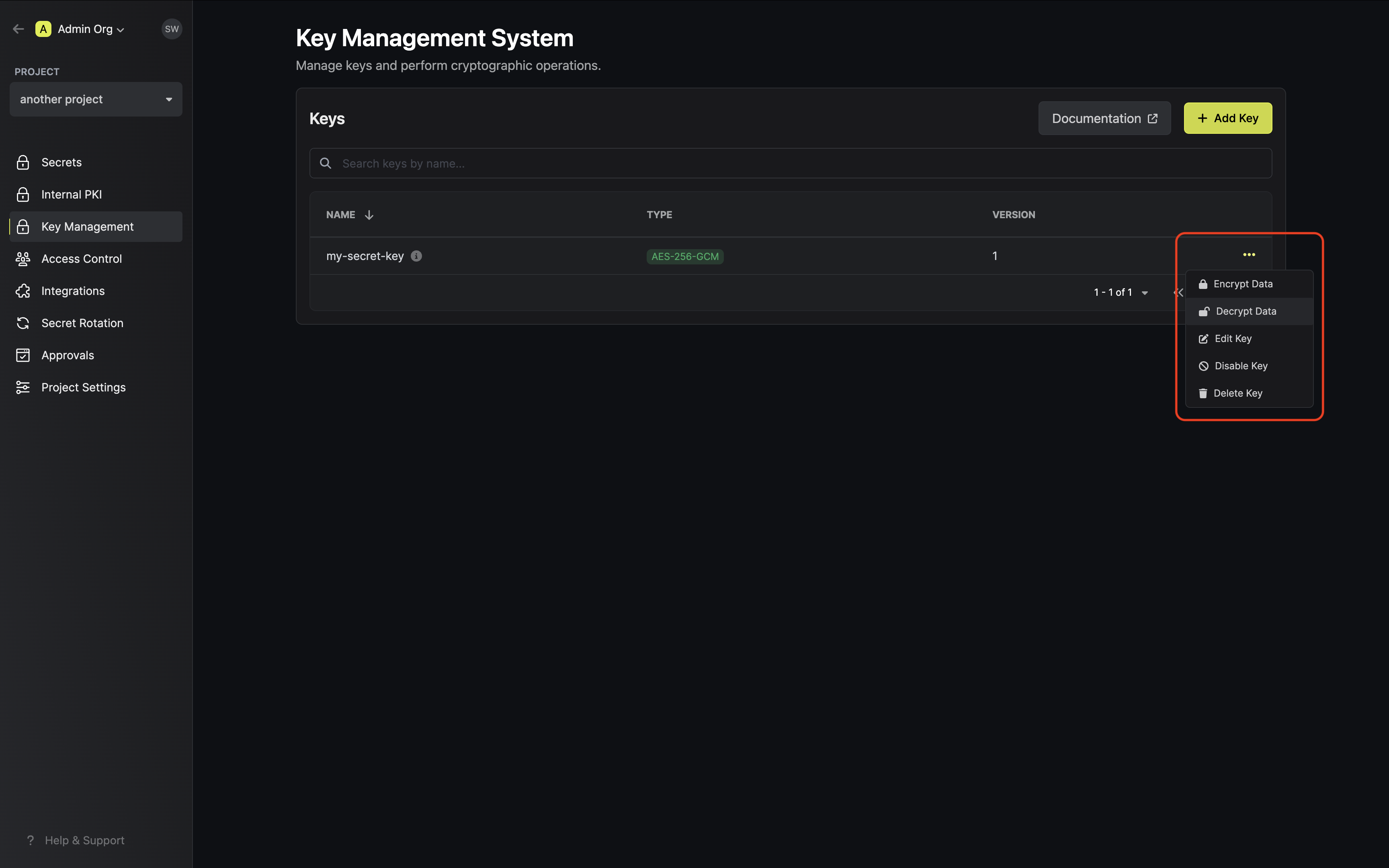

Signing
Guide to Signing Data
In the following steps, we explore how to generate a key and use it to sign data.- Infisical UI
- API
Creating a KMS key
Navigate to Project > Key Management and tap on the Add Key button. Specify your key details. Here’s some guidance on each field:
Specify your key details. Here’s some guidance on each field:
 Specify your key details. Here’s some guidance on each field:
Specify your key details. Here’s some guidance on each field:- Name: A slug-friendly name for the key.
