In the world of cybersecurity, managing secrets and credentials securely is crucial. AWS Secrets Manager is one of the secret management solutions used by many organizations. However, there are other alternatives available that might fit your organization's requirements better. This articles describes some common alternatives to AWS Secrets Manager:
1. Infisical
Infisical (that's us 👋) is an open source secret management platform. It provides an end-to-end set of tools that cover all aspects of secret management: from secure version-controled secret storage, to secret rotation, to integrations across infrastructure, certificate lifecycle management, to secret scanning and leak prevention.
Infisical is a popular developer tool with over 12,700 GitHub stars. It is widely adopted by Fortune 500 enterprises, fastest growing startups, and international governments.
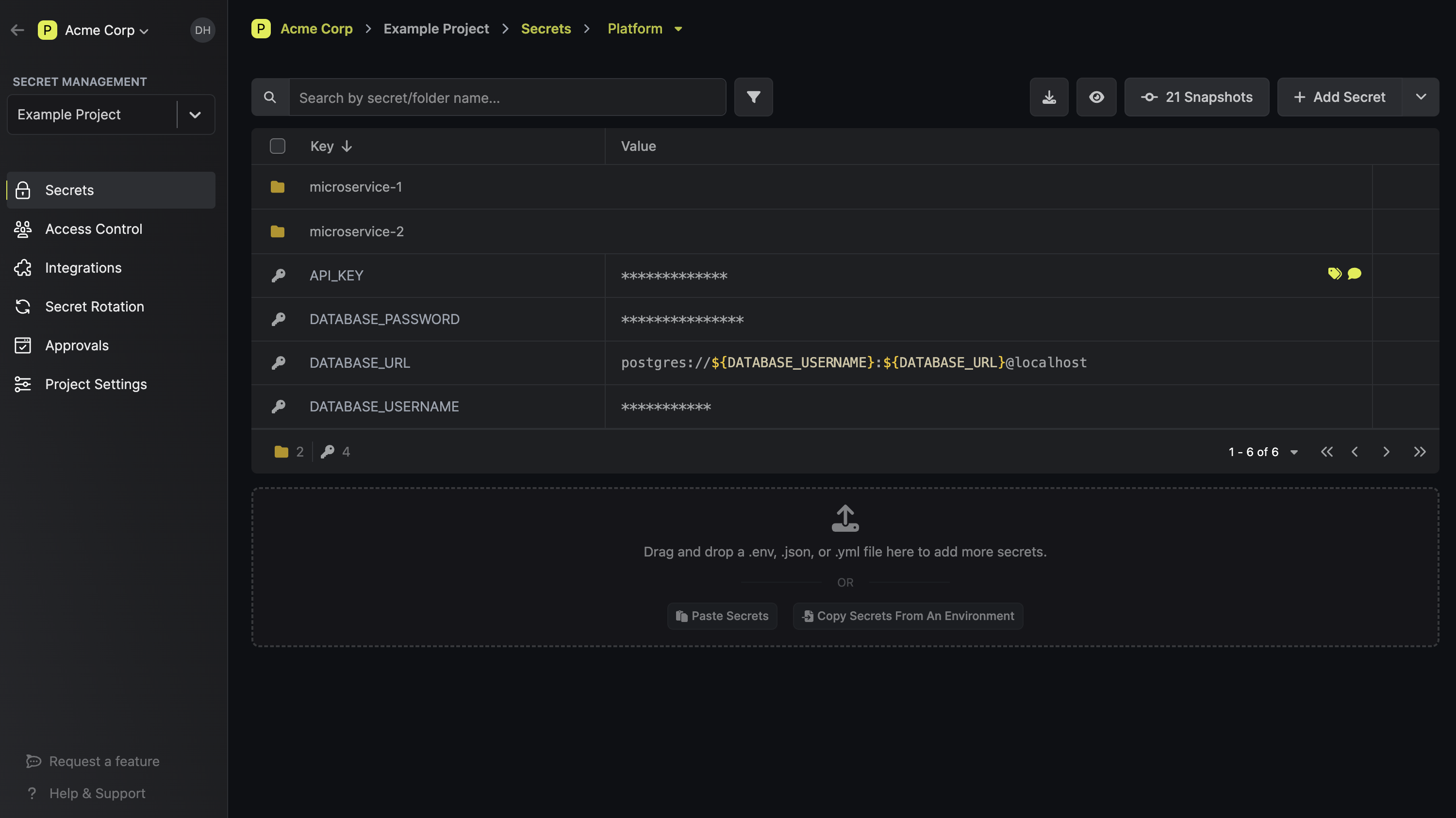
Key features
Compared to AWS Secrets Manager, Infisical has a more advanced feature set. Infisical's main product directions include:
-
Secret Management: Manage secrets securely and efficiently across your infrastructure. Integrate with development, CI/CD, and production envirionments.
-
Dynamic Secret Management: Automatically generate and rotate secrets based on specified settings. Works with all major databases.