-
Key Usage: The type of key to create (e.g
Encrypt/Decryptfor encryption, andSign/Verifyfor signing). -
Algorithm: The signing algorithm associated with the key (e.g.
RSA_4096). -
Description: An optional description of what the intended usage is for the key.
Signing data with the KMS key
Once your key is generated, open the options menu for the newly created key and select sign data.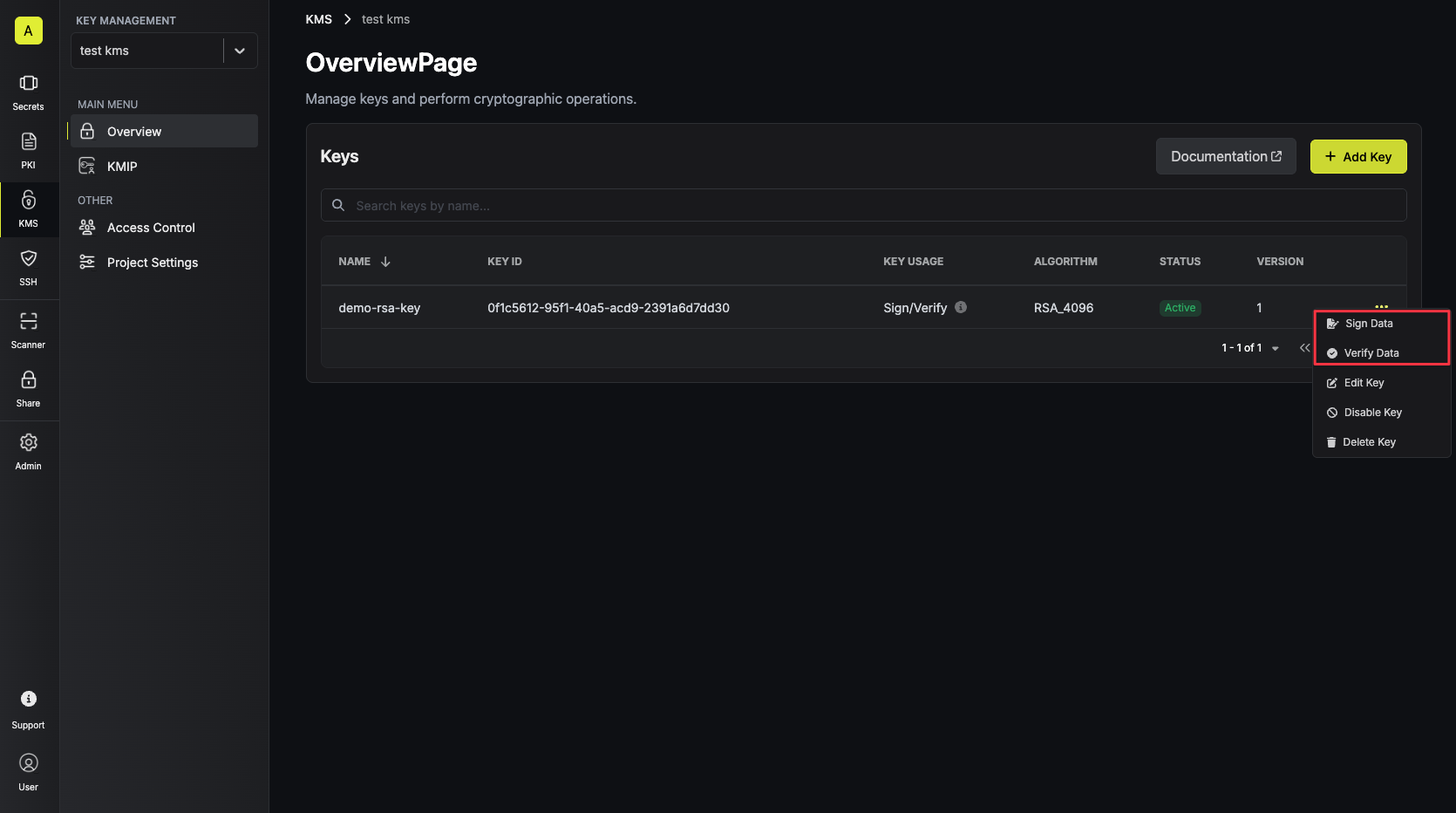 Populate the text area with your data and tap on the Sign button.
Populate the text area with your data and tap on the Sign button.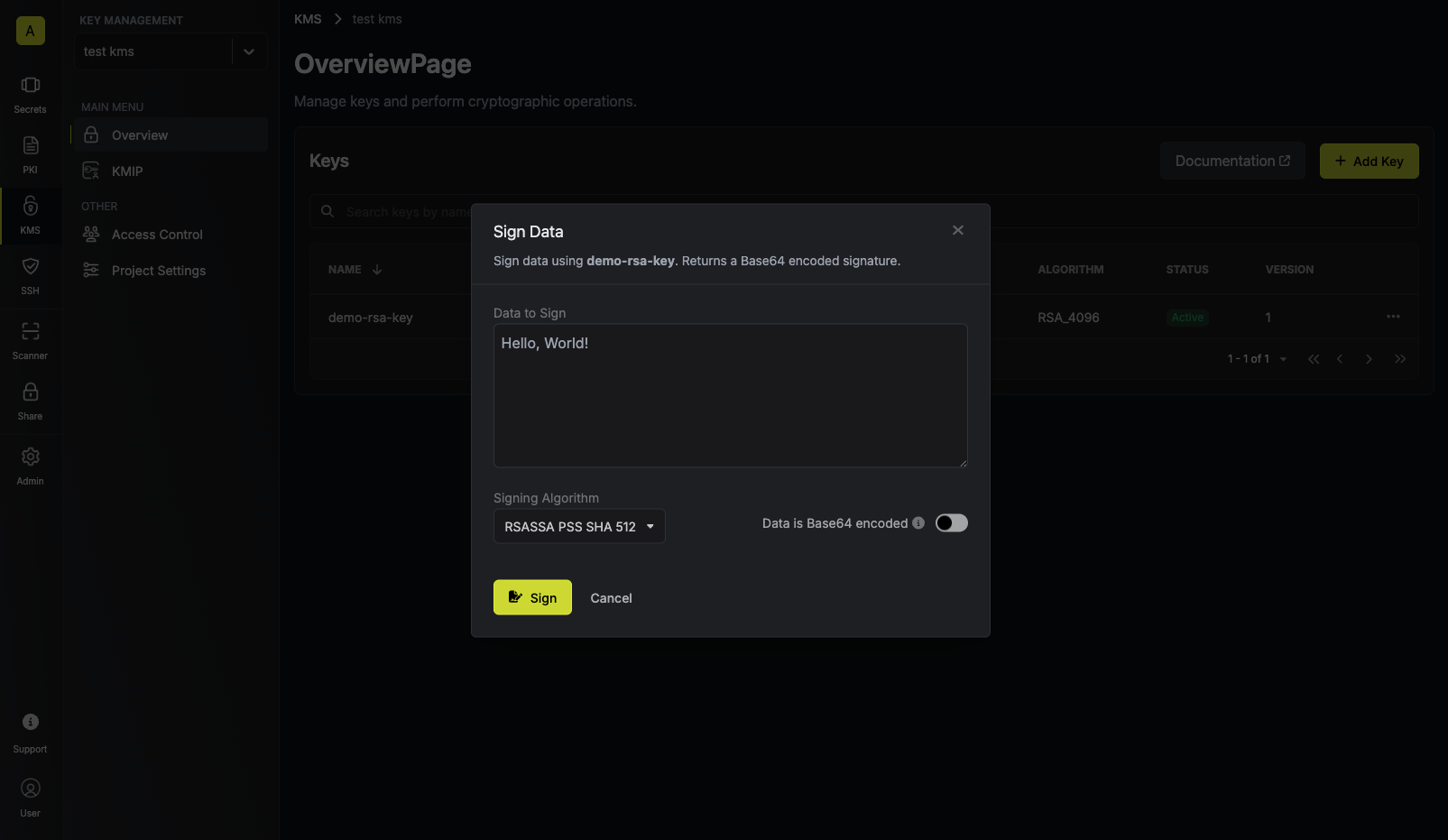 Make sure to select the appropriate signing algorithm that will be used to sign the data.