-
Certificate Lifecycle Management (PKI): Create Private CA hierarchies and issue X.509 certificates.
-
Secret Scanning: Automatically detect and prevent any secret leaks to git and other environments. Over 150+ different secret types are supported.
-
Secret Sharing: Generated end-to-end encrypted links based on defined security settings – then share these links safely within or outside of your organizations.
How does Infisical compare to AWS Secrets Manager?
Given Infisical's main focus, it offers a wider collection of tools in the secrets management realm. AWS's portfolio has a wide range of tools for managing infrastructure, but its Secrets Manager offering lacks certain functionality that is commonly needed by developers and organizations.
| Infisical | AWS Secrets <br/>Manager | |
|---|---|---|
| Open Source <br/> Audit code, contribute to roadmap, and build integrations | ✅ | ❌ |
| Self-hostable <br/> Host on your own infrastructure (if required) | ✅ | ❌ |
| Self-serve Upgrade <br/> Free to try, no mandatory sales calls | ✅ | ✅ |
| Dynamic Secrets and Rotation <br/> Automatically rotate database access tokens and more | ✅ | ❌ (only custom) |
| Integrations and Ecosystem <br/> Seamlessly integrate with existing tools in your ecosystem | ✅ | ✅ (often external) |
| Developer Workflows <br/> Self-serve secrets with Approval Workflows, Access Requests, etc. | ✅ | ❌ |
| Secret Scanning <br/> Automatically identify secret leaks to Git and other systems | ✅ | ❌ |
| Secret Sharing <br/> Share secrets secure among people in and outside of your organization | ✅ | ❌ |
| Governance <br/> Audit logs, roles-based access, permissions | ✅ | ✅ |
| Developer Community <br/> Wide developer adoption across the world for better reliability and support | ✅ | ✅ |
Why do companies choose Infisical?
There are a few main reasons for that:
- It's many tools in one: Infisical can cover full secret management lifecycle in a single tool. In addition, Infisical provides a wide range of integrations with 99+% of leading developer and infrastructure tools.
- Self-hosting: Infisical is able to satisfy the needs of the most security-oriented enterprises by providing both Self-hosted and managed Cloud-hosted options.
- Pricing is transparent and scaleable: Many organizations appreciate Infisical's affordability and that pricing scales as they grow. There's a generous free tier they can use forever.
- Focus on Developer Experience: Centralized secrets management is meant to save many developer hours. Infisical is able to achieve this goal by providing great developer experience tested by 10,000s of developers across the globe.
2. HashiCorp Vault
HashiCorp Vault and HashiCorp Vault Enterprise are a solution designed to fight secret sprawl and integrate with DevOps methodologies, enabling businesses to continuously deliver new applications and functionalities without compromising on security. It is focused on managing application identities and providing secure access to cloud resources.
How does HashiCorp Vault compare to AWS Secrets Manager?
HashiCorp Vault boasts a much larger developer community around its product compared to AWS Secrets Manager – which is a significantly simpler tool.
One of the benefits of AWS Secrets Manager is that, unlike Vault Enterprise, it does not require talking to sales to make the purchase (and it is not as costly). Otherwise, HashiCorp Vault provides much more advanced functionality for each of the categories defined below:
| HashiCorp <br/> Vault | AWS Secrets <br/>Manager | |
|---|---|---|
| Open Source <br/> Audit code, contribute to roadmap, and build integrations | ✅ | ❌ |
| Self-hostable <br/> Host on your own infrastructure (if required) | ✅ | ❌ |
| Self-serve Upgrade <br/> Free to try, no mandatory sales calls | ❌ | ✅ |
| Dynamic Secrets and Rotation <br/> Automatically rotate database access tokens and more | ✅ | ❌ (only custom) |
| Integrations and Ecosystem <br/> Seamlessly integrate with existing tools in your ecosystem | ✅ | ✅ (often external) |
| Developer Workflows <br/> Self-serve secrets with Approval Workflows, Access Requests, etc. | ❌ | ❌ |
| Secret Scanning <br/> Automatically identify secret leaks to Git and other systems | ✅ | ❌ |
| Secret Sharing <br/> Share secrets secure among people in and outside of your organization | ❌ | ❌ |
| Governance <br/> Audit logs, roles-based access, permissions | ✅ | ✅ |
| Developer Community <br/> Wide developer adoption across the world for better reliability and support | ✅ | ✅ |
Why do companies choose HashiCorp Vault?
There are a few main aspects of HashiCorp Vault that users appreciate:
- Security: HashiCorp Vault provides a large number of security configurations for the most advanced a security-focused organizations.
- Automations: HashiCorp Vault provides a very wide range of automations for integrating secret management workflows across infrastructure, managing certificates, rotating secret values, and more.
- Availability: High uptime and reliability are critical for secrets management. HashiCorp Vault is able to provide high availability (HA) setup for both self-hosted and cloud-managed environments.