Supported signing algorithms are:For RSA keys:Copy and store the signature of your data.
Make sure to select the appropriate signing algorithm that will be used to sign the data.
Supported signing algorithms are:For RSA keys:Copy and store the signature of your data.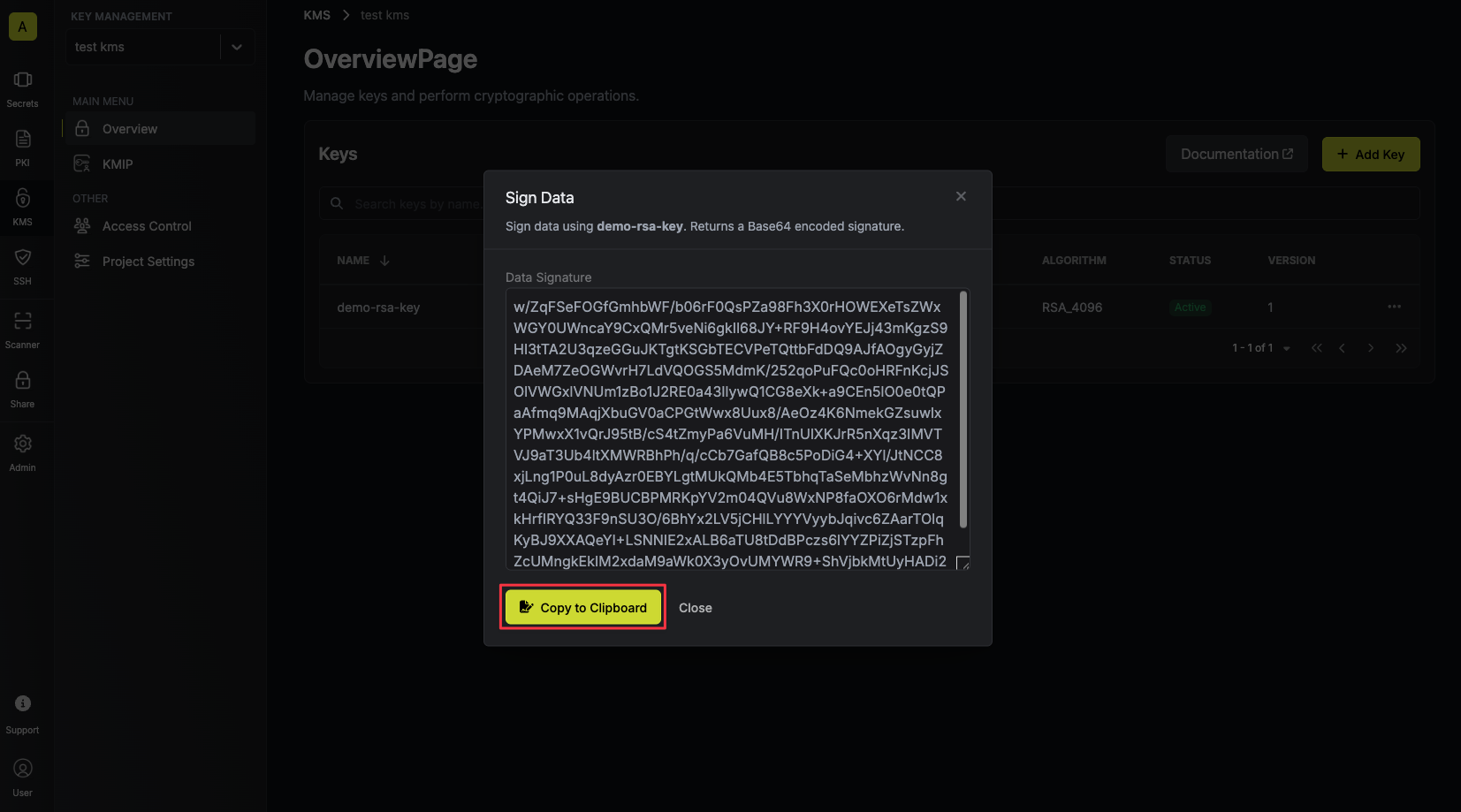
 Populate the text area with your data and tap on the Sign button.
Populate the text area with your data and tap on the Sign button. Make sure to select the appropriate signing algorithm that will be used to sign the data.
Supported signing algorithms are:For RSA keys:
Make sure to select the appropriate signing algorithm that will be used to sign the data.
Supported signing algorithms are:For RSA keys:RSASSA PSS SHA 512: Not deterministic, and includes random salt.RSASSA PSS SHA 384: Not deterministic, and includes random salt.RSASSA PSS SHA 256: Not deterministic, and includes random salt.RSASSA PKCS1 V1.5 SHA 512: Deterministic, and does not include randomness.RSASSA PKCS1 V1.5 SHA 384: Deterministic, and does not include randomness.RSASSA PKCS1 V1.5 SHA 256: Deterministic, and does not include randomness.
ECDSA SHA 512: Not deterministic, and includes randomness.ECDSA SHA 384: Not deterministic, and includes randomness.ECDSA SHA 256: Not deterministic, and includes randomness.
RSASSA PSS SHA 512 signing algorithm.If your data is already Base64 encoded make sure to toggle the respective switch on to avoid
redundant encoding.

Guide to Verifying Data
In the following steps, we explore how to verify data using an existing key in Infisical KMS.- Infisical UI
- API
Accessing your key
Navigate to Project > Key Management and open the options menu for the key used to sign the data
you want to verify.

Verifying data with the KMS key