3. Azure Key Vault
Azure Key Vault is a native secrets management solution provided by Azure. It is a fairly simplistic solution, but it might be able to satisfy the needs of certain organizations.
How does Azure Key Vault comapre to AWS Secrets Manager?
AWS Secrets Manager is technically very similar to Azure Key Vault – besides the fact that it integrates better with Azure than AWS. On the other hand, it is a more popular solution compared to Azure Key Vault. This is primarily due to AWS's great distribution and simple integration with other AWS tools.
| Azure Key <br/>Vault | AWS Secrets <br/>Manager | |
|---|---|---|
| Open Source <br/> Audit code, contribute to roadmap, and build integrations | ❌ | ❌ |
| Self-hostable <br/> Host on your own infrastructure (if required) | ❌ | ❌ |
| Self-serve Upgrade <br/> Free to try, no mandatory sales calls | ✅ | ✅ |
| Dynamic Secrets and Rotation <br/> Automatically rotate database access tokens and more | ❌ (only custom) | ❌ (only custom) |
| Integrations and Ecosystem <br/> Seamlessly integrate with existing tools in your ecosystem | ✅ (often external) | ✅ (often external) |
| Developer Workflows <br/> Self-serve secrets with Approval Workflows, Access Requests, etc. | ❌ | ❌ |
| Secret Scanning <br/> Automatically identify secret leaks to Git and other systems | ❌ | ❌ |
| Secret Sharing <br/> Share secrets secure among people in and outside of your organization | ❌ | ❌ |
| Governance <br/> Audit logs, roles-based access, permissions | ✅ | ✅ |
| Developer Community <br/> Wide developer adoption across the world for better reliability and support | ✅ | ✅ |
Why do companies choose Azure Key Vault?
There are mainly 2 reasons for choosing Azure Key Vault:
- Ease of starting out: Azure Key Vault is easy to get started if your organization is already heavily using Azure. That is, you might already have budget allocated to Azure and may not need an approval for adopting a new Azure-provided tool.
- Integrations with Azure: If you are utilizing only Azure tools across infrastructure, it might make sense to use Azure-native integrations of Key Vault. A common exception from this is CI/CD tooling.
4. Building In-House Secret Management Tools
In the realm of secrets management, organizations often face the decision of choosing between off-the-shelf solutions like Infisical or Vault and developing an in-house secrets management platform tailored to their specific needs. In the past decade, organizations like Lyft, Pinterest, and Segment have committed to building out their own solutions. While this option can offer high customization, it comes with its own set of challenges and considerations.

Pros of Building an In-House Secrets Management Solution
-
Customization: The most significant advantage of an in-house solution is the ability to tailor it precisely to your infrastructure and operational needs. This customization can result in a system that aligns perfectly with your existing workflows, systems, and security policies.
-
Control Over Updates and Changes: With an in-house system, you have complete control over when and how the system is updated or changed. This can be crucial for organizations operating in highly regulated industries or those with strict internal control requirements.
Cons of Building an In-House Secrets Management Solution
-
Resource-Intensive Development: Developing a secrets management solution in-house requires significant time investment in design, development, and testing. This process can divert valuable IT and development resources away from other critical projects.
-
Ongoing Maintenance and Support: Post-deployment, the system will require continuous maintenance to ensure its efficiency and security. This includes regular updates, patches, and security checks, all of which demand dedicated staff and resources.
-
Audit and Compliance Challenges: Custom-built systems can face heightened scrutiny from auditors, especially in industries with stringent regulatory standards. Ensuring compliance and passing audits can be more challenging as auditors may not be familiar with the custom system, unlike widely recognized commercial products.
-
Security Expertise Requirement: Building a secure and robust secrets management system requires a high level of security expertise. This includes not just the initial build but also ongoing threat assessment and response capabilities.
-
Lack of External Support: Unlike commercial solutions that come with vendor support, an in-house system lacks external support. This means any issues or challenges must be addressed internally, which can be a significant drawback in case of complex problems.
-
Training for New Employees: A custom solution requires specific training for new employees, which can be more resource-intensive compared to using a standard, widely-used solution where employees might already have some familiarity or where extensive training resources are readily available.
-
Scalability Concerns: As the organization grows, the in-house solution might need significant re-engineering to scale effectively, which can be a resource-intensive process.
Is Infisical right for you?
Here's our (short) sales pitch.
We're biased (obviously), but we think Infisical is a perfect Azure Key Vault replacement if:
- You are looking for a developer-focused solution that will last you many years ahead. With Infisical, you get much more than just a secure key-value storage (e.g., secret scanning, certificate management, secret sharing, and more).
- You value transparency. We're open source and open core under the MIT license.
- You want to try before you buy. Infisical is self-serve with a generous free tier.
Check out our product page and read our documentation to learn more.
If you have any questions or want to schedule a product demo, you can talk to one of our experts.