Paste your signature and data into the text areas and tap on the Verify button.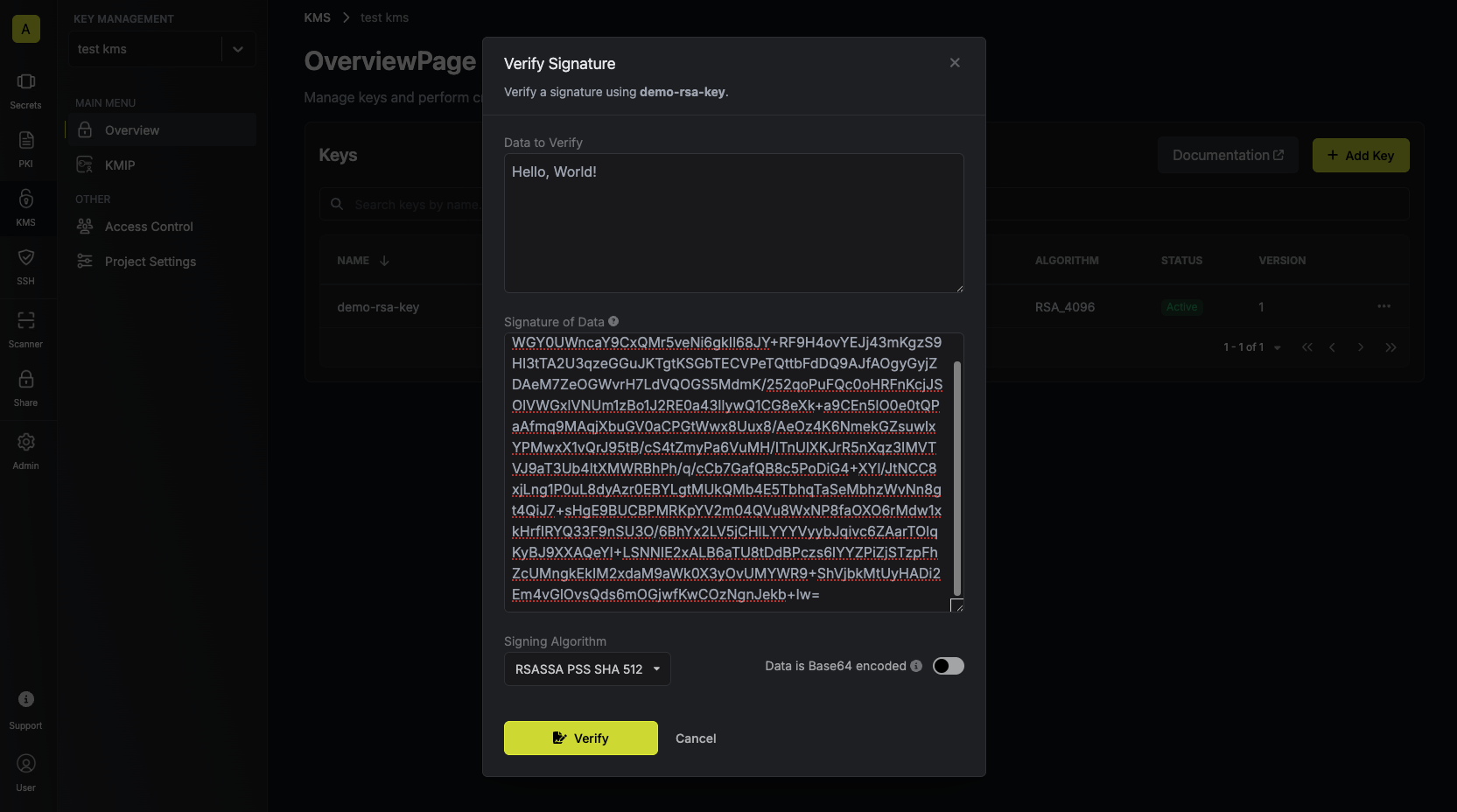 Your verification result will be displayed and can be copied for use.
Your verification result will be displayed and can be copied for use.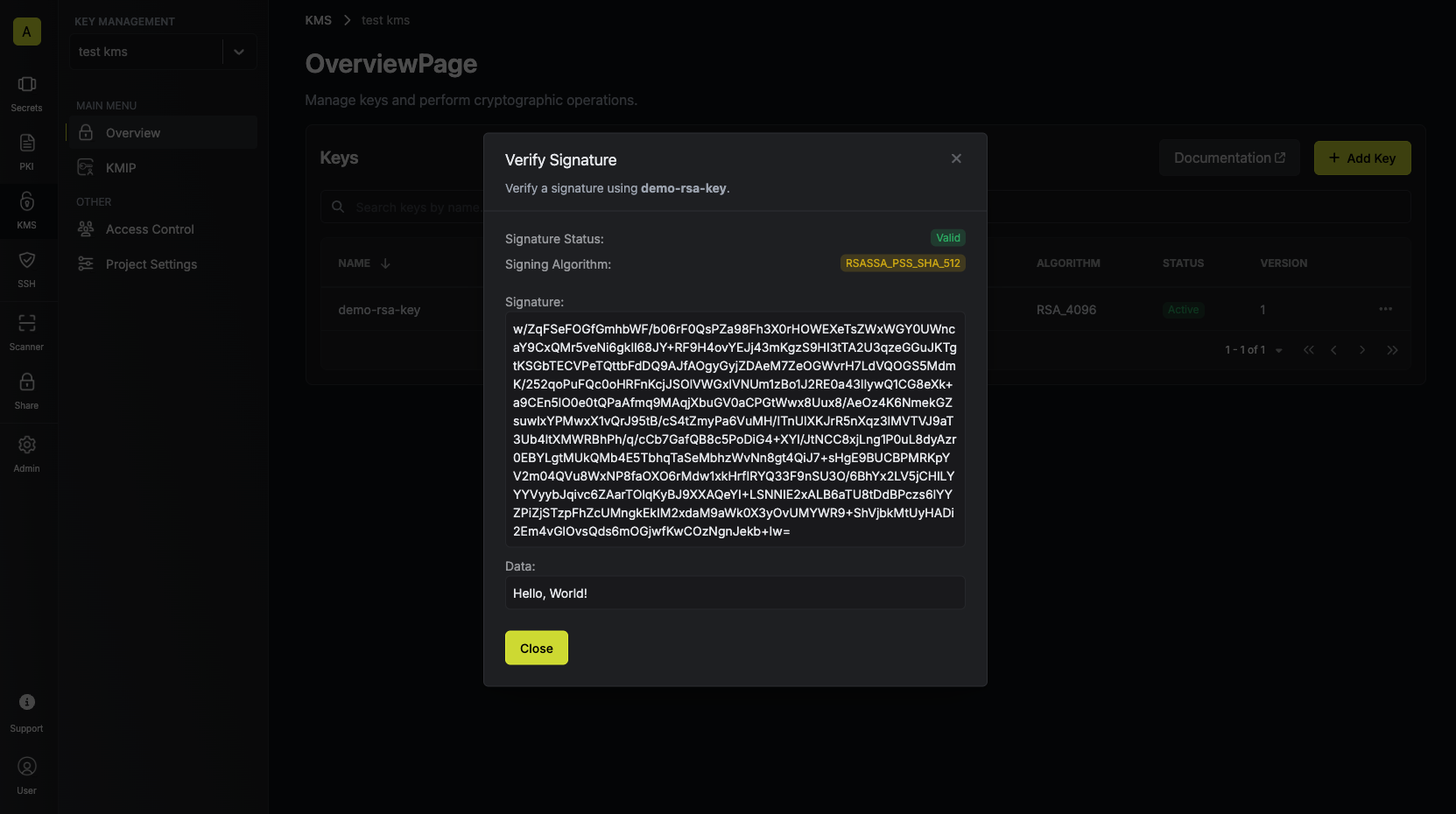 If the signature is invalid, you’ll see an error message indicating that the signature is invalid, and the “Signature Status” field will be
If the signature is invalid, you’ll see an error message indicating that the signature is invalid, and the “Signature Status” field will be
 Your verification result will be displayed and can be copied for use.
Your verification result will be displayed and can be copied for use. If the signature is invalid, you’ll see an error message indicating that the signature is invalid, and the “Signature Status” field will be
If the signature is invalid, you’ll see an error message indicating that the signature is invalid, and the “Signature Status” field will be Invalid.FAQ
Is my data stored in Infisical KMS?
Is my data stored in Infisical KMS?
No. Infisical’s KMS only provides cryptographic services and does not store
any encrypted or decrypted data.
Can key material be accessed outside of Infisical KMS?
Can key material be accessed outside of Infisical KMS?
No. Infisical’s KMS will never expose your keys, encrypted or decrypted, to
external sources.
What algorithms does Infisical KMS support?
What algorithms does Infisical KMS support?
Currently Infisical supports 4 different key algorithms with different purposes:
-
RSA_4096: For signing and verifying data. -
ECC_NIST_P256: For signing and verifying data. -
AES-256-GCM: For encryption and decryption operations. -
AES-128-GCM: For encryption and decryption operations.
How do I sign and verify a digest using the Infisical KMS?
How do I sign and verify a digest using the Infisical KMS?
To sign and verify a digest using the Infisical KMS, you can use the
Sign and Verify endpoints respectively.
You will need to pass "isDigest": true in the request body to indicate that you are signing or verifying a digest.
The data you are signing or verifying will need to be a base64 encoded digest of the data you wish to sign or verify.
It’s important that the digest is created using the same hashing algorithm as the signing algorithm. As an example, you would create the digest with SHA512 if you are using the RSASSA_PKCS1_V1_5_SHA_512 signing algorithm.To create a SHA512 digest of your data, you can use the following command with OpenSSL:Sample request for signing a digest
Request
Sample response for signing a digest
Response
Sample request for verifying a digest
Request
Sample response for verifying a digest
Response
Please note that
RSA PSS signing algorithms are not supported for digest signing and verification. Please use RSA PKCS1 V1.5 signing algorithms for digest signing and verification, or ECDSA if you’re using an ECC key.